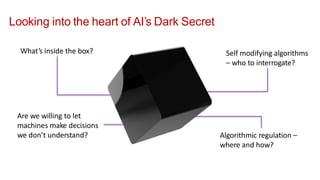
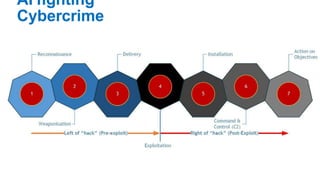
The document discusses the critical role of artificial intelligence (AI) and machine learning (ML) in combating cybersecurity threats, highlighting the evolution of these technologies and their rapidly growing applications across industries. It emphasizes the increasing sophistication of cyber attacks and the necessity for enhanced cybersecurity measures, predicting significant growth in global cybersecurity spending. AI is portrayed as a transformative force, enabling faster threat detection and more effective protection against evolving threats.