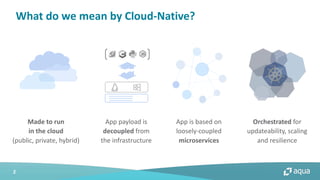
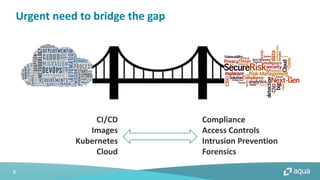
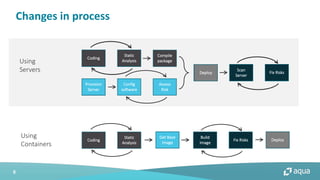
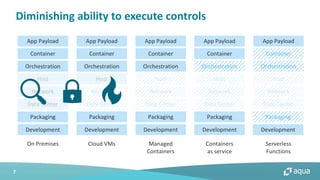
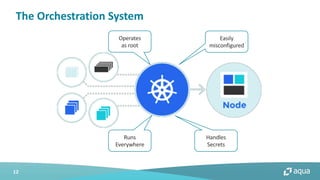
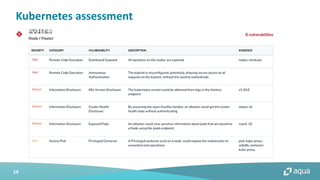
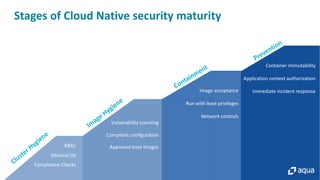
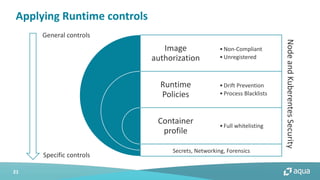
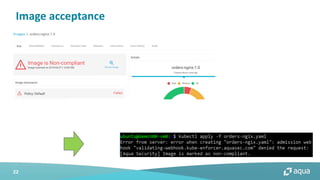
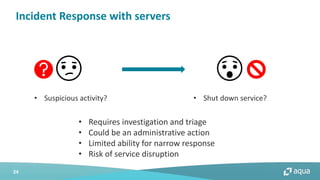
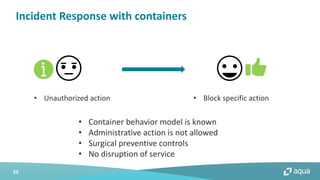
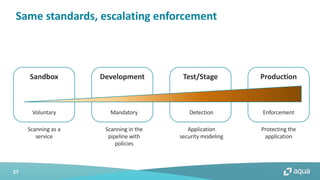
This document discusses cloud-native security and the challenges of securing containerized and microservices-based applications in cloud environments. It outlines a maturity model for cloud-native security with stages like image acceptance, least privilege at runtime, container immutability, and immediate incident response. The document also provides checklists and best practices for securing Kubernetes clusters, container images, and the container build pipeline to help bridge the gap between development, operations, and security in cloud-native applications.