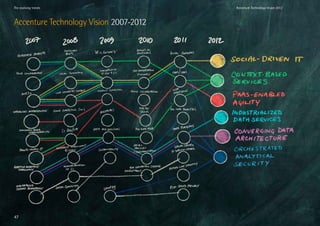
The Accenture Technology Vision 2012 report highlights the transformative role of technology in business as organizations must adapt to a rapidly changing technological landscape. Key trends identified include context-based services, converging data architectures, and the importance of security, urging companies to move beyond cost-cutting strategies and embrace innovation. CIOs are encouraged to leverage these trends to propel growth and improve customer experiences through actionable insights derived from contextual data.