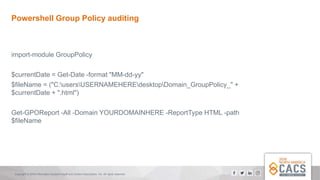
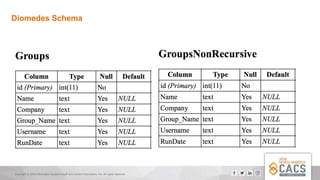
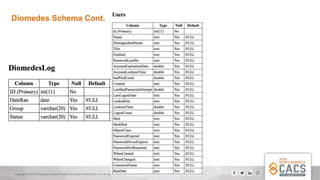
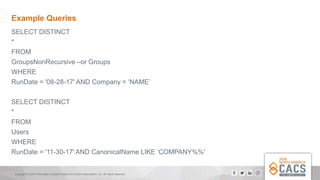
The document provides a comprehensive overview of Active Directory (AD), explaining its purpose, structure, and components such as domains, forests, and group policies. It emphasizes the importance of AD for IT administrators in managing user access and introduces the Diomedes data warehouse for auditing purposes. Additionally, it highlights the use of PowerShell for active directory management and querying.