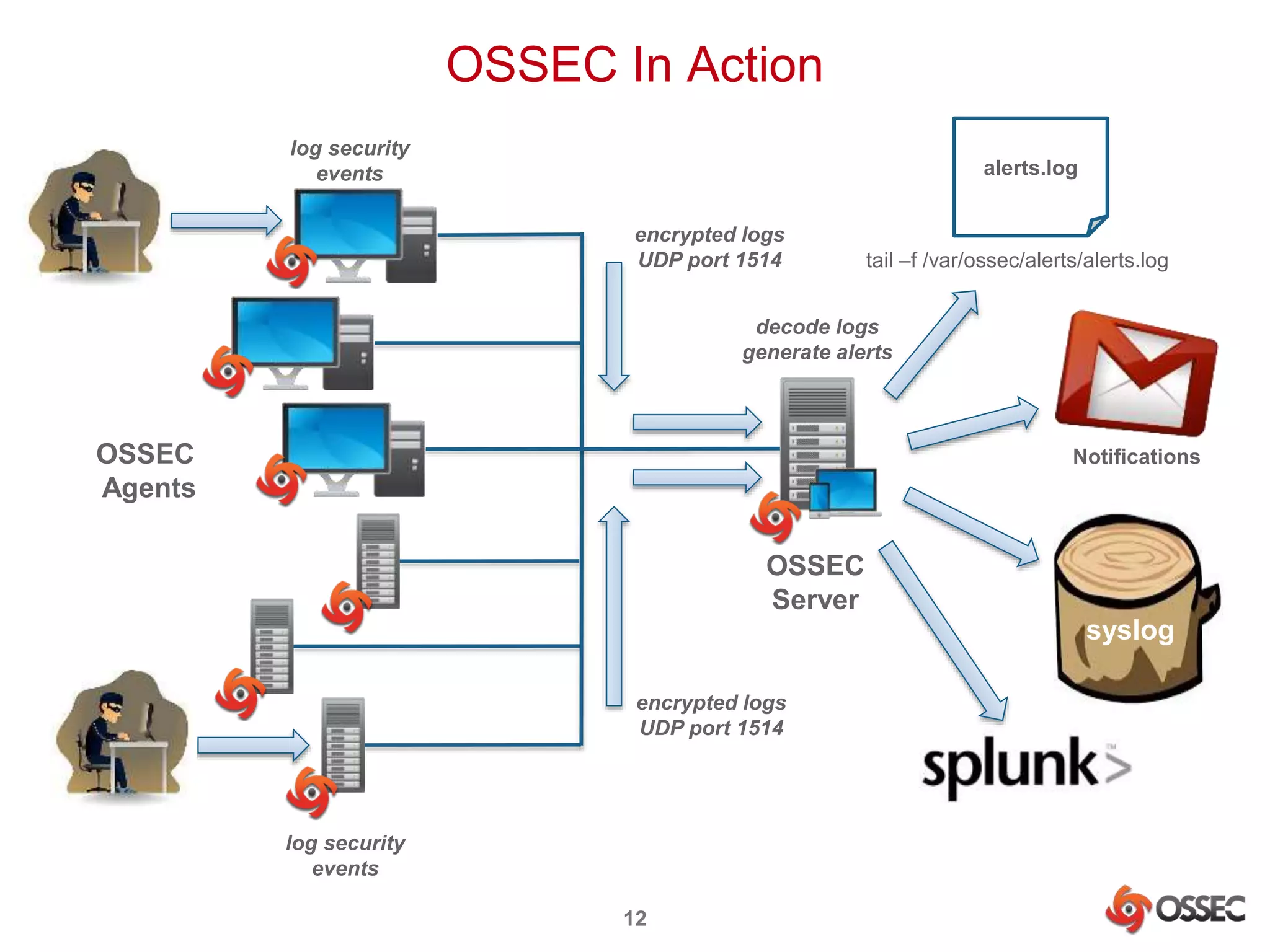
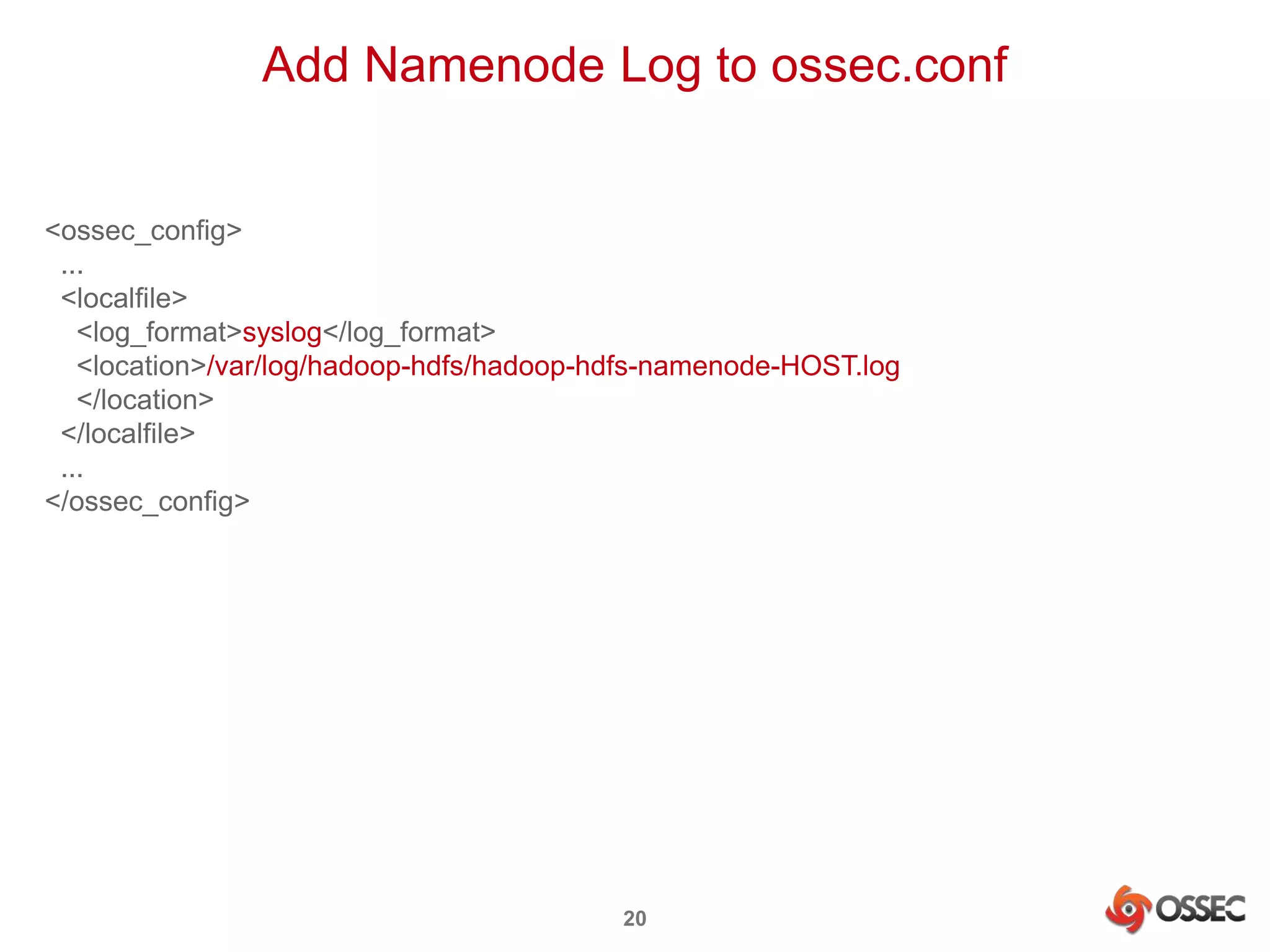
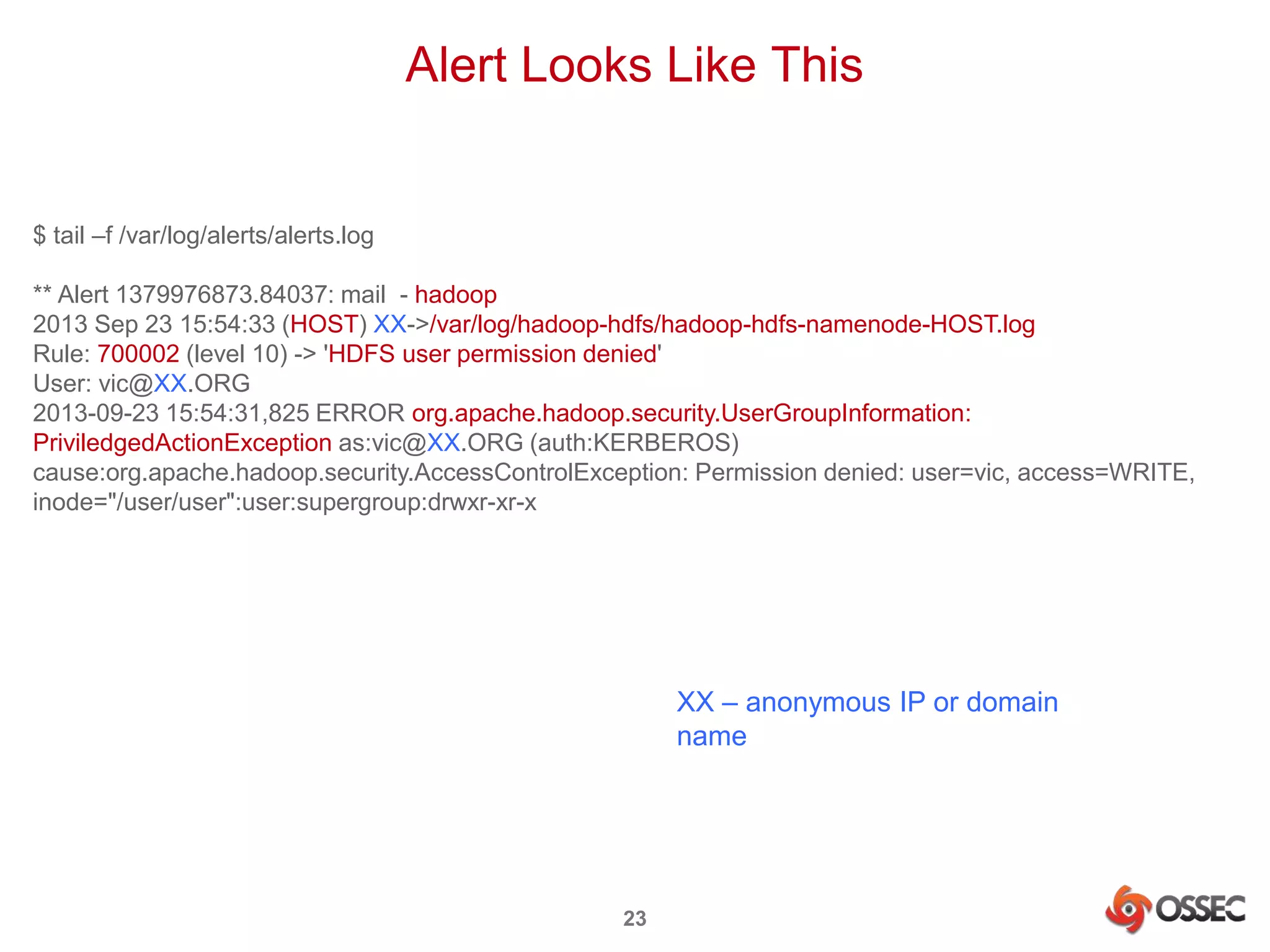
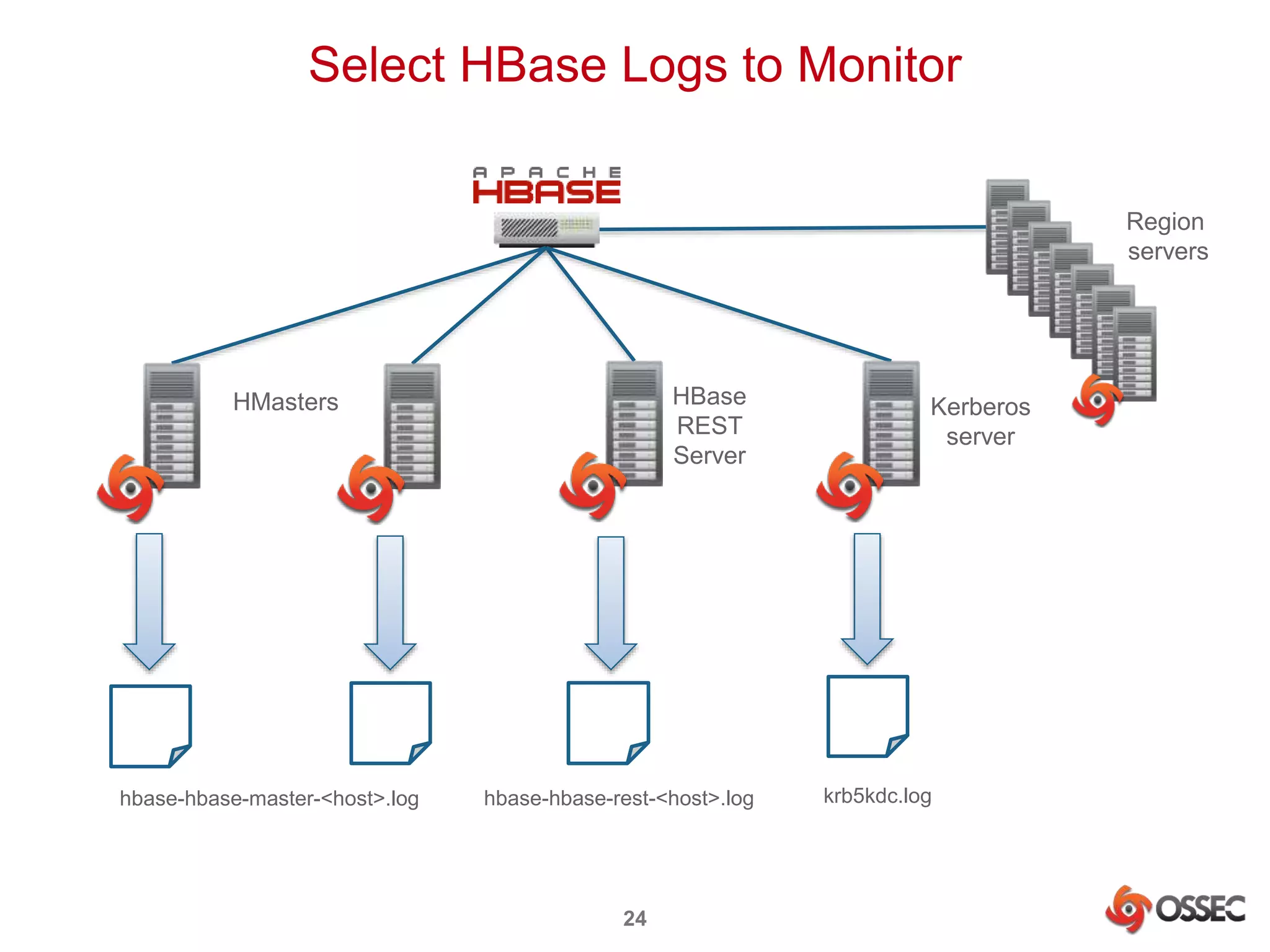
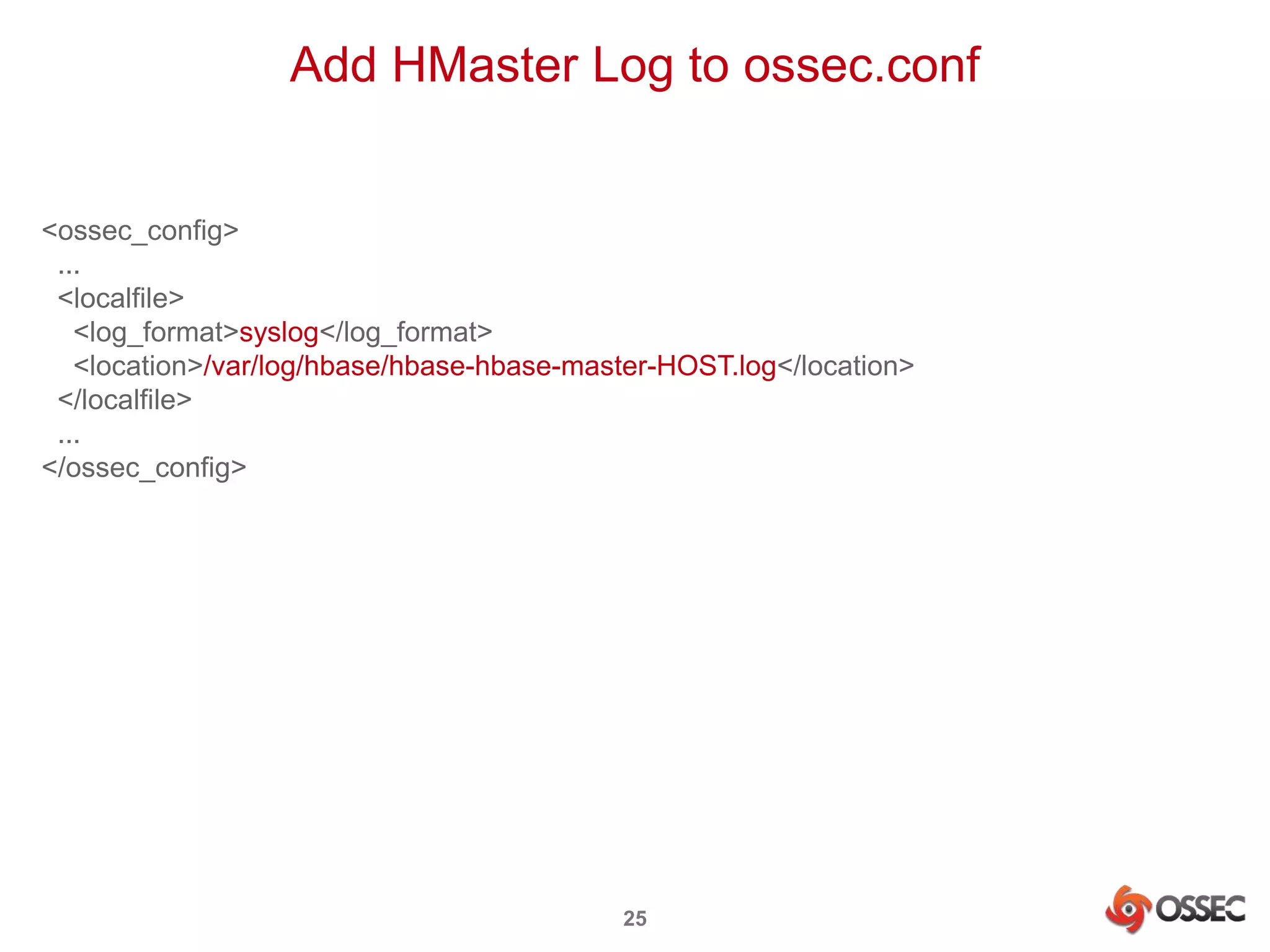
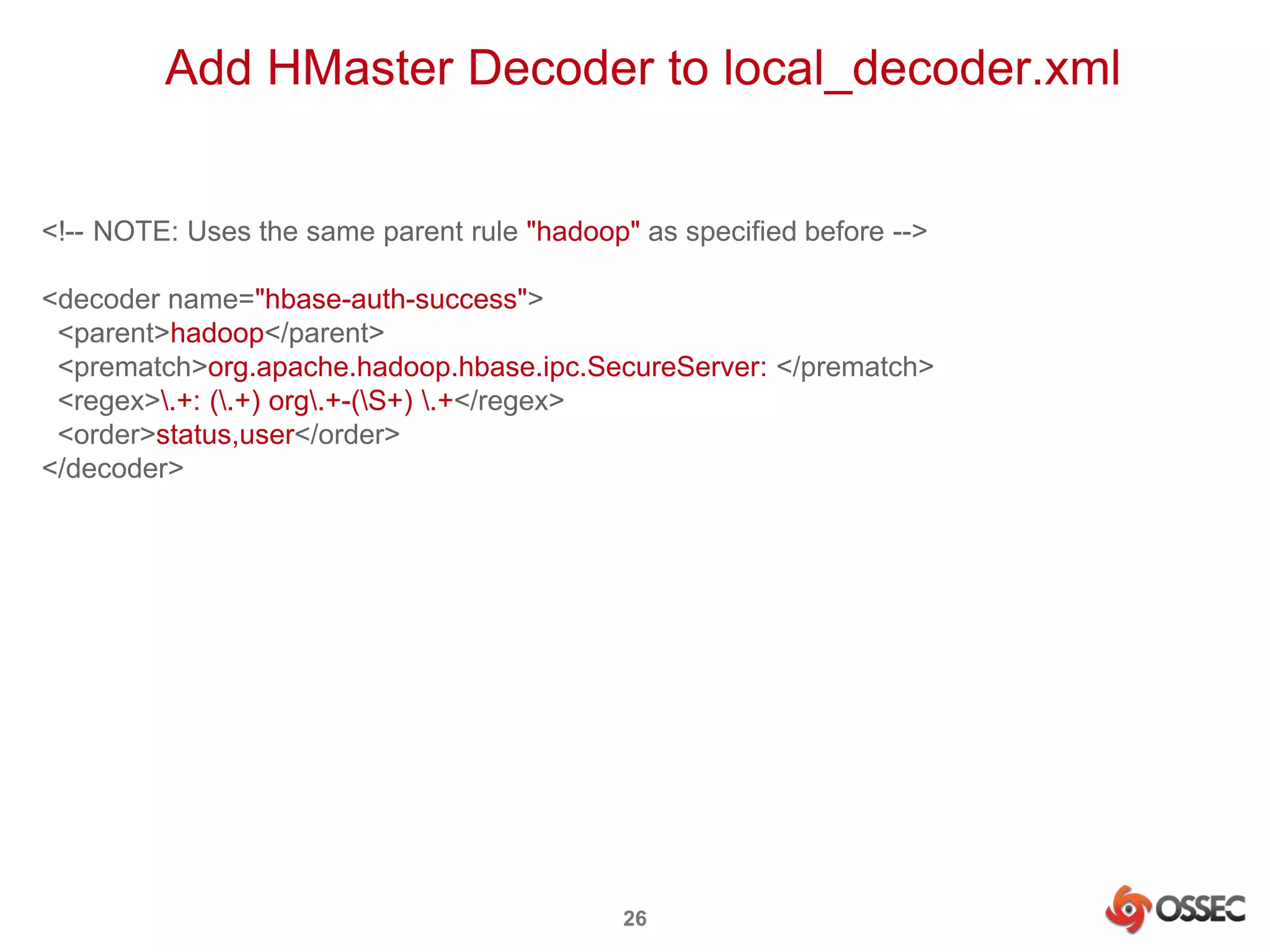
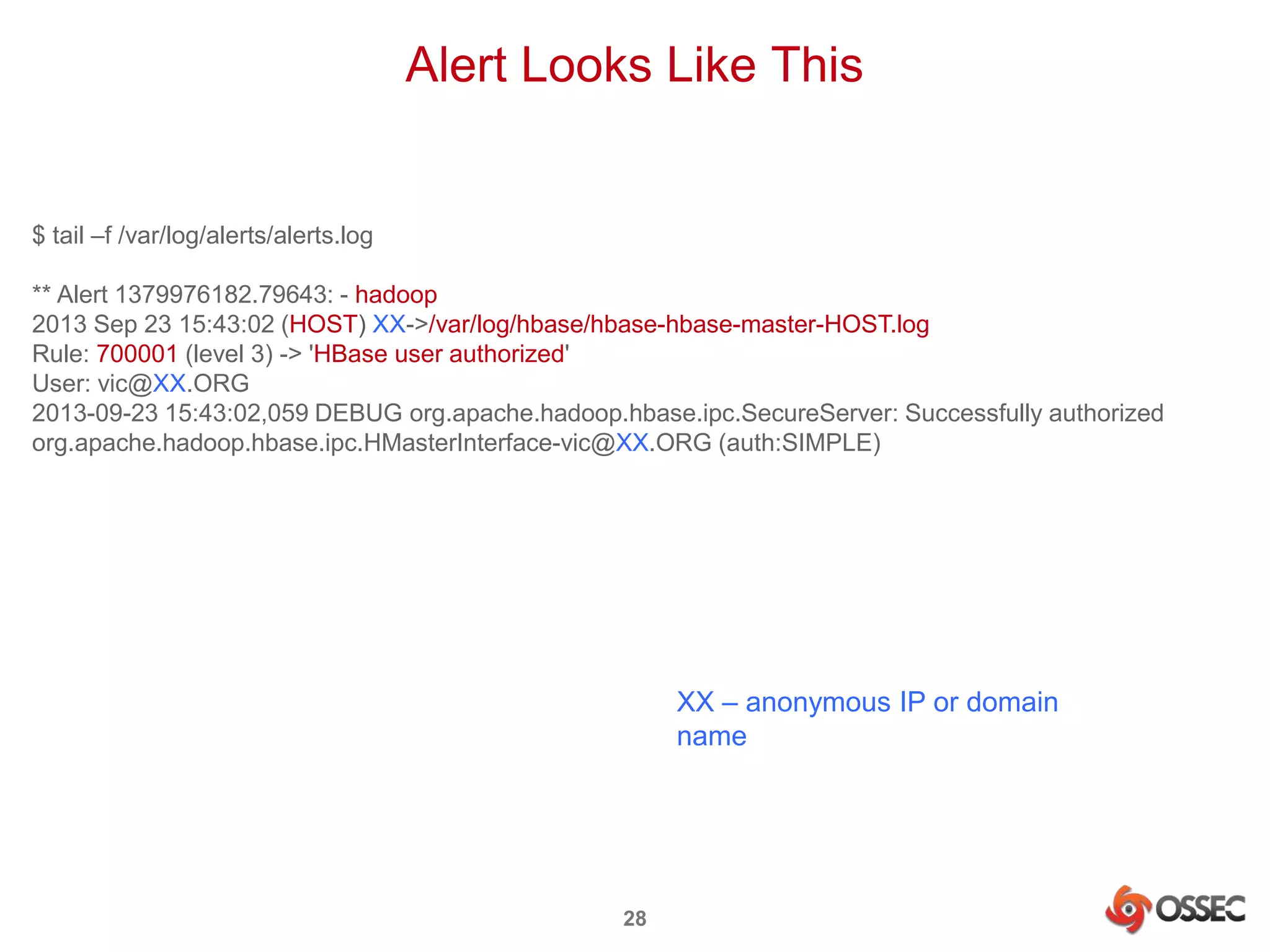
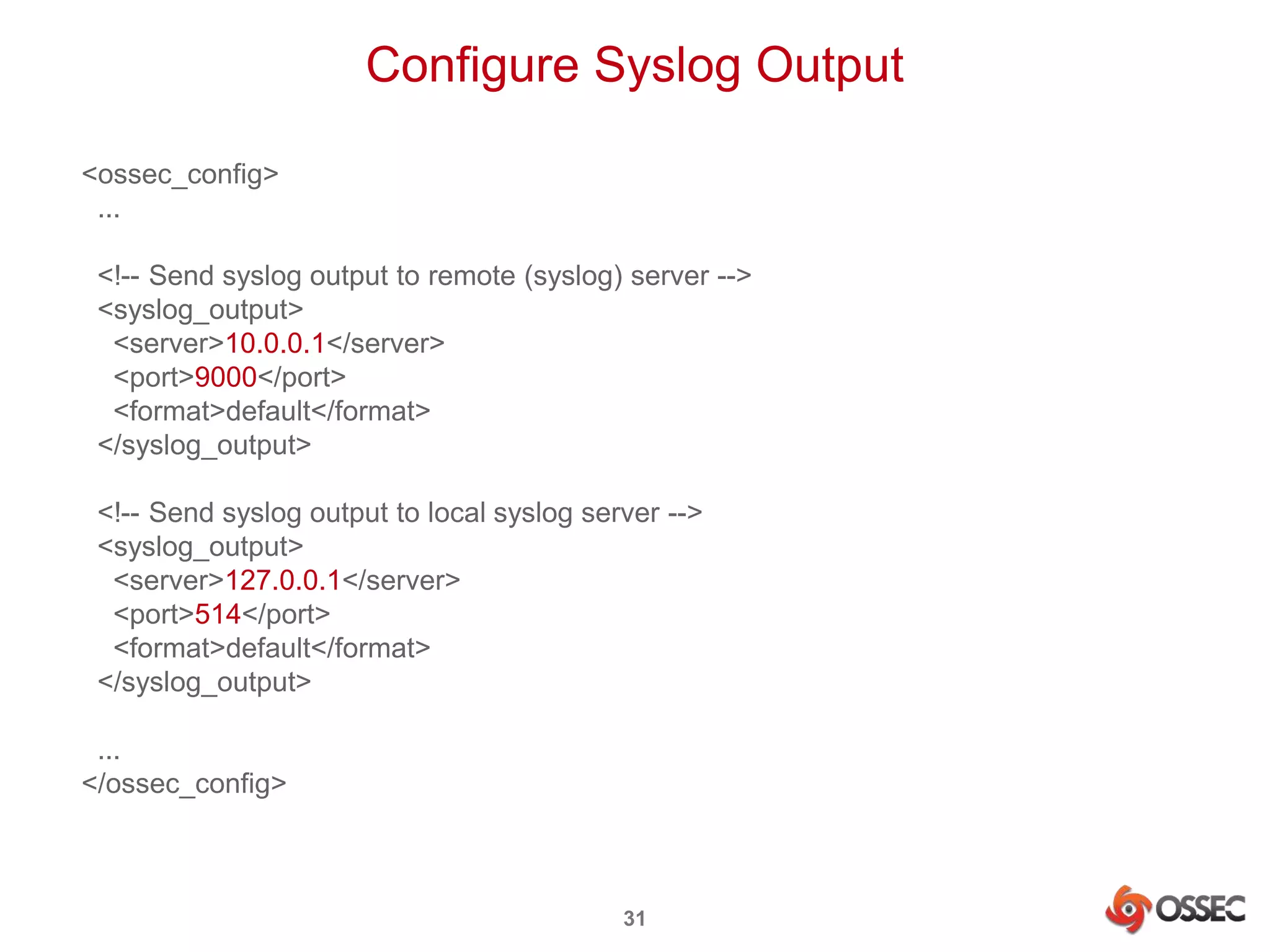
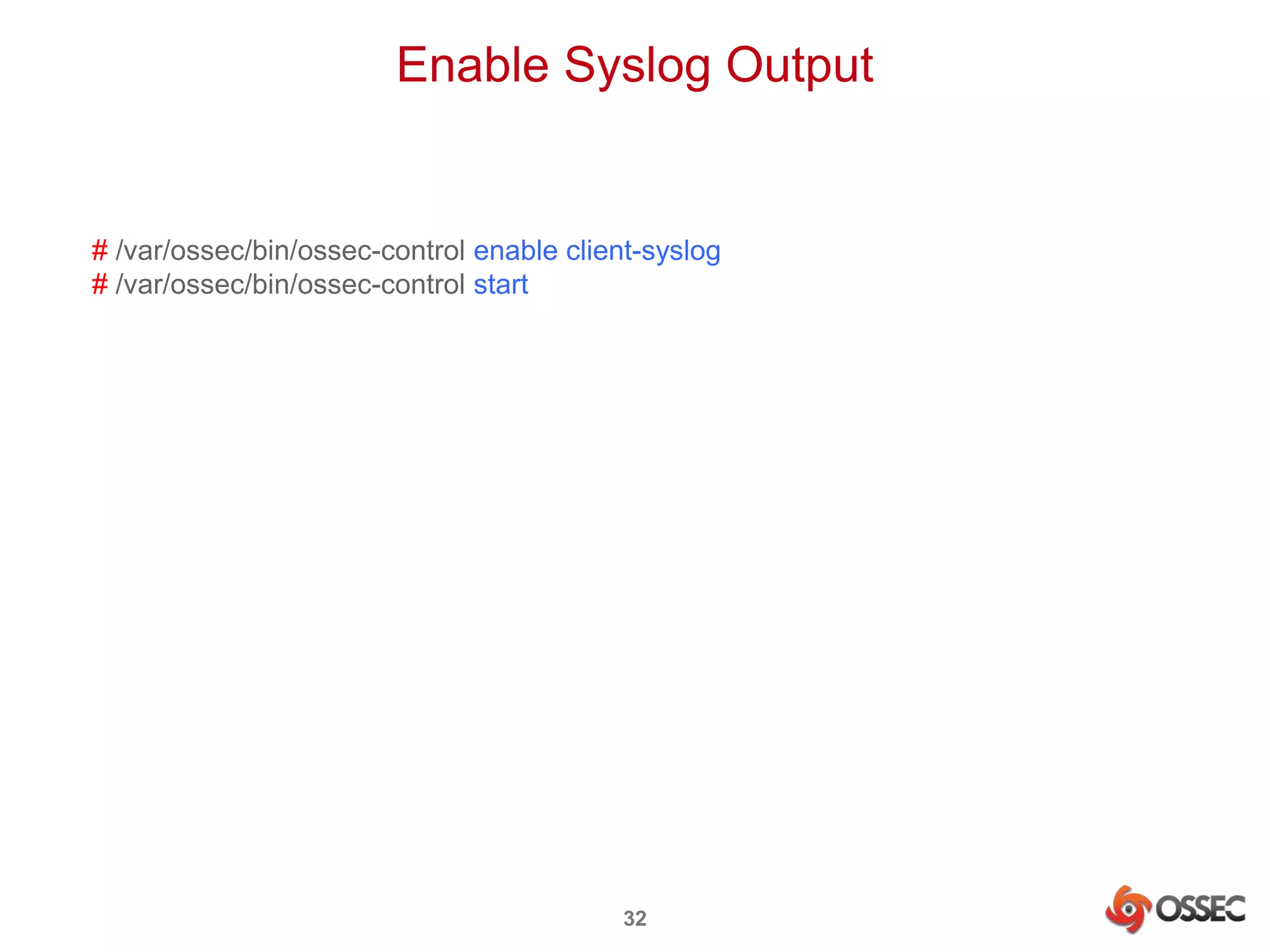
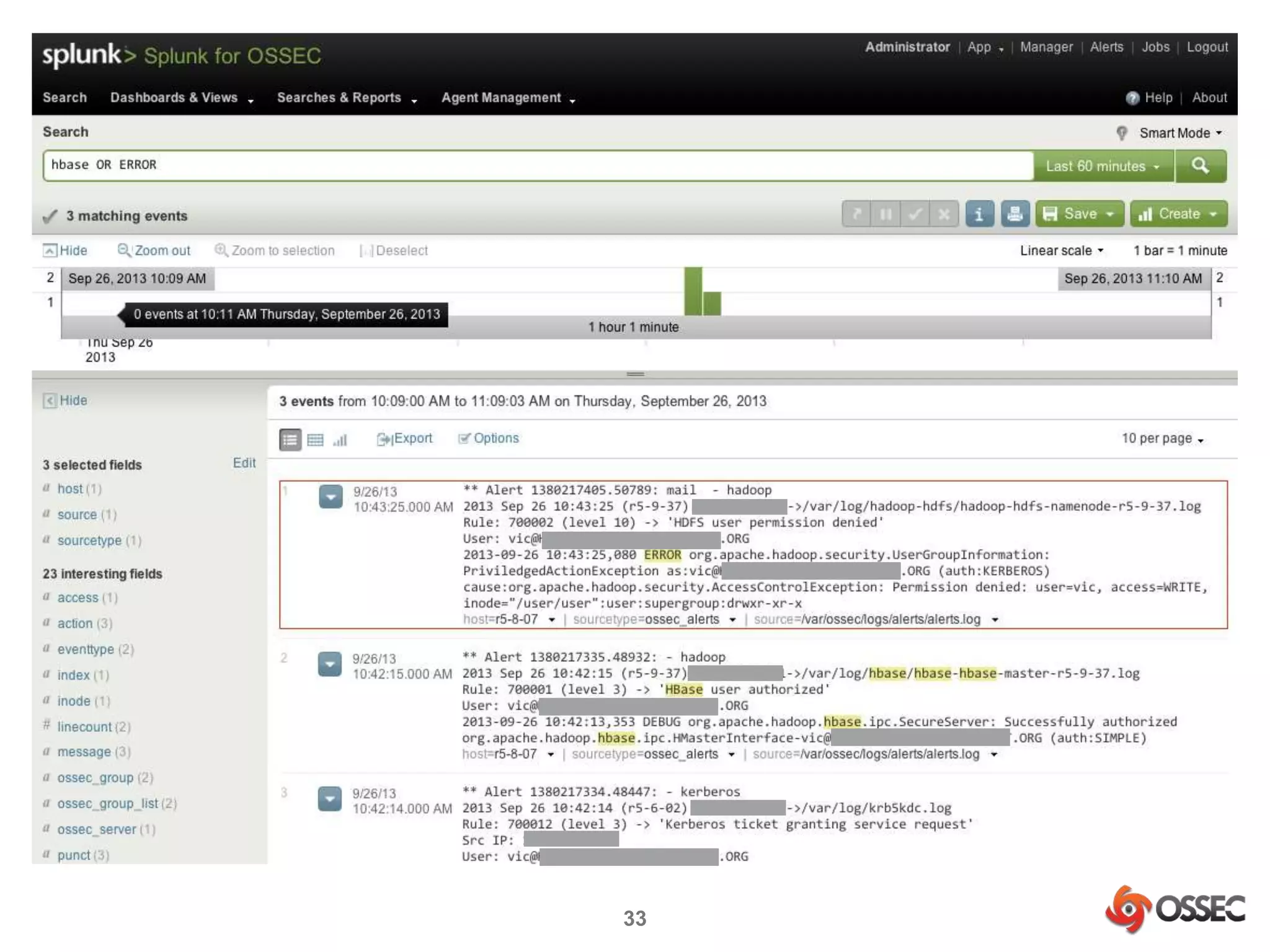
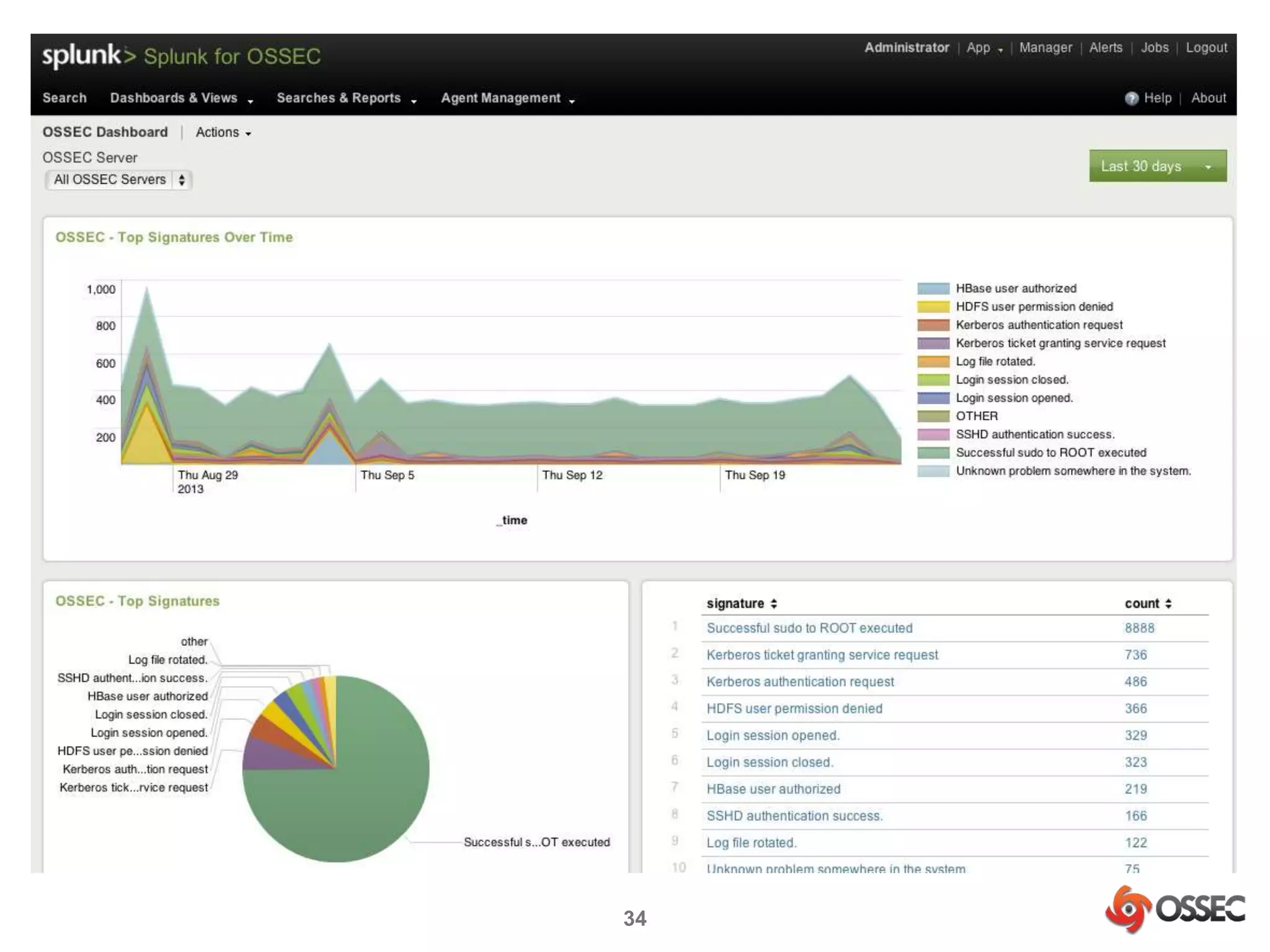
This document discusses securing Hadoop clusters with OSSEC host-based intrusion detection. It provides an overview of OSSEC and how to configure it to monitor Hadoop and HBase logs. Specific steps are outlined to configure file integrity checking, select logs to monitor, add decoders and rules to generate alerts for security events like unauthorized access attempts. Sending alerts to Splunk for further analysis is also recommended for security event monitoring and trend analysis.