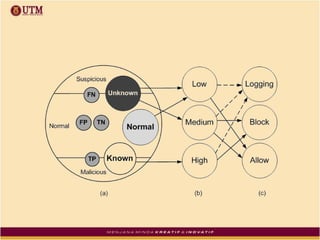
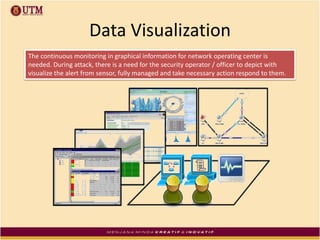
The document reviews the evolution and effectiveness of intrusion prevention systems (IPS) and intrusion detection systems (IDS) from the 1990s to present, highlighting their roles in network security against increasing cyber threats. It discusses various challenges, including false alarms, data management, and the need for enhanced detection and response capabilities, while proposing future improvements in feature extraction and real-time analysis. The authors argue for an integrated approach that optimally combines IPS and IDS functionalities for comprehensive network security management.