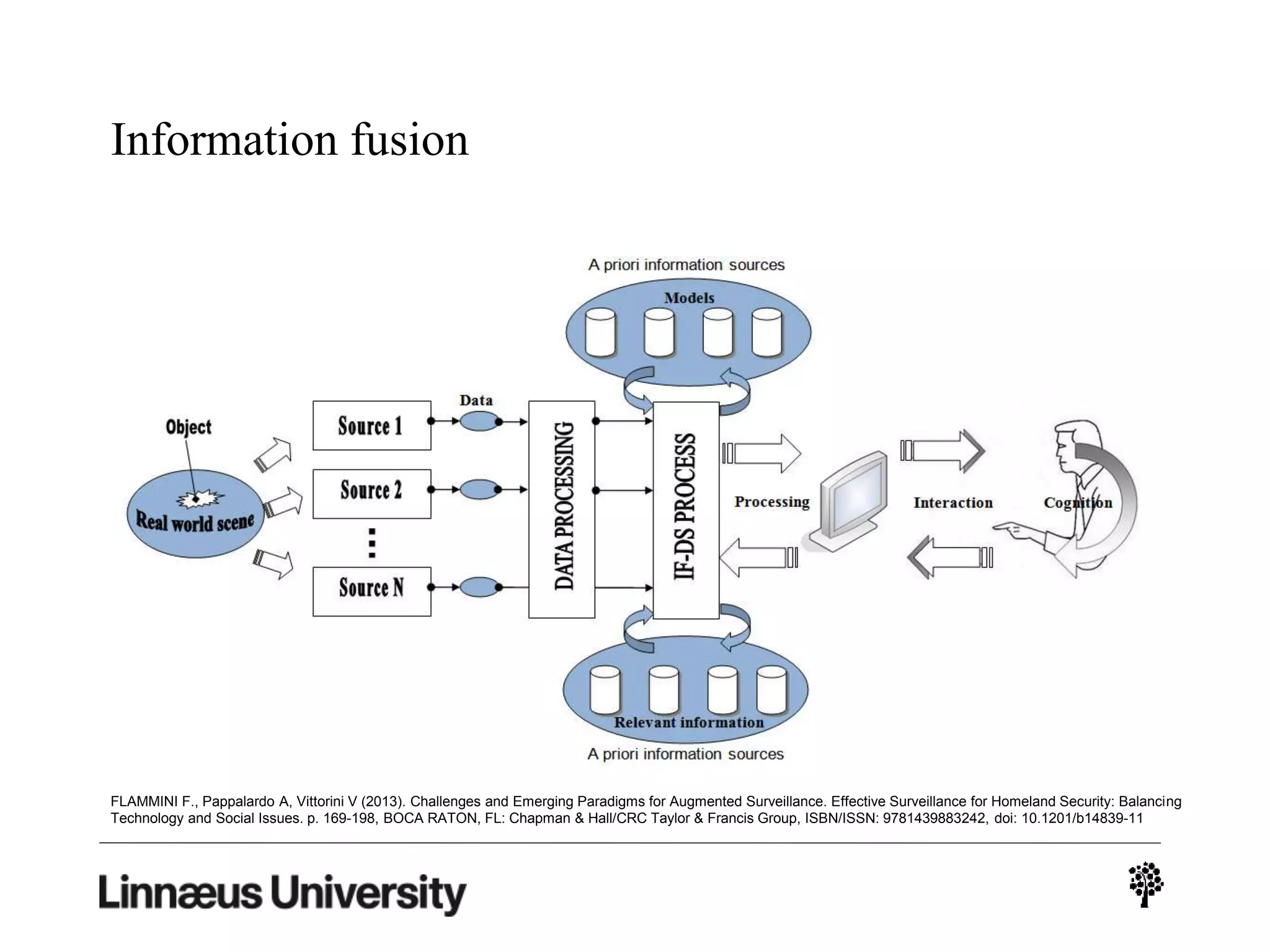
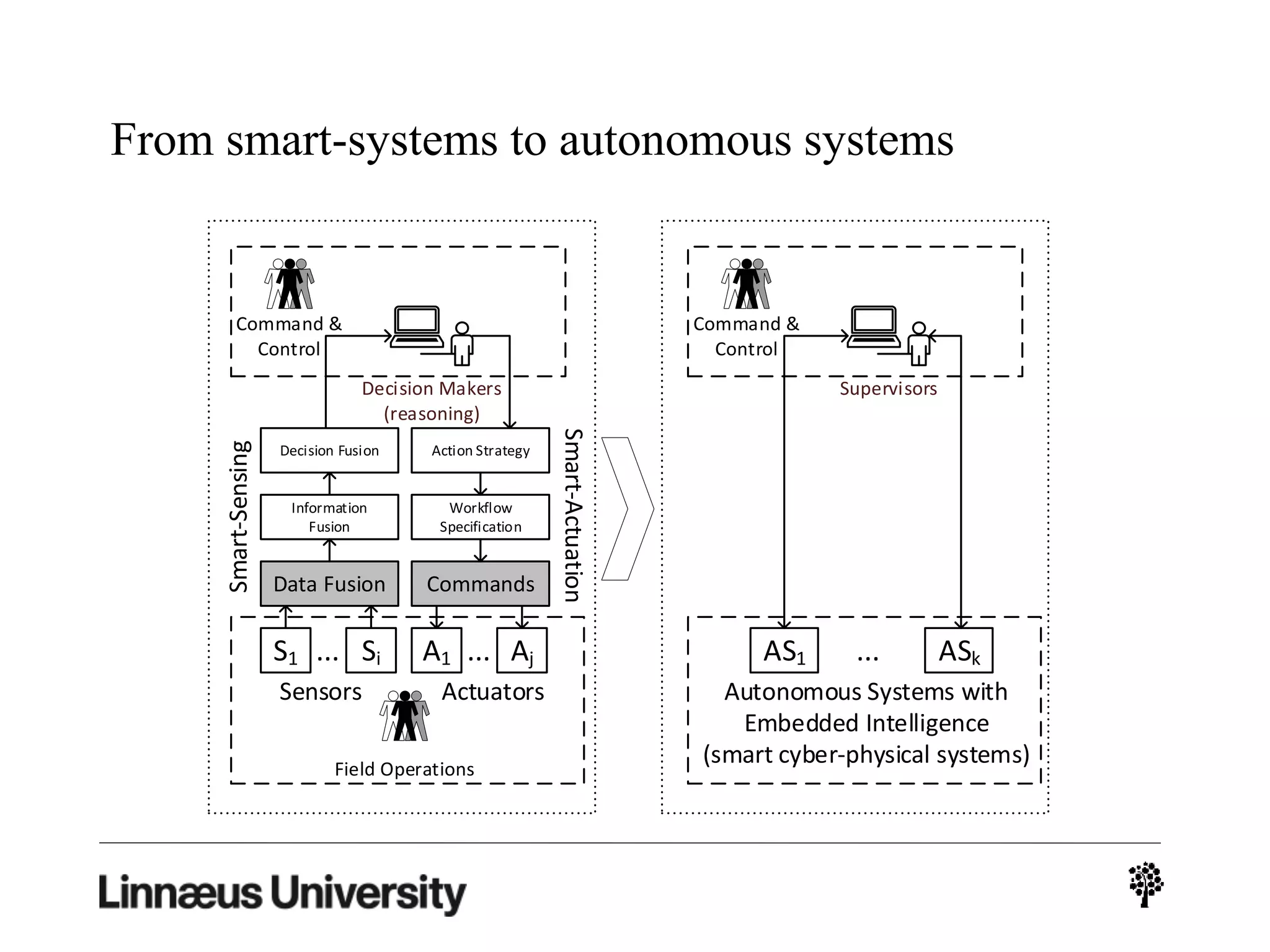
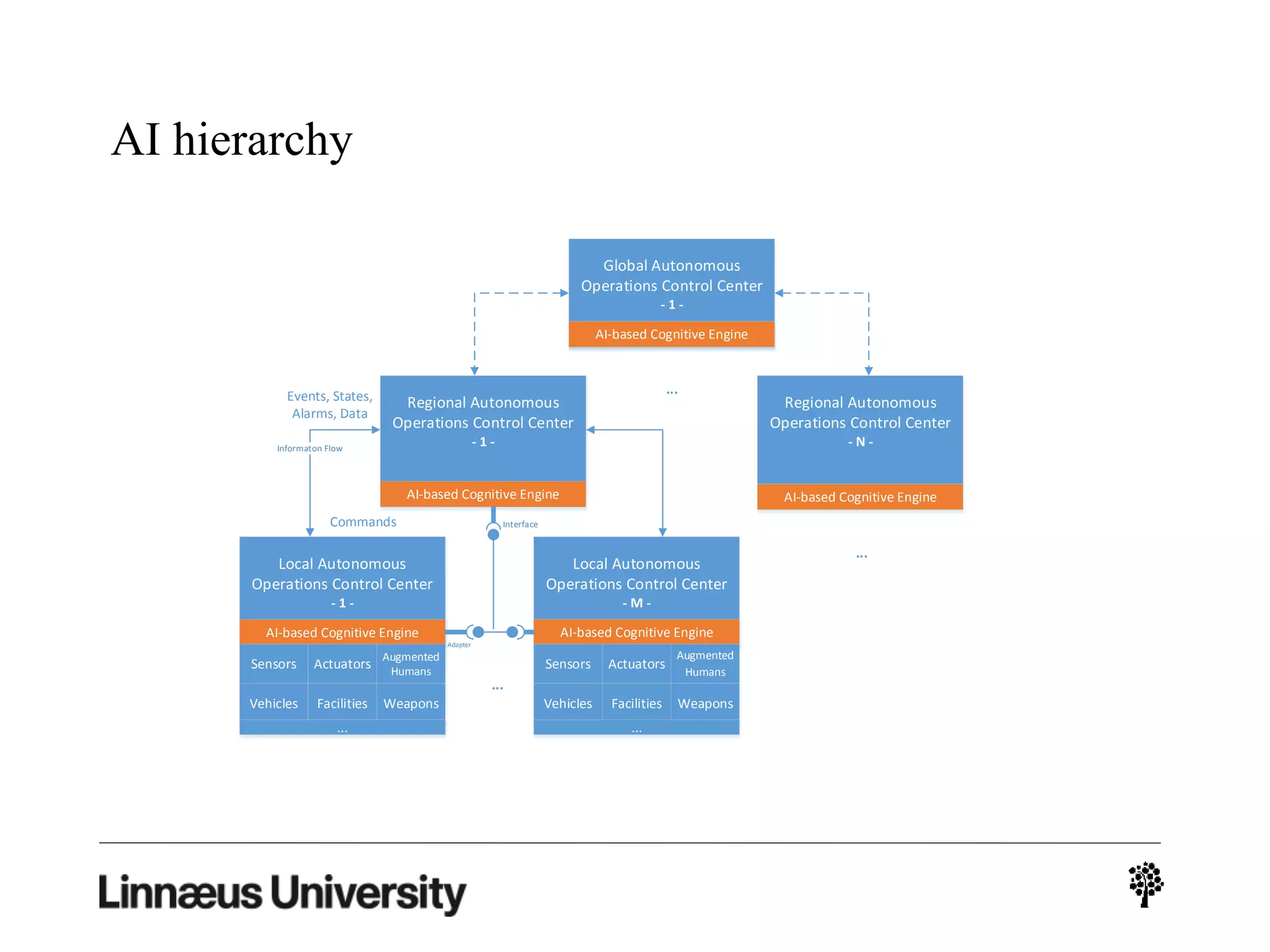
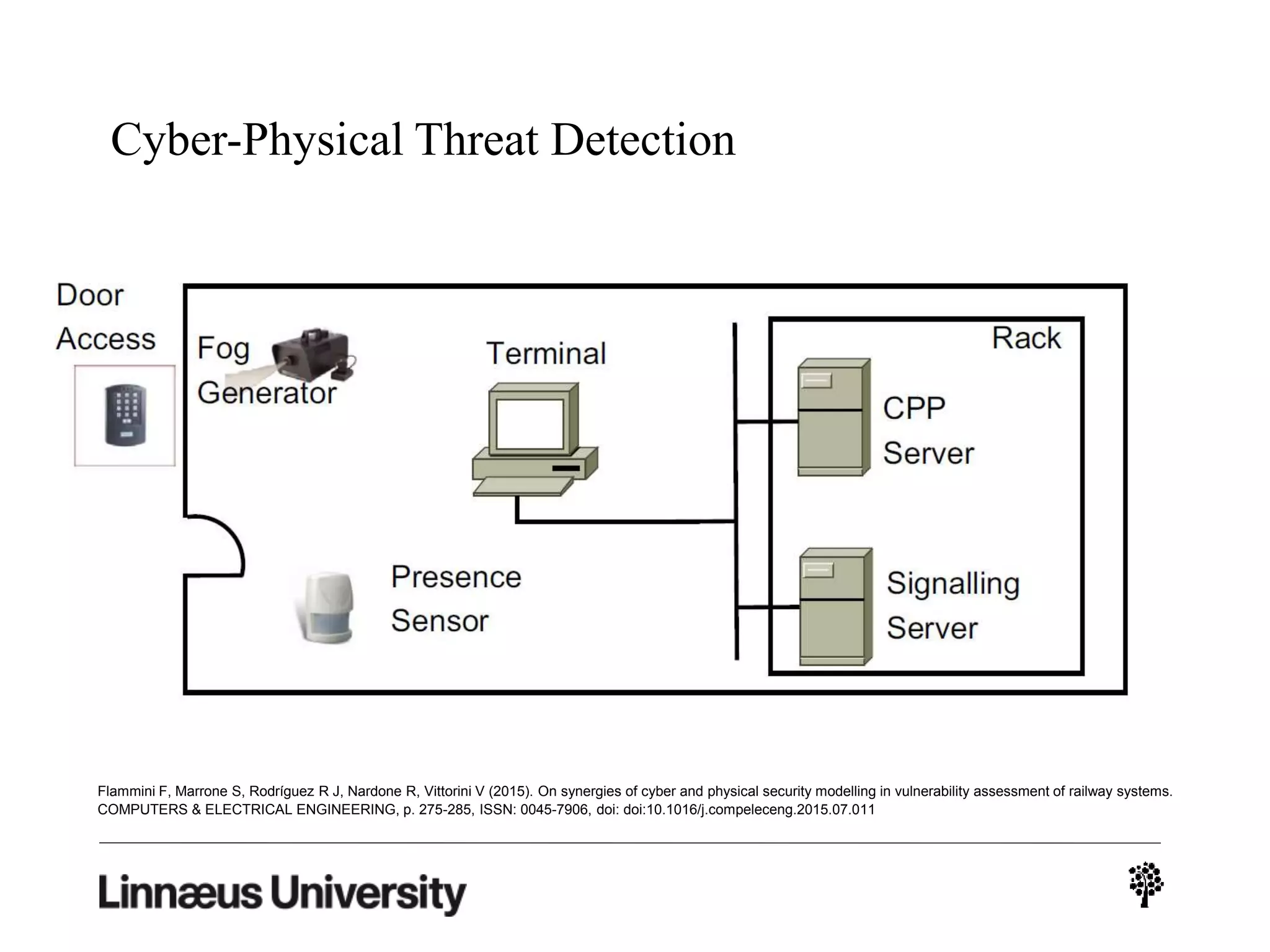
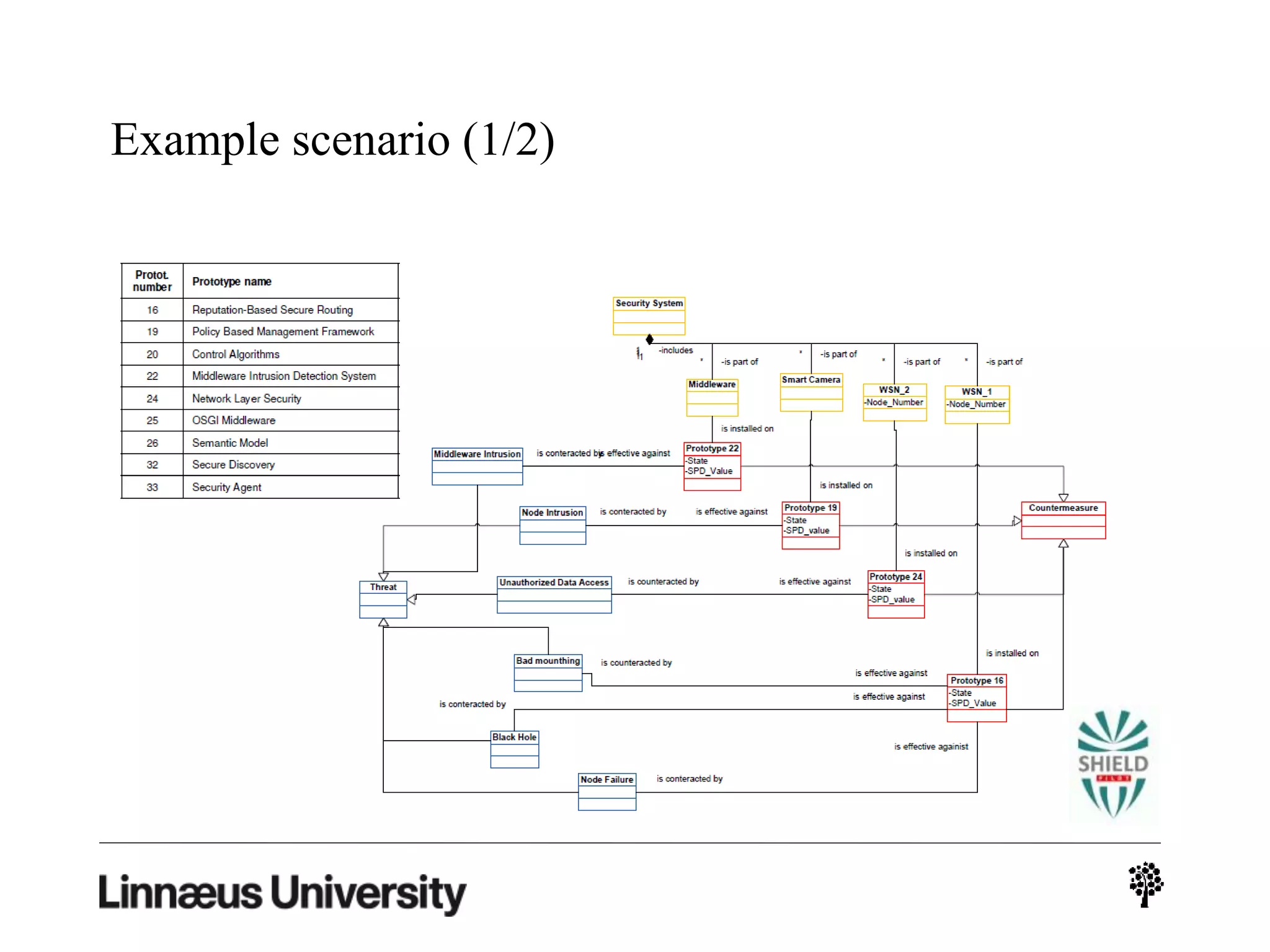
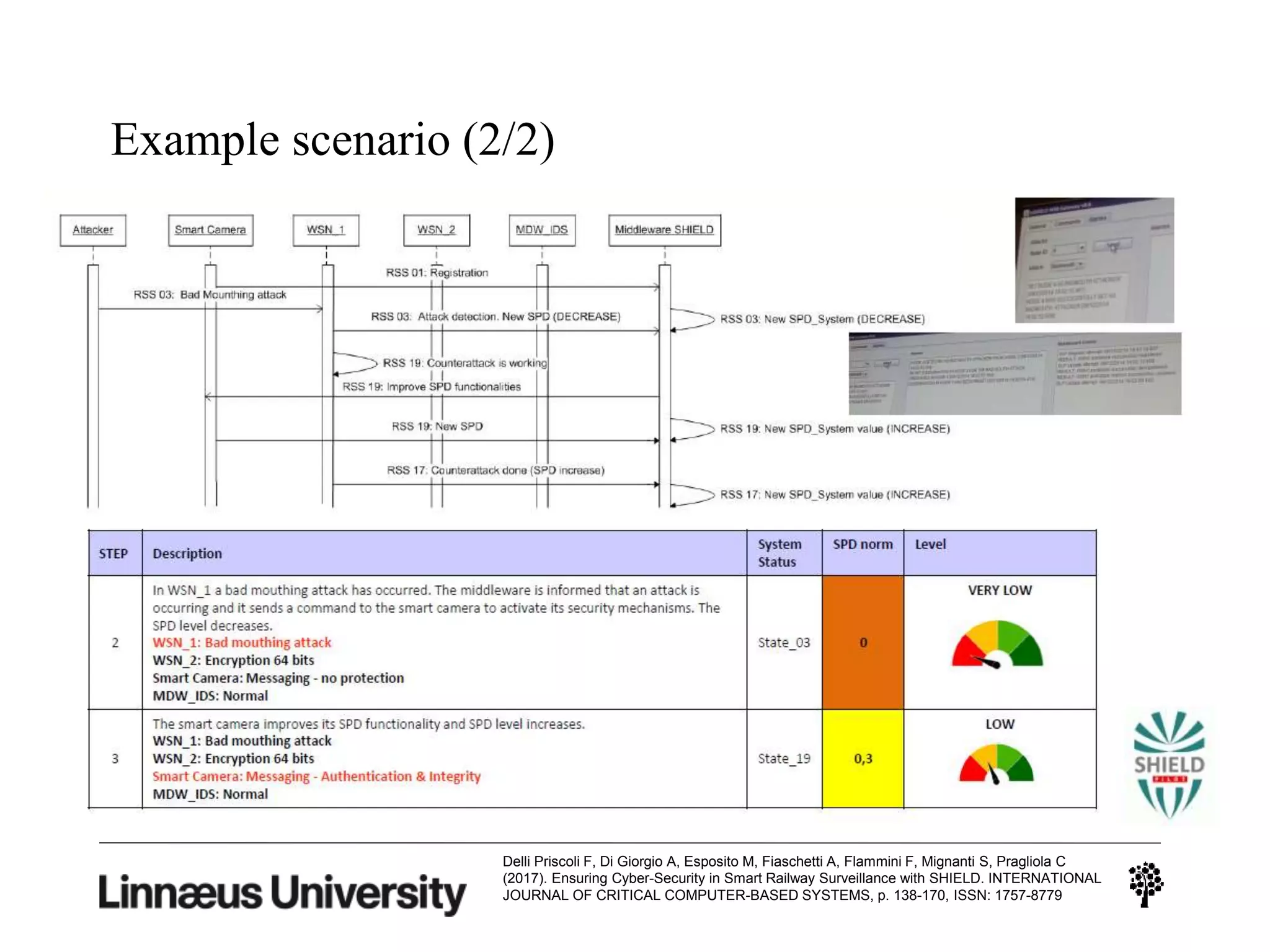
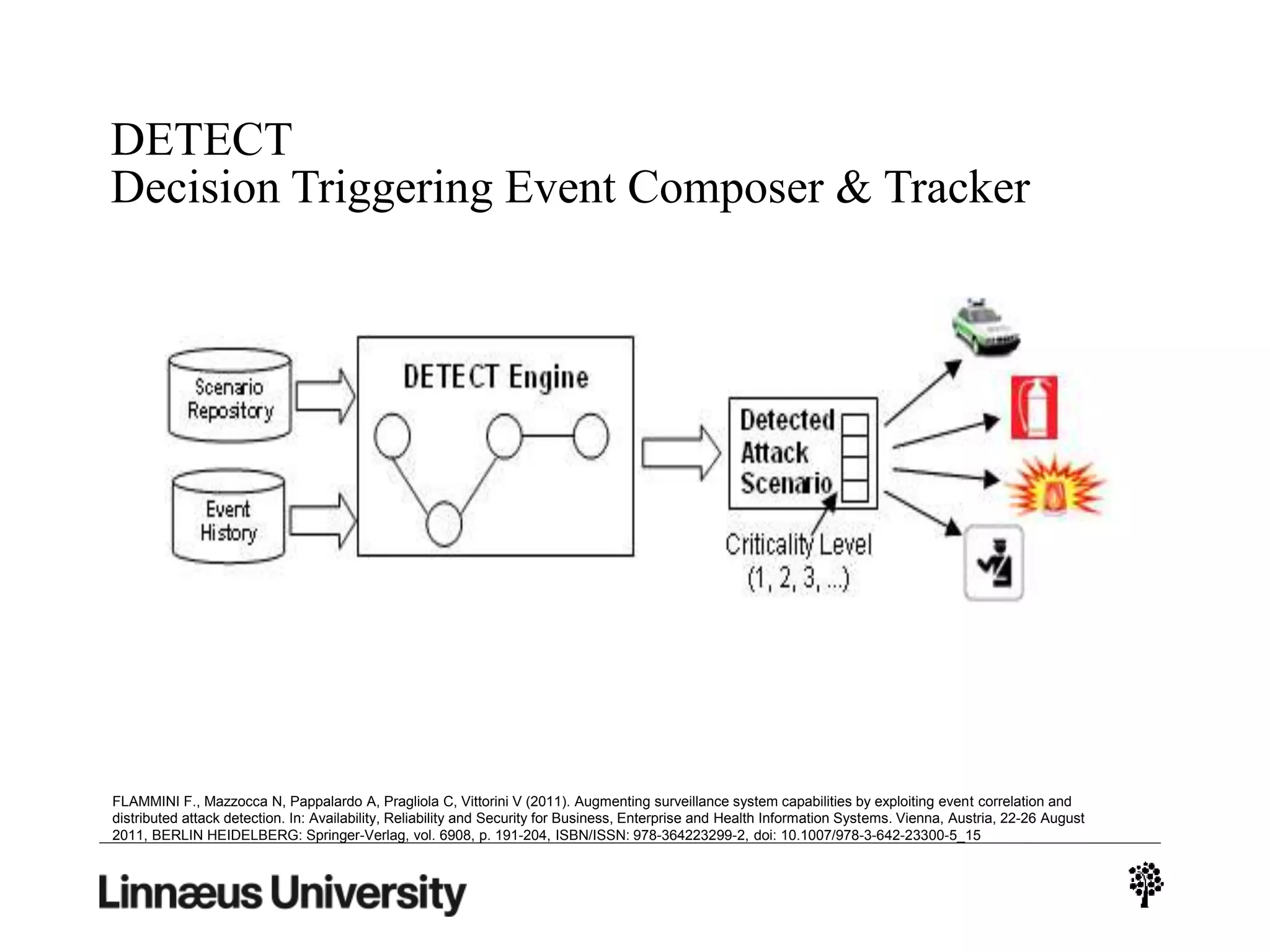
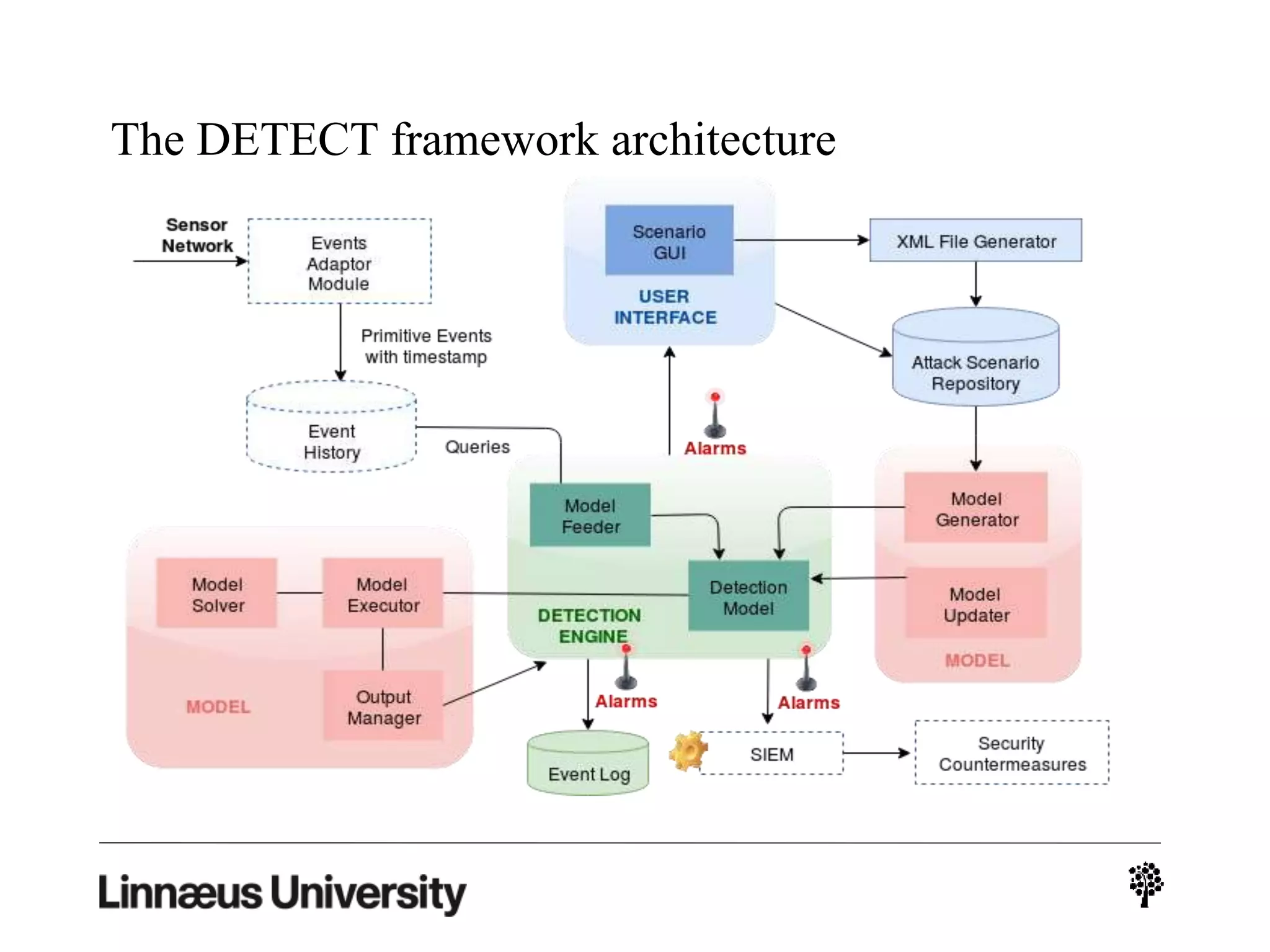
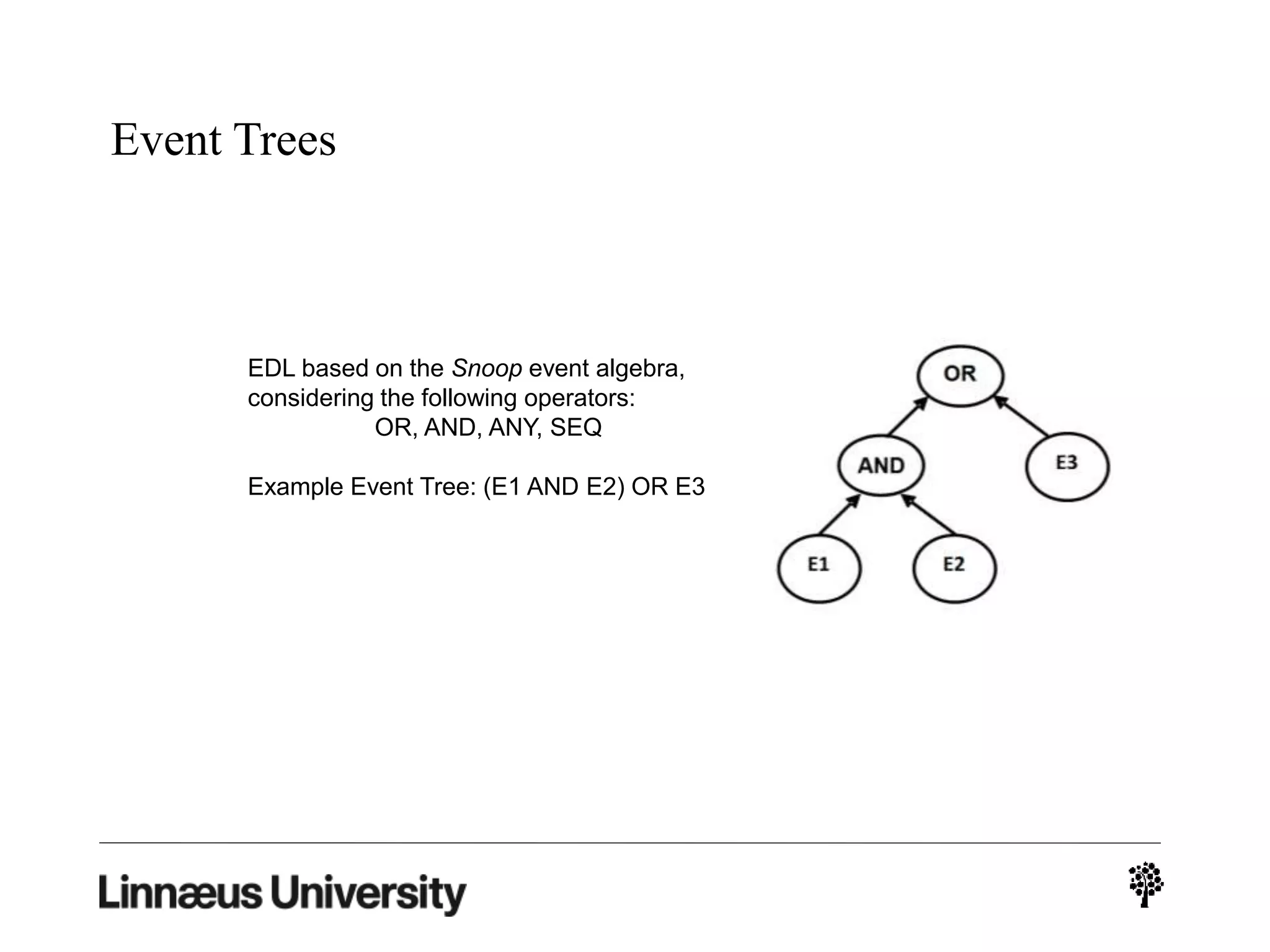
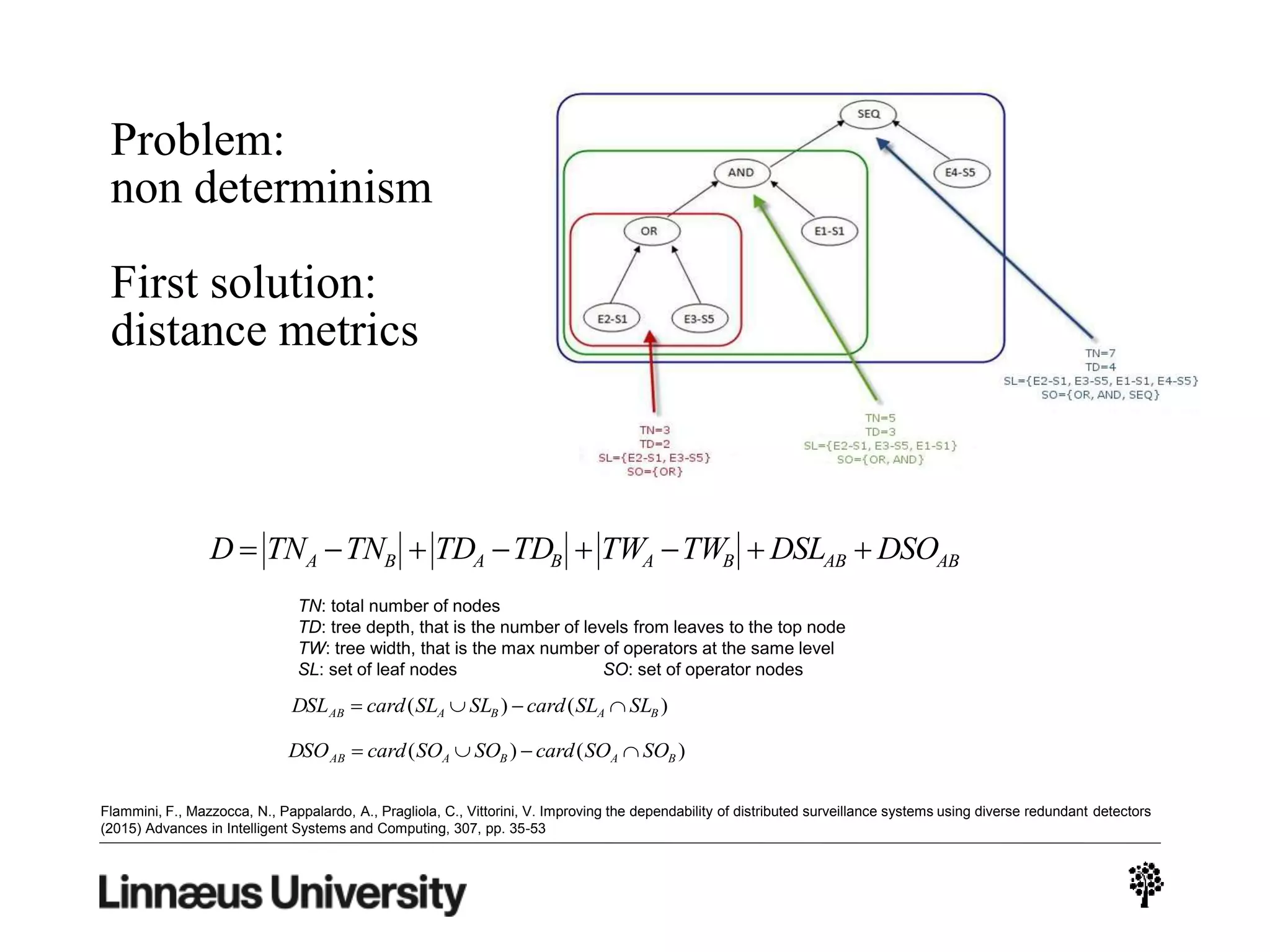
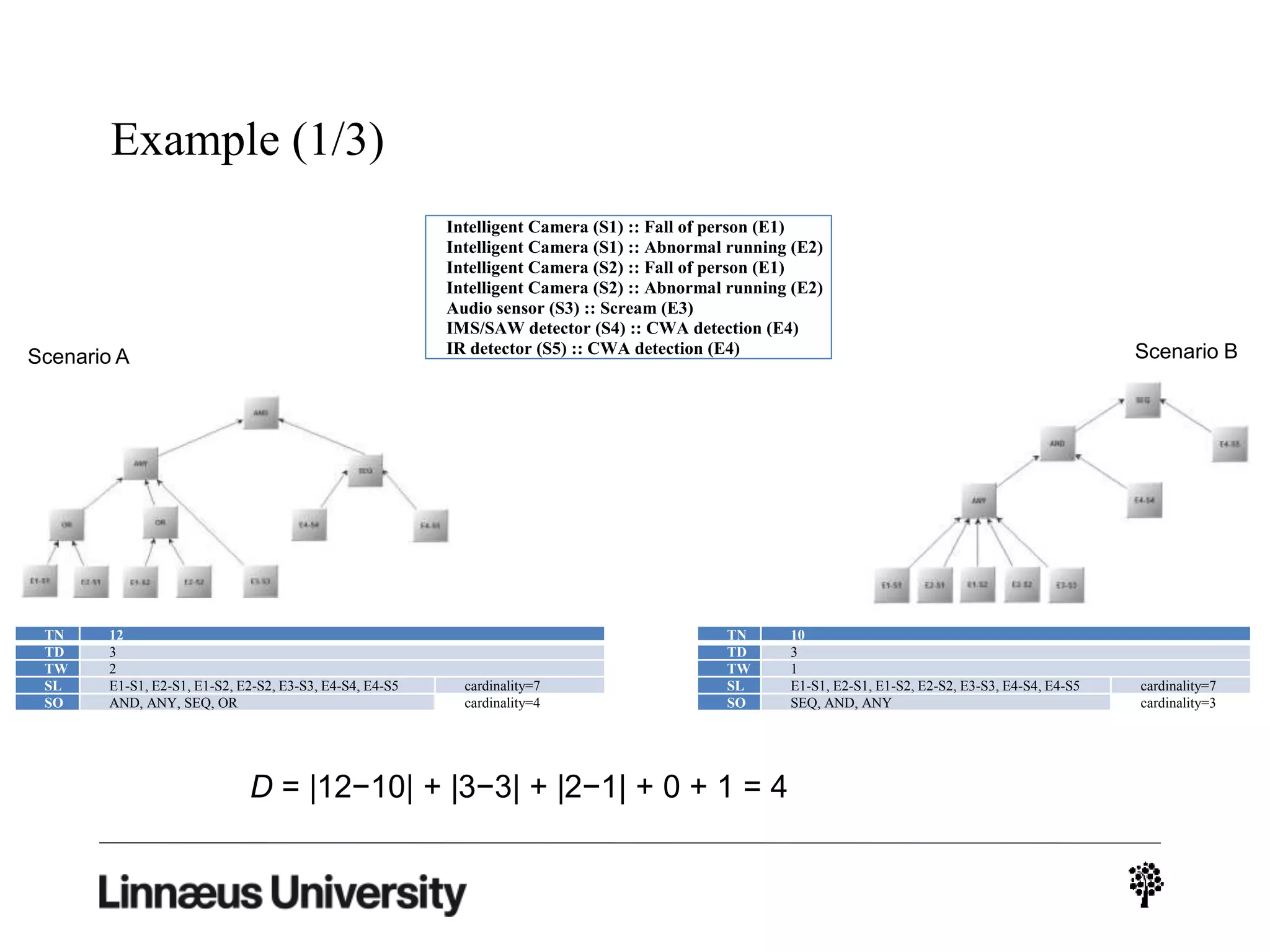
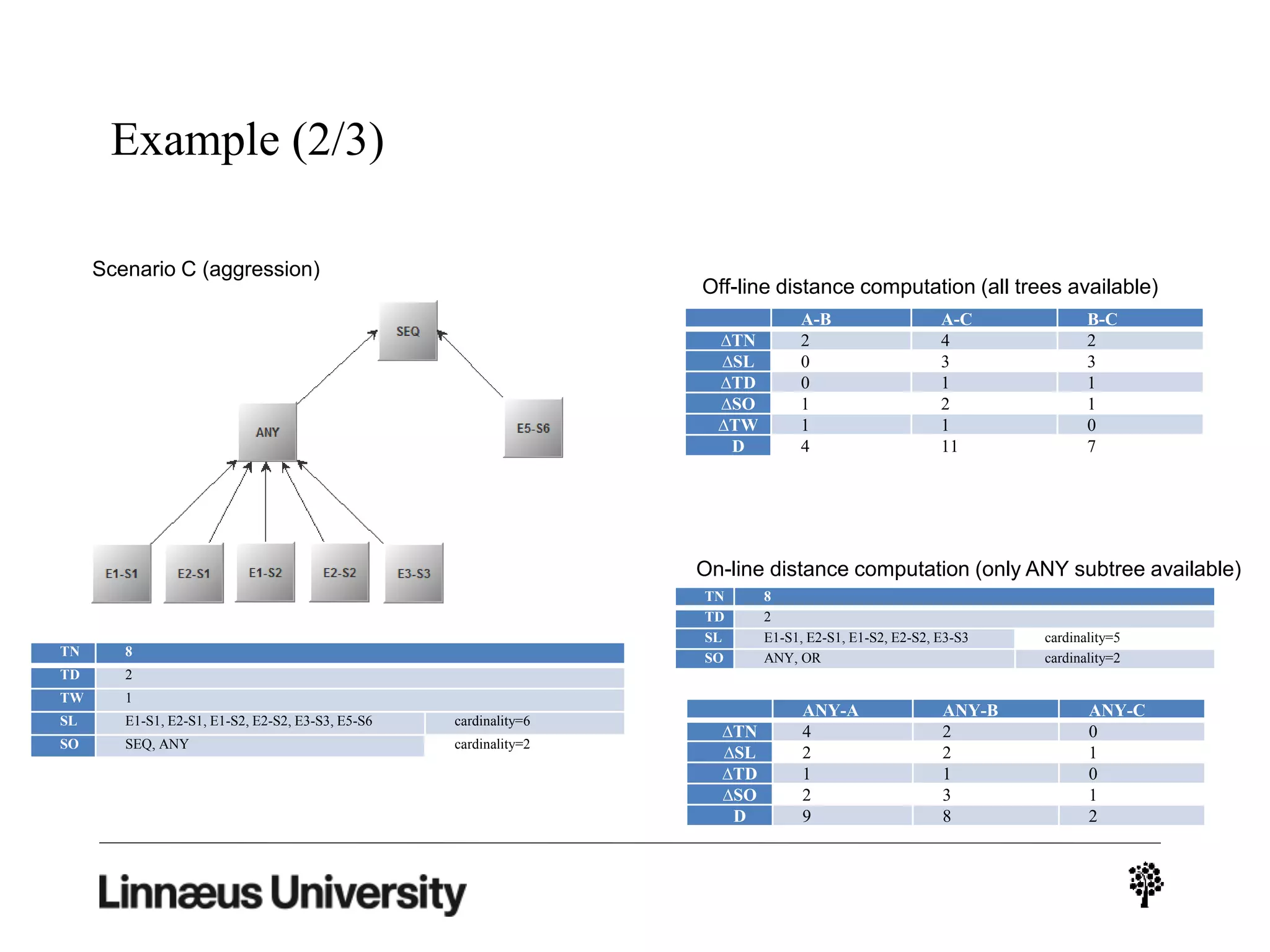
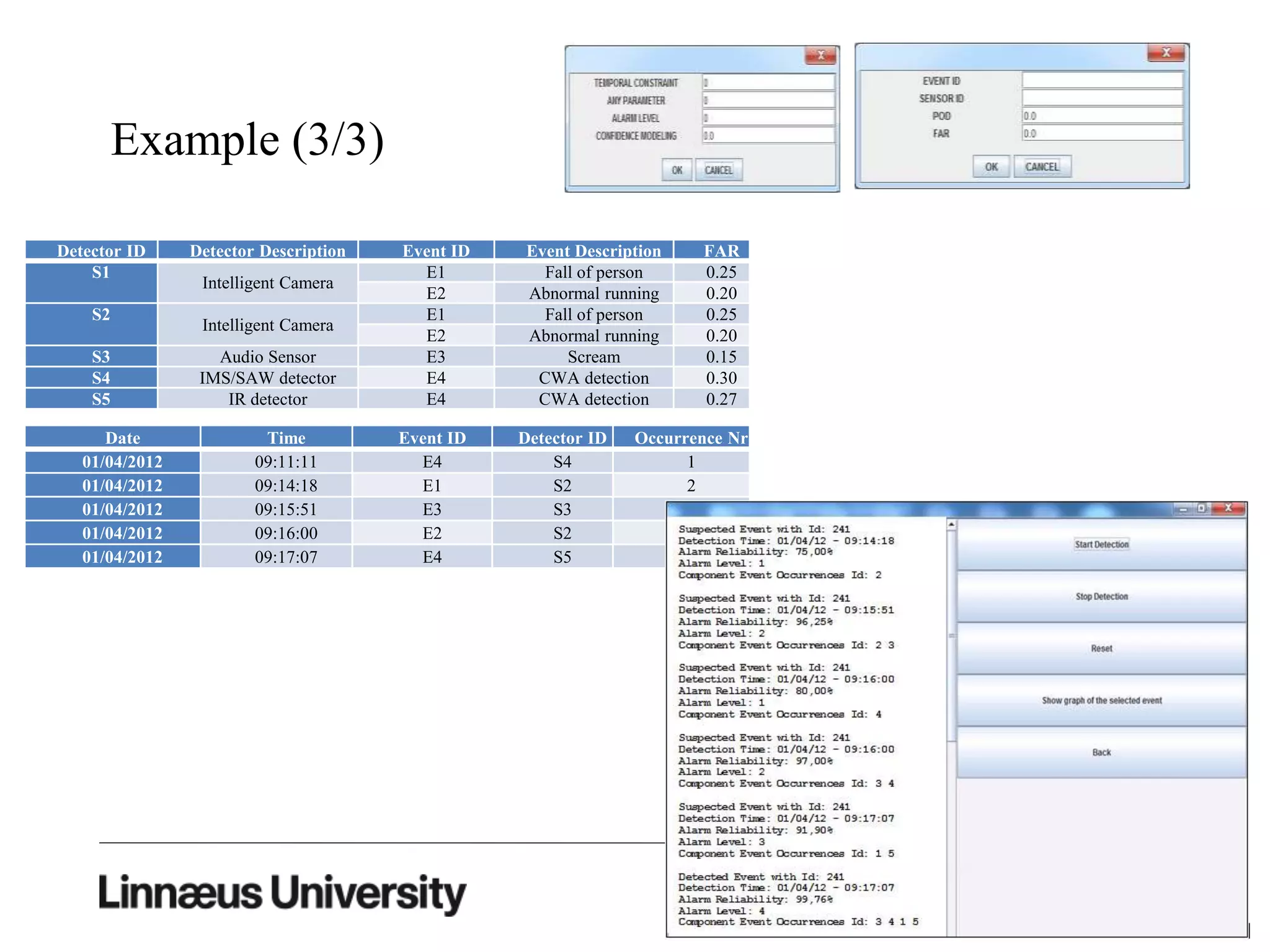
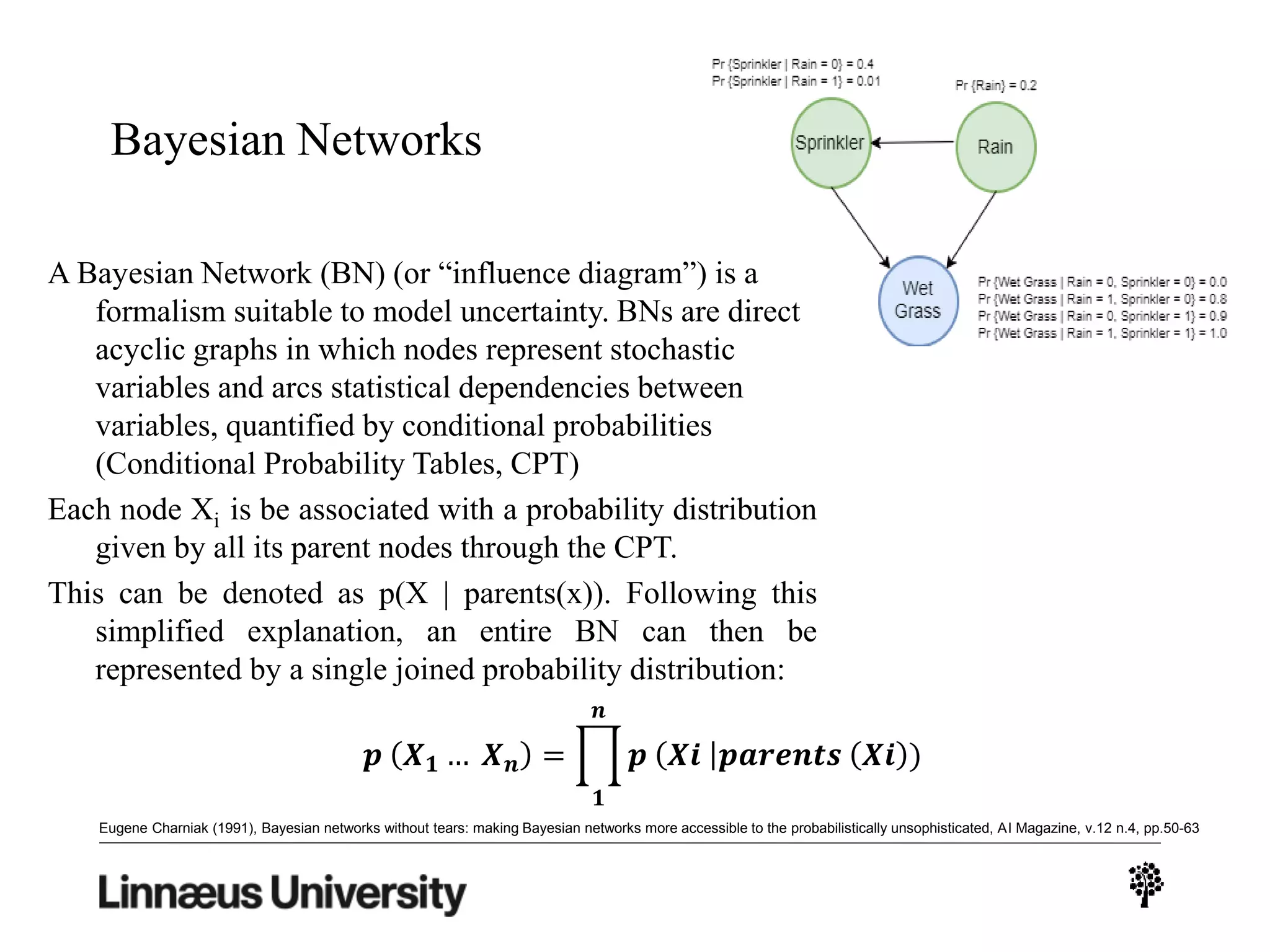
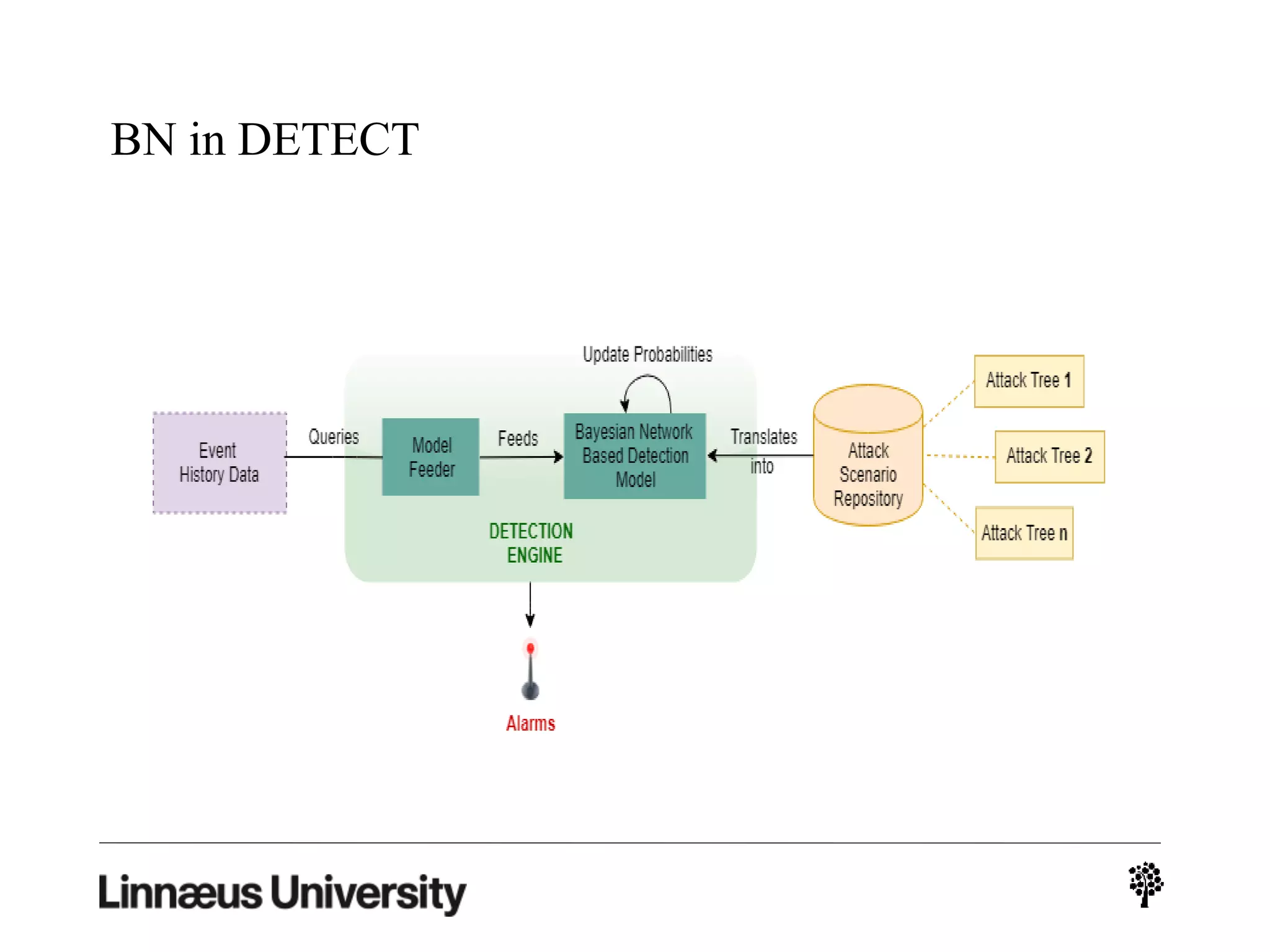
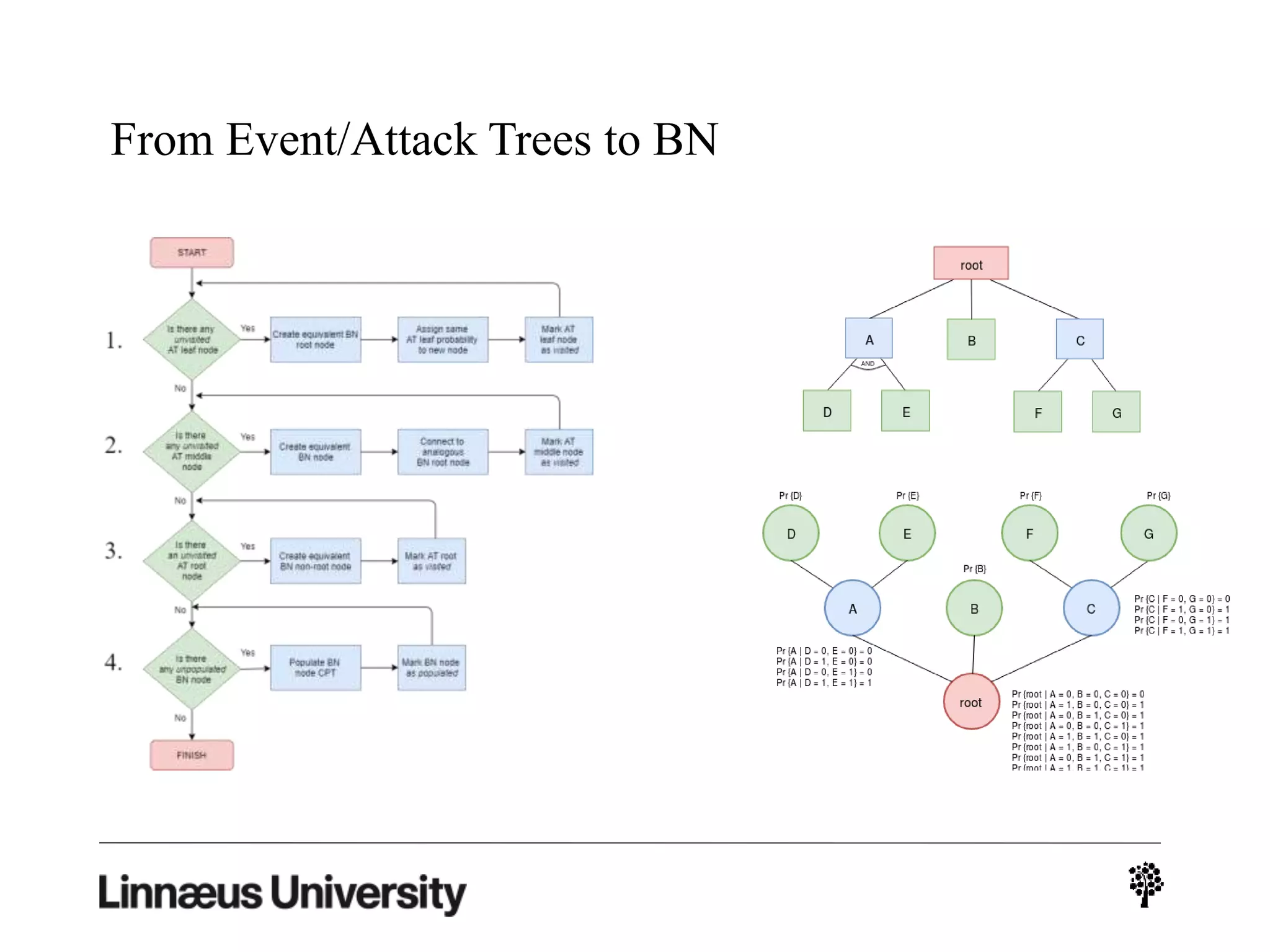
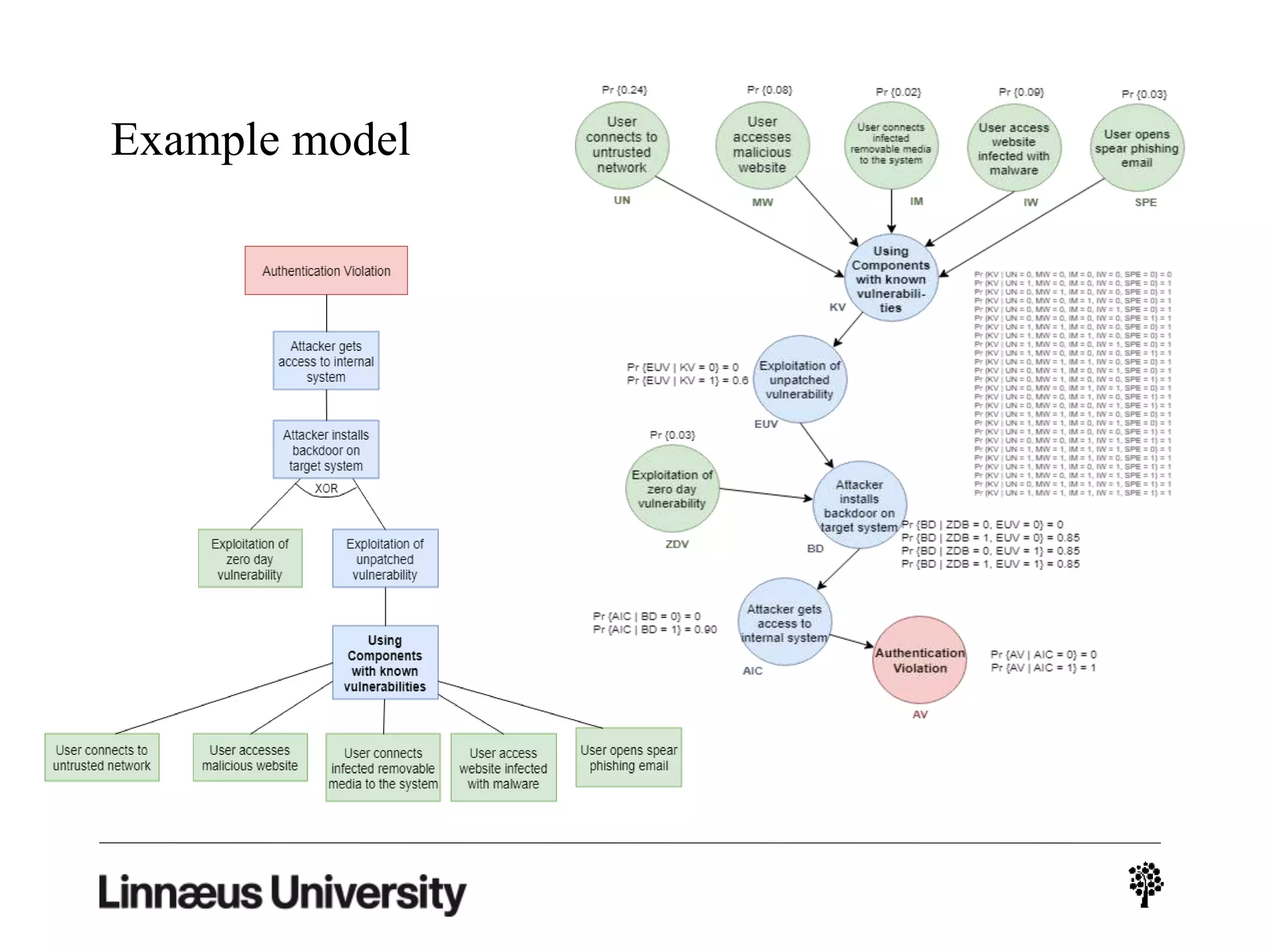
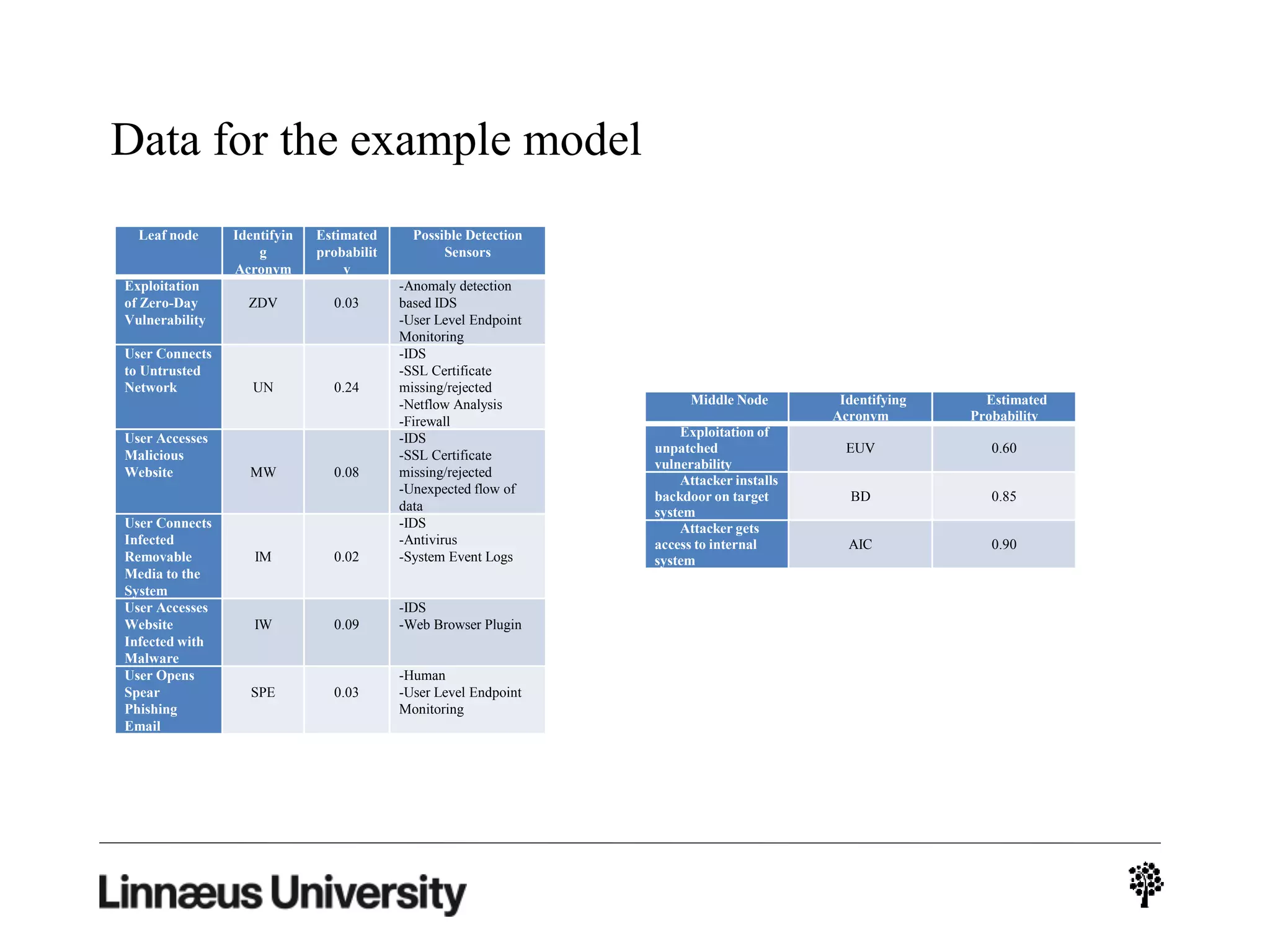
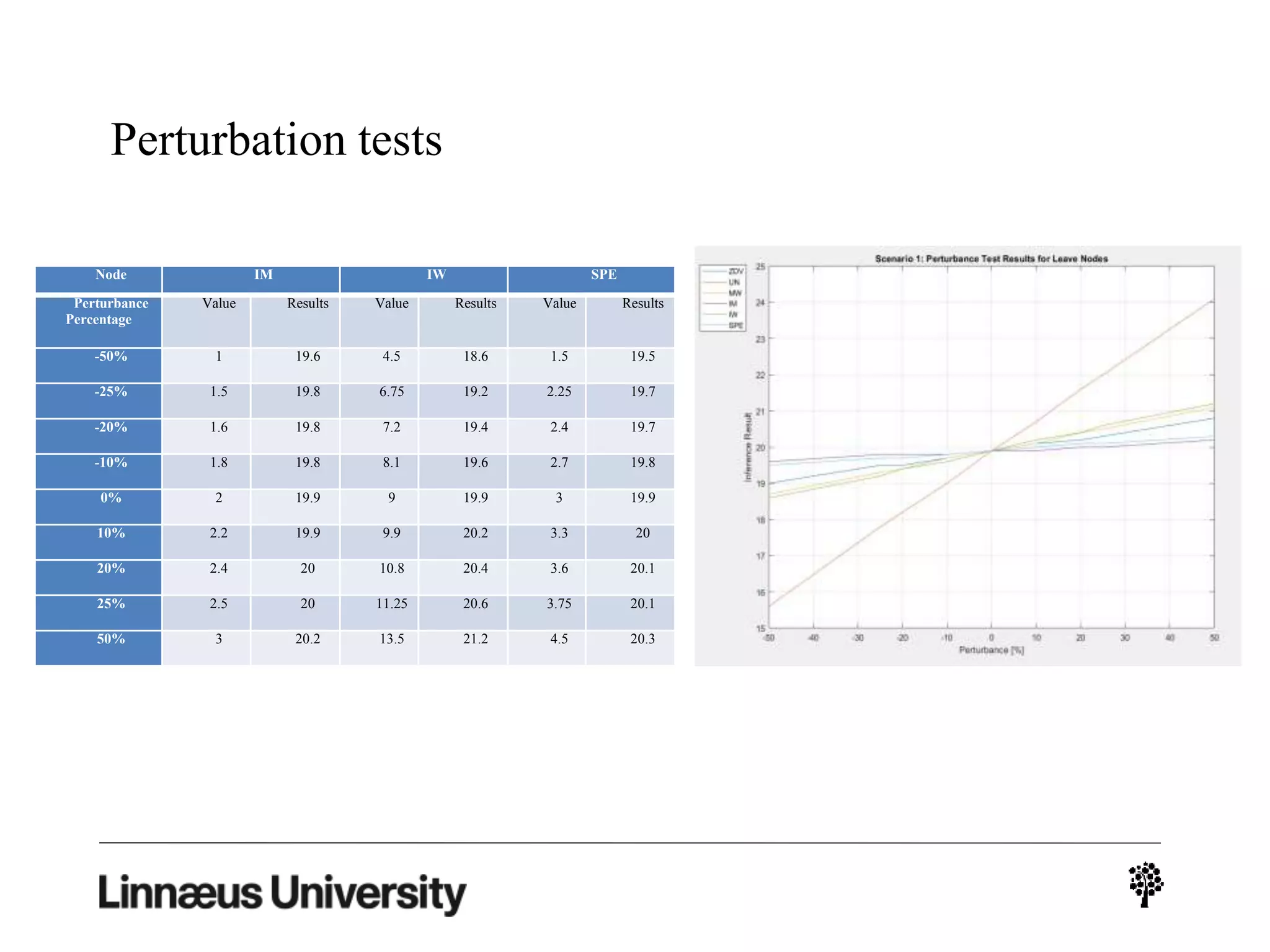
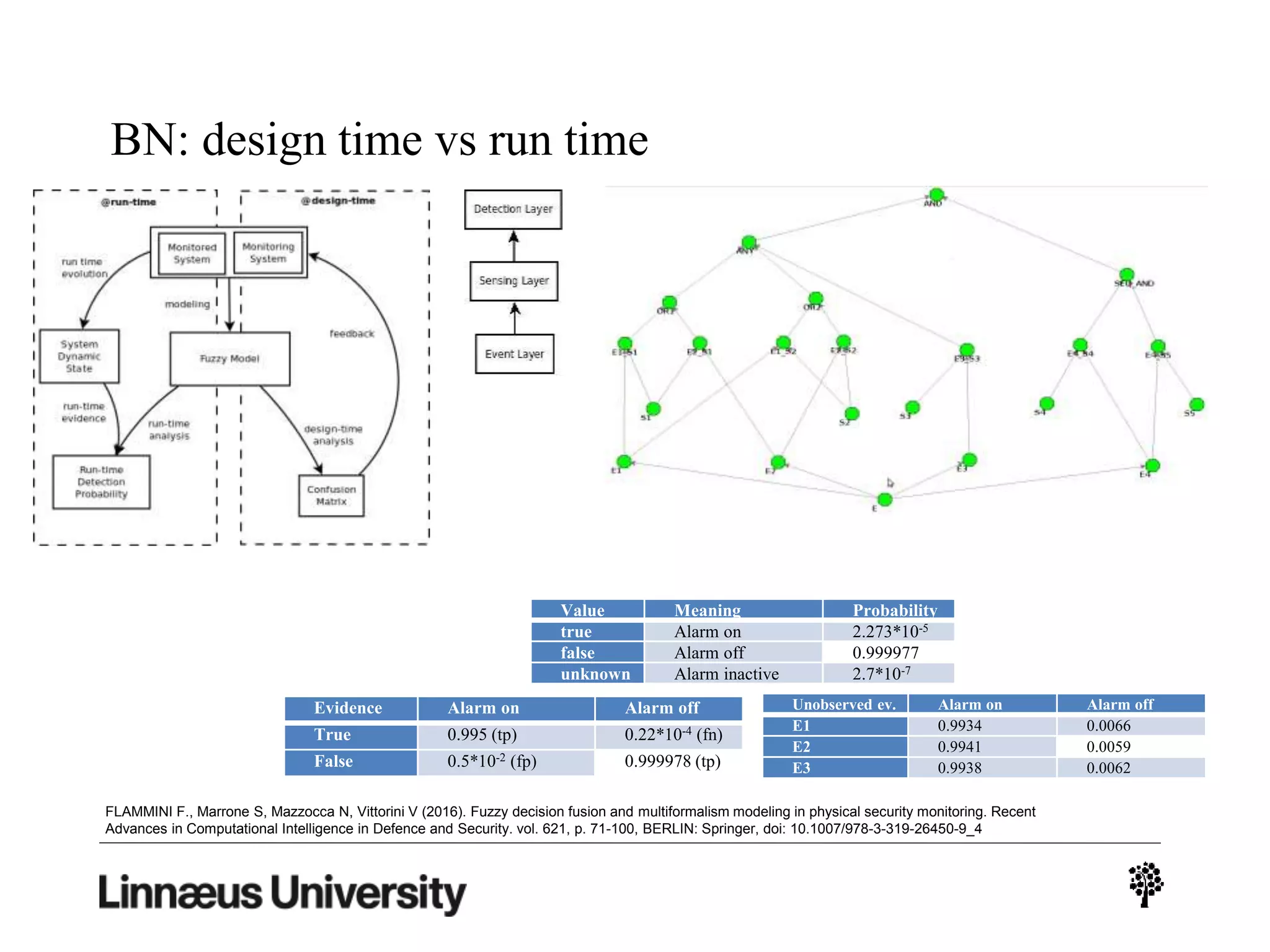
The document discusses using artificial intelligence techniques like Bayesian networks and event trees for cybersecurity applications. It describes how these techniques can help address issues with security operations centers being overwhelmed by too much information from various sensors and systems. Bayesian networks and event trees can help fuse data from different sources to detect threats more effectively. The document provides examples of how Bayesian networks can be built using historical threat data and customized for specific organizations. It also discusses how these models can be updated dynamically based on real-time data from systems.