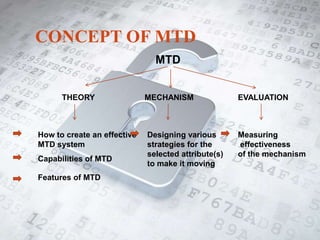
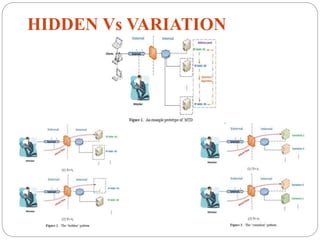
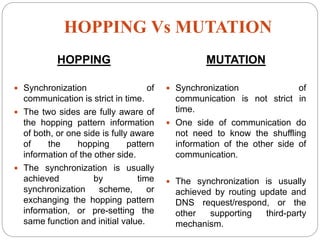
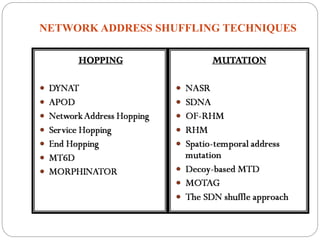
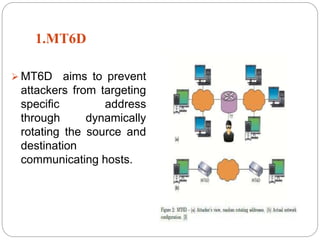
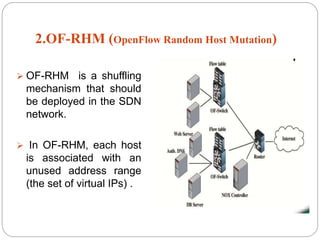
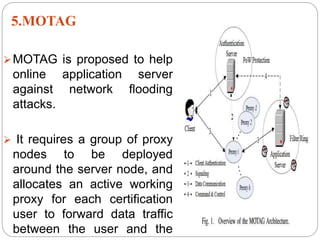
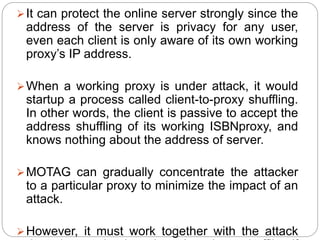
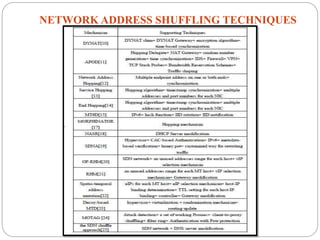
This document introduces network address shuffling as a technique of moving target defense (MTD) to enhance cybersecurity. It describes MTD as automatically changing system attributes to make the attack surface unpredictable for adversaries. Network address shuffling specifically aims to periodically change IP addresses and port numbers. The document outlines various techniques for network address shuffling including MT6D, OF-RHM, RHM, and discusses key considerations for implementing an effective and practical shuffling method such as ensuring unpredictability, determining shuffling frequency, and security of the shuffling rules.

















![REFERENCES
[1] Guilin Cai, Baosheng Wang, Xiaofeng Wang, Yulei
Yuan, Sudan Li College of Computer, National University
of Defense Technology, Changsha, China,”An
Introduction to Network Address Shuffling”.
[2] T. E. Carroll, M. Crouse, E. W. Fulp and K. S.
Berenhaut, "Analysis of network address shuffling as a
moving target defense", in Proc of 2014 IEEE
International Conference on Communications (ICC),
2014, pp.701-706.
[3]Y. Liu, W. Peng and J. Su, "A study of IP prefix hijacking
in cloud computing networks", SECURITY AND
COMMUNICATION NETWORKS, vol.7, no.11, pp.2201-
2210. 2014.
[4] D. Evans, A. Nguyen-Tuong, and J. Knight,
“Effectiveness of moving target defenses,” in Moving
Target Defense: Creating Asymmetric Uncertainty for
Cyber Threats, S. Jajodia, A. K. Ghosh, V. Swarup, C.](https://image.slidesharecdn.com/seminar-170125151645/85/AN-INTRODUCTION-TO-NETWORK-ADDRESS-SHUFFLING-34-320.jpg)
