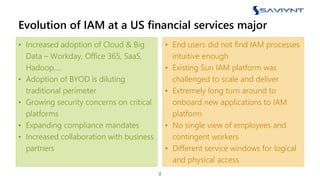
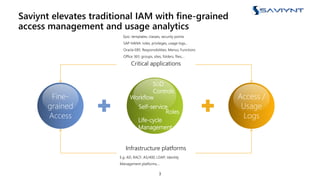
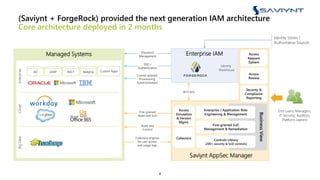
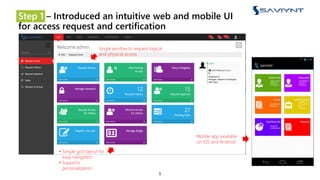
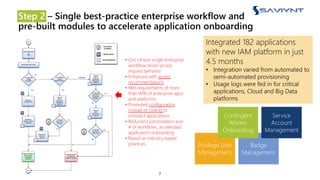
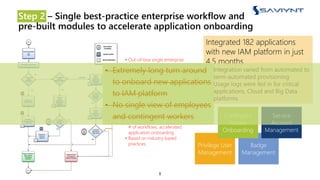
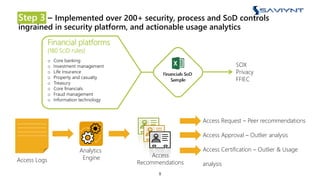
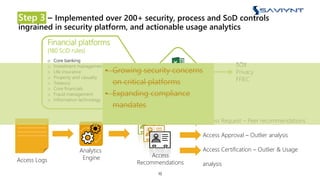
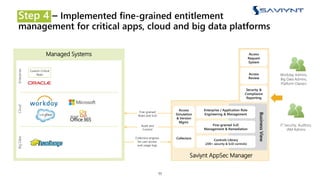
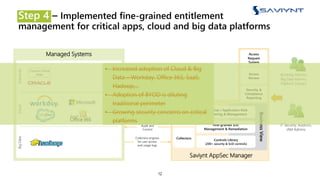
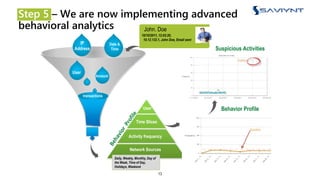
The document outlines the evolution of Identity and Access Management (IAM) at a major U.S. financial service, emphasizing challenges with scalability, integration, and user intuitiveness in existing systems. It introduces Saviynt's IAM solutions, which provide fine-grained access management and improved onboarding processes, resulting in the integration of 182 applications within 4.5 months and significant compliance and security enhancements. Furthermore, the implementation of advanced analytics and insider threat management aims to address growing security concerns and improve operational efficiency.