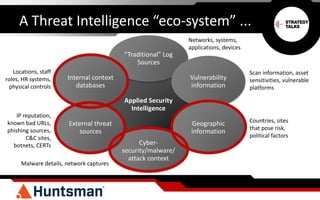
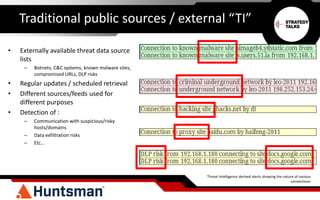
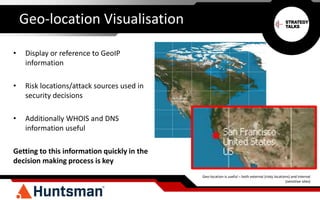
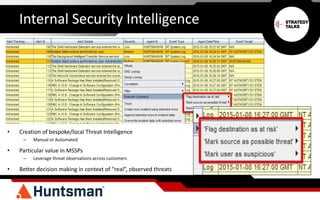
The document discusses the importance of threat intelligence in enhancing security responses, emphasizing that it encompasses both internal and external data sources. It illustrates how organizations, particularly in the defense sector, leverage threat intelligence for real-time alerts and decision-making, while also highlighting the need for automated processes in analyzing network behavior. Ultimately, effective threat intelligence aids in the prompt identification and resolution of cyber threats.