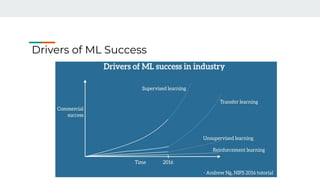
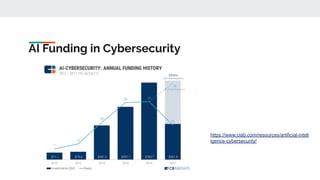
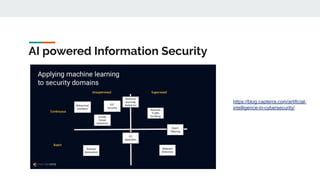
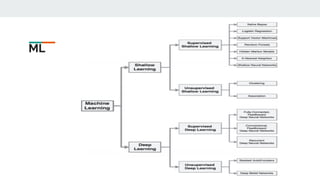
AI and machine learning techniques are increasingly being used for security applications. Some key points:
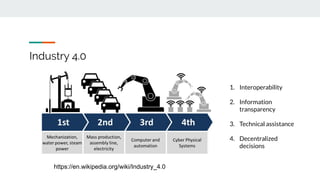
1. AI is enabling new technologies like Industry 4.0 through applications in IoT, big data, and automated decision making. Security is evolving to use these new AI capabilities.
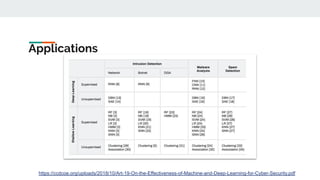
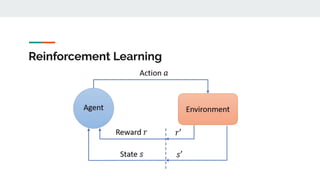
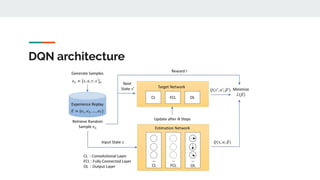
2. Common ML tasks used in security include classification, clustering, and anomaly detection. Deep learning models are also used for malware detection.
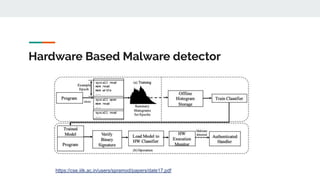
3. Areas where AI is applied to security include malware detection, threat detection, fraud detection, and network security monitoring. Both supervised and unsupervised learning techniques are used.
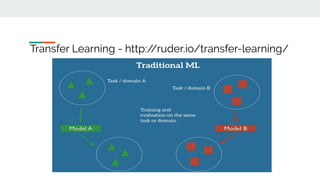
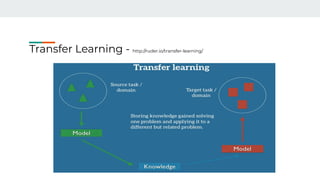
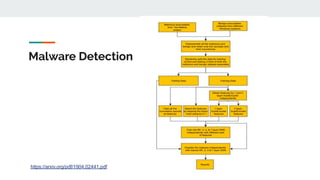
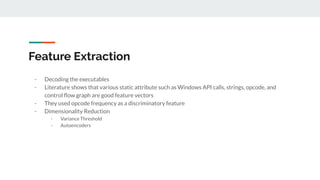
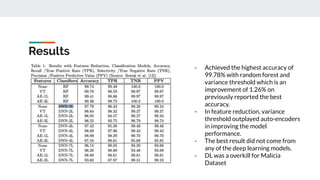
4. Building effective AI security solutions requires datasets, feature extraction, model selection and training, and evaluation of results. Transfer