This document discusses network readiness and provides information on service level agreements (SLAs), service targets, and ports and protocols. It defines SLAs, describes types of SLAs and their components, and explains the SLA lifecycle. It also discusses factors to consider when setting targets for bandwidth, latency, and packet loss. Finally, it covers common ports used for AV, identifying required ports and protocols, firewalls, and documenting ports and protocols.







![3/28/2013
14
Copyright 2012 by InfoComm International®
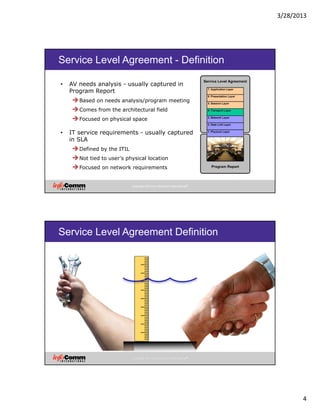
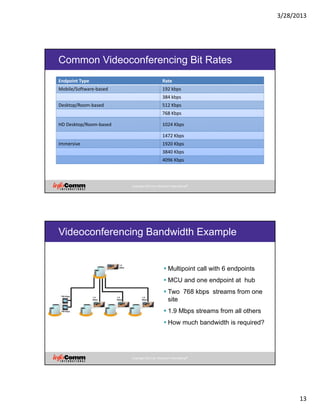
Videoconferencing Bandwidth Example
• Hub Site LAN
• [(0.768 + (0.768 * 0.2)) * 2] + [(1.9 + (1.9 * 0.2)) * 4] =
• [(0.768 + 0.154) * 2] + [(1.9 + 0.4) * 4] =
• [(0.922) * 2] + [(2.3) * 4] =
• 1.844 + 9.2 =
• 11 Mbps
Copyright 2012 by InfoComm International®
Videoconferencing Bandwidth Example
Branch to Hub WAN Spokes
[0.768 + (0.768 * 0.2)] * 2 =
(0.768 + 0.154) * 2 =
0.922 * 2 =
1.844 Mbps
[1.9 + (1.9 * 0.2)] * 1 =
[1.9 + (0.4)] * 1 =
2.3 * 1 =
2.3 Mbps](https://image.slidesharecdn.com/almopro-assessingnetworkreadiness20130325-140310111555-phpapp01/85/Assessing-Network-Readiness-14-320.jpg)