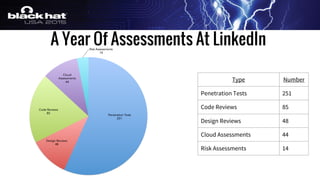
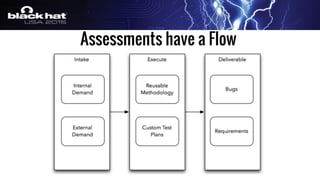
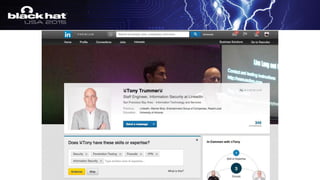
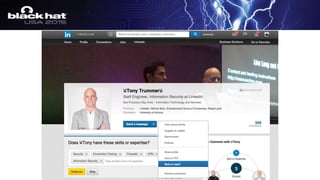
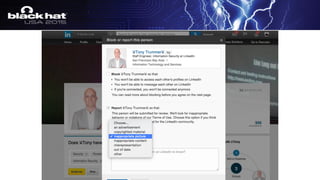
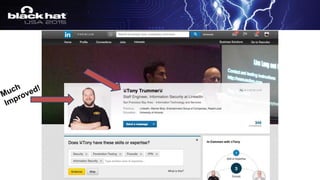
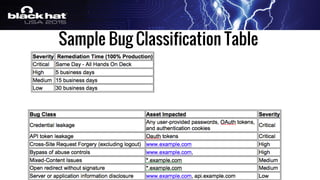
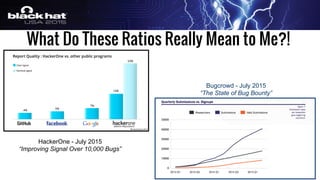
The document outlines a tactical approach to application security at LinkedIn, detailing essential elements like application assessments, incident response strategies, and bug bounty programs. It emphasizes iterative processes, operational excellence, and collaboration across teams while maintaining a focus on real-time risk mitigation. The authors advocate for a tactical mindset as a means to effectively manage security challenges and foster positive relationships with researchers.