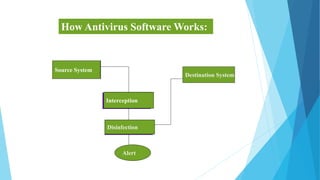
This document provides information about computer viruses and antivirus software. It defines viruses as small programs that spread from computer to computer and interfere with operations. It explains that viruses are often spread through email attachments and downloads. The document then discusses different types of viruses and what to do if a computer has a virus. It defines antivirus software as programs that identify and eliminate viruses. It describes how antivirus software works by maintaining databases of known viruses and scanning files to detect matches. It also explains how antivirus software intercepts files, disinfects infected files, and alerts users. The document provides tips on installing, updating, and using antivirus software effectively.