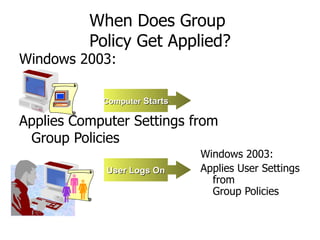
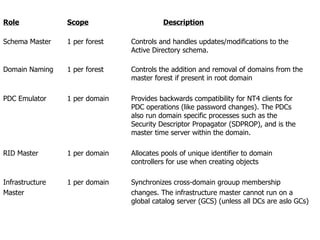
Active Directory (AD) is a hierarchical framework for storing information about objects like users, computers, and groups in a centralized database. It allows administrators to easily deploy software, apply policies, and manage access across an organization. The logical structure of AD includes forests, domains, and organizational units that define security boundaries and make administration and resource access easier to manage.