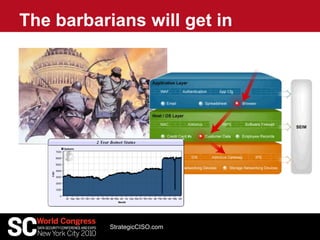
This document discusses strategies for data protection and cybersecurity. It advocates taking a strategic rather than tactical approach that is driven by business needs rather than vendors. It emphasizes the importance of understanding threats, vulnerabilities, and risks; developing comprehensive protection strategies; operationalizing security; and continuously evaluating and improving security measures. The overall message is that effective cybersecurity requires understanding the environment, threats, and business needs in order to develop and execute holistic, risk-based strategies.





![Security Trends – Current View
StrategicCISO.com- CONFIDENTIAL -
Endpoint Suites Network UTM Application
Security
Vulnerability
Management
[Other Point
Products]
Security Information and Event
Management
• Alerts
• Log Mgt
• Event Correlation
• Compliance Certification
Governance Risk
and Compliance
• User Policy Compliance
• Compliance Workflow and Reporting
• Remediation Workflow and Reporting](https://image.slidesharecdn.com/2010scworldcongressnyc-12894058059555-phpapp01/85/2010-Sc-World-Congress-Nyc-6-320.jpg)

![Security – Future View
StrategicCISO.com- CONFIDENTIAL -
Endpoint Suites Network UTM Application
Security
Vulnerability
Management
IT Security Management
Vendors: IBM, HP, Cisco, Computer Associates, Symantec, McAfee
[Other Point
Products]
Comprehensive
Security Test and Measurement
•Verify and Validate Security Controls
•Measure Real-world Threat Readiness
•Measure Security Effectiveness
Security Information and Event
Management
• Alerts
• Log Mgt
• Event Correlation
• Compliance Certification
Governance Risk
and Compliance
• User Policy Compliance
• Compliance Workflow and Reporting
• Remediation Workflow and Reporting](https://image.slidesharecdn.com/2010scworldcongressnyc-12894058059555-phpapp01/85/2010-Sc-World-Congress-Nyc-8-320.jpg)