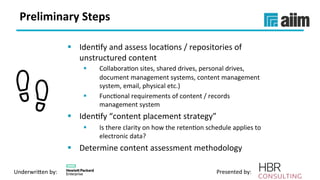
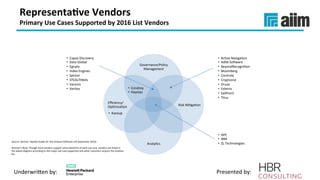
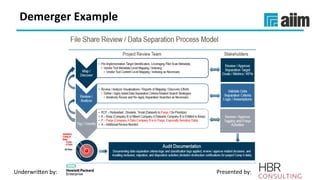
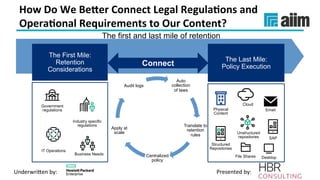
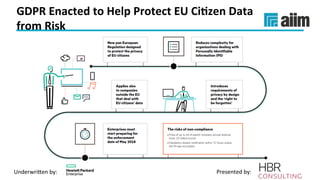
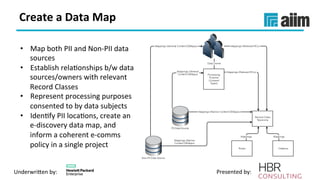
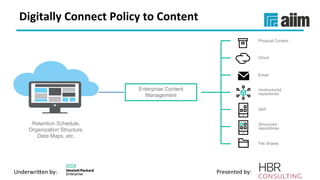
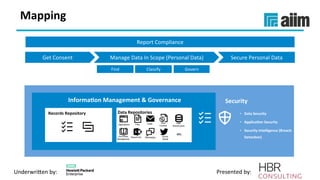
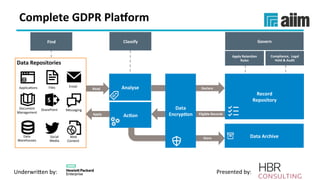
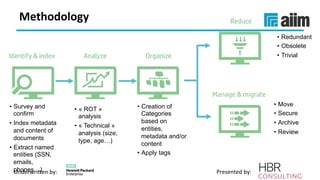
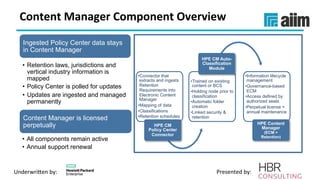
The document discusses the importance of effective data retention policies and information governance in organizations, highlighting challenges such as unstructured data, compliance risks, and data privacy issues. It emphasizes the need for a clear governance framework, comprehensive data assessment, and the elimination of unnecessary data to improve operational efficiency and regulatory compliance. The presentation also introduces foundational components for defensibility and offers practical steps to align legal requirements with content management strategies.