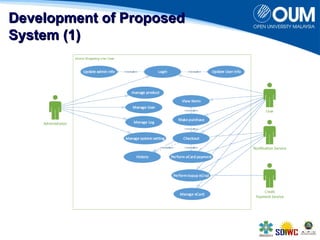
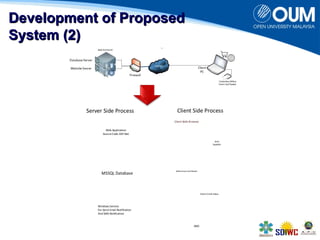
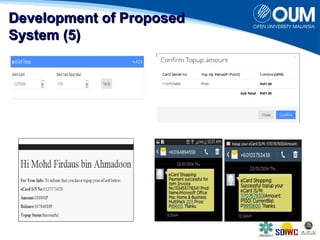
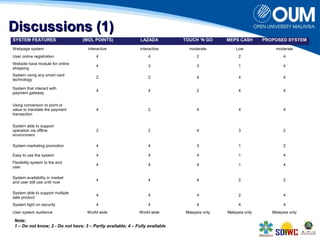
The document proposes a secure online shopping system that utilizes contactless smart cards for transactions, aiming to enhance consumer trust and experience by replacing credit and debit cards. It details the end-to-end process of using the system, development components, and security measures integrated to protect user transactions. The authors discuss the need for improved online shopping security to meet increasing consumer demand for online retail services.



![RReellaatteedd WWoorrkkss
• Payments and transactions in electronic have grown exponentially [Fiallos & Wu, 2005].
• Digital money offers flexible electronic payment with added security features that is required for
transaction, such as replicating the individual activity [Lee, Oh & Lee, 2004]
• Common elements in electronic payment methods are credit card, debit instruments, prepaid
payment services, cumulative collection services, payment portal services and mobile phone
payments [Vassilliou, 2004]
• Electronic payment (e-payment) offers several benefits:
The need to only enter account information for making online payment [Hord, 2005]
Convenient, helps in cost reduction and secured, which translates into reliable online
transactions for purchasing goods or services over the Internet [Humphrey, Pulley & Vesala,
2000]
Automation of payment made electronically contributes to the reduction of the overall cost
for payment system [Appiah and F. Agyemang, 2006].
• Approaches and technologies have been introduced in ensuring the security of electronic
payment via the Internet:
Cryptography is the most common security measures for online payment but slow in speed
and less efficient [Taddesse & Kidan, 2005]
Credit cards with RFID technology is part of mobile phone architecture for secure e-payments
[Venkataramani & Gopalan, 2007].
Use of fingerprint verification technique and steganography for confidence in online
shopping [Ihmaidi, Al-Jaber & Hudaib, 2006]
Speech recognition and encrypted USB device as mechanisms for secured online
transaction [Panigrahy, Jena & Jena, 2010][Lin, Yuan &Qu, 2007].
a new framework that omits hardware deployment at customer’s site for online shopping via
mutual authentication between merchant and customers
[Gupta and R. Johari, 2007]](https://image.slidesharecdn.com/ebw2014paperid118-141015013205-conversion-gate01/85/An-Alternative-of-Secured-Online-Shopping-System-via-Point-Based-Contactless-Smart-Card-4-320.jpg)