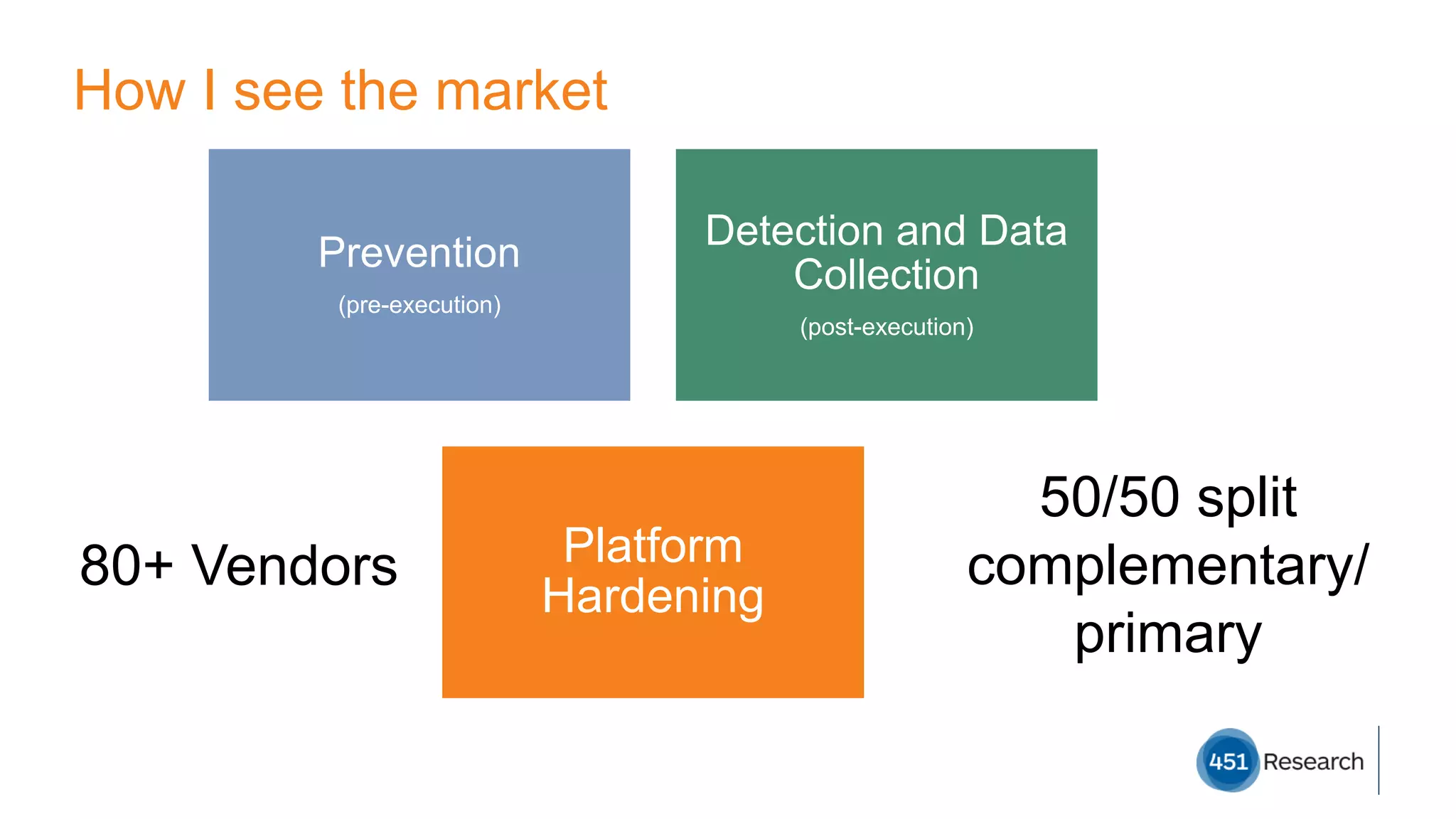
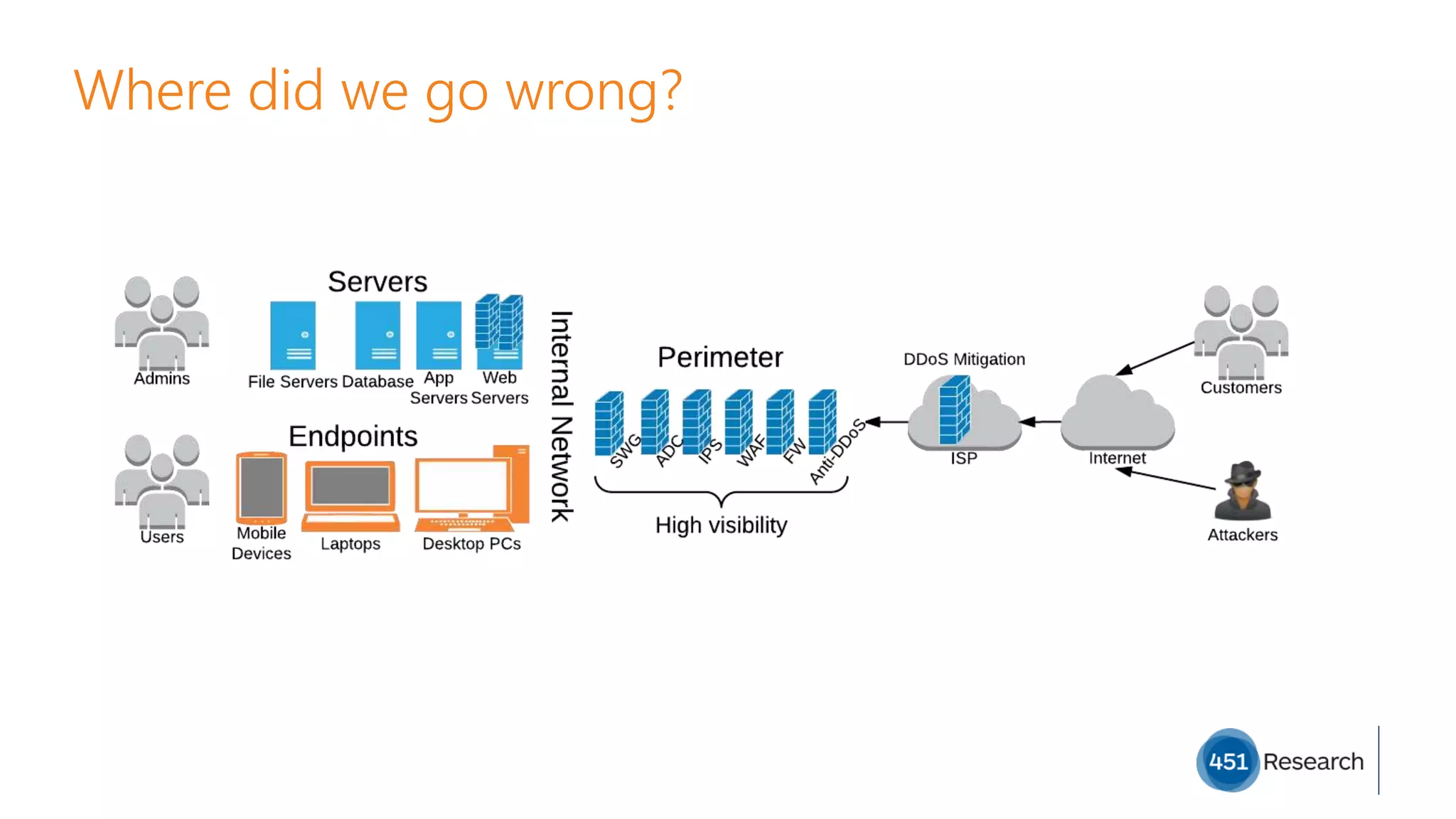
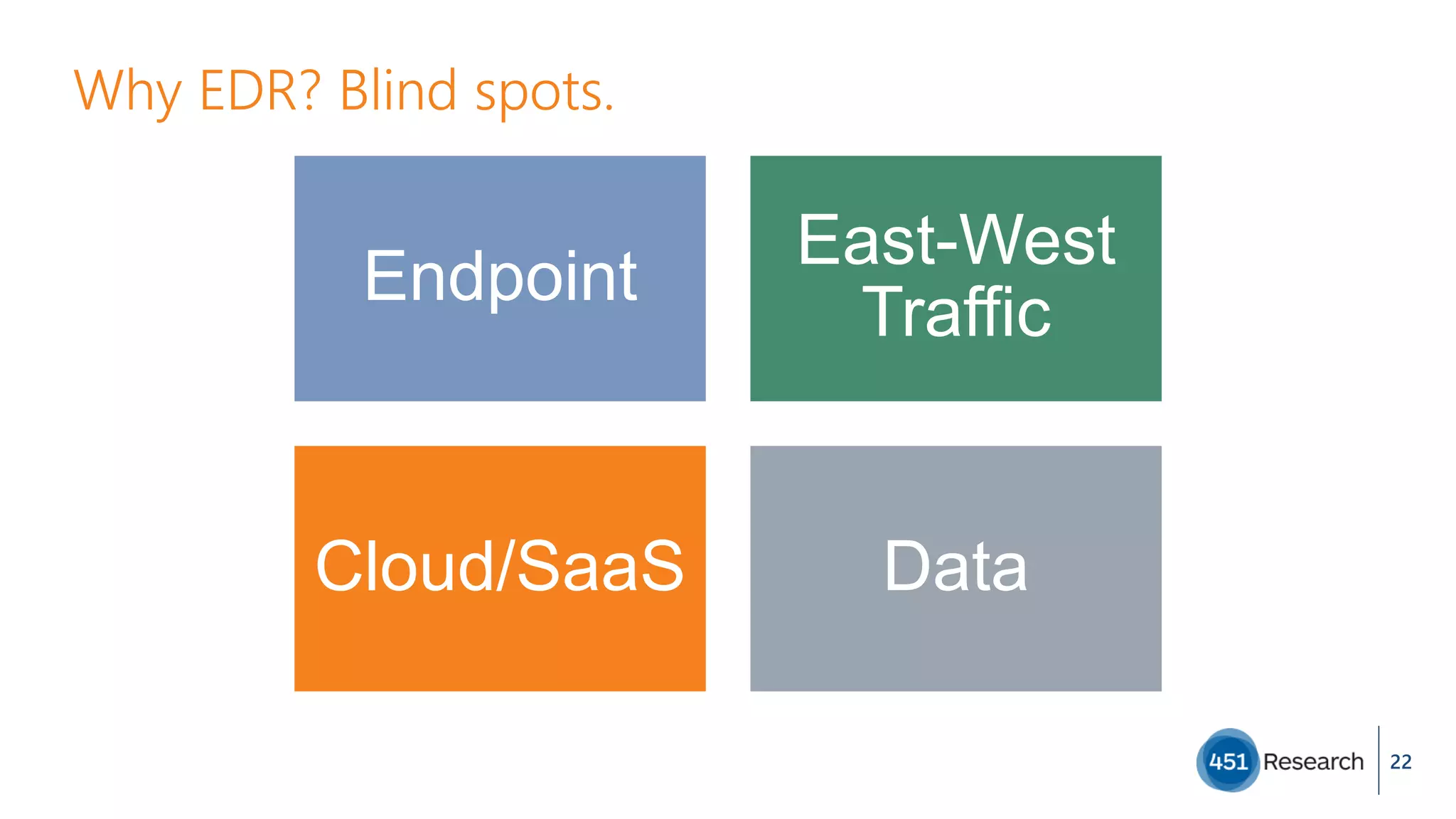
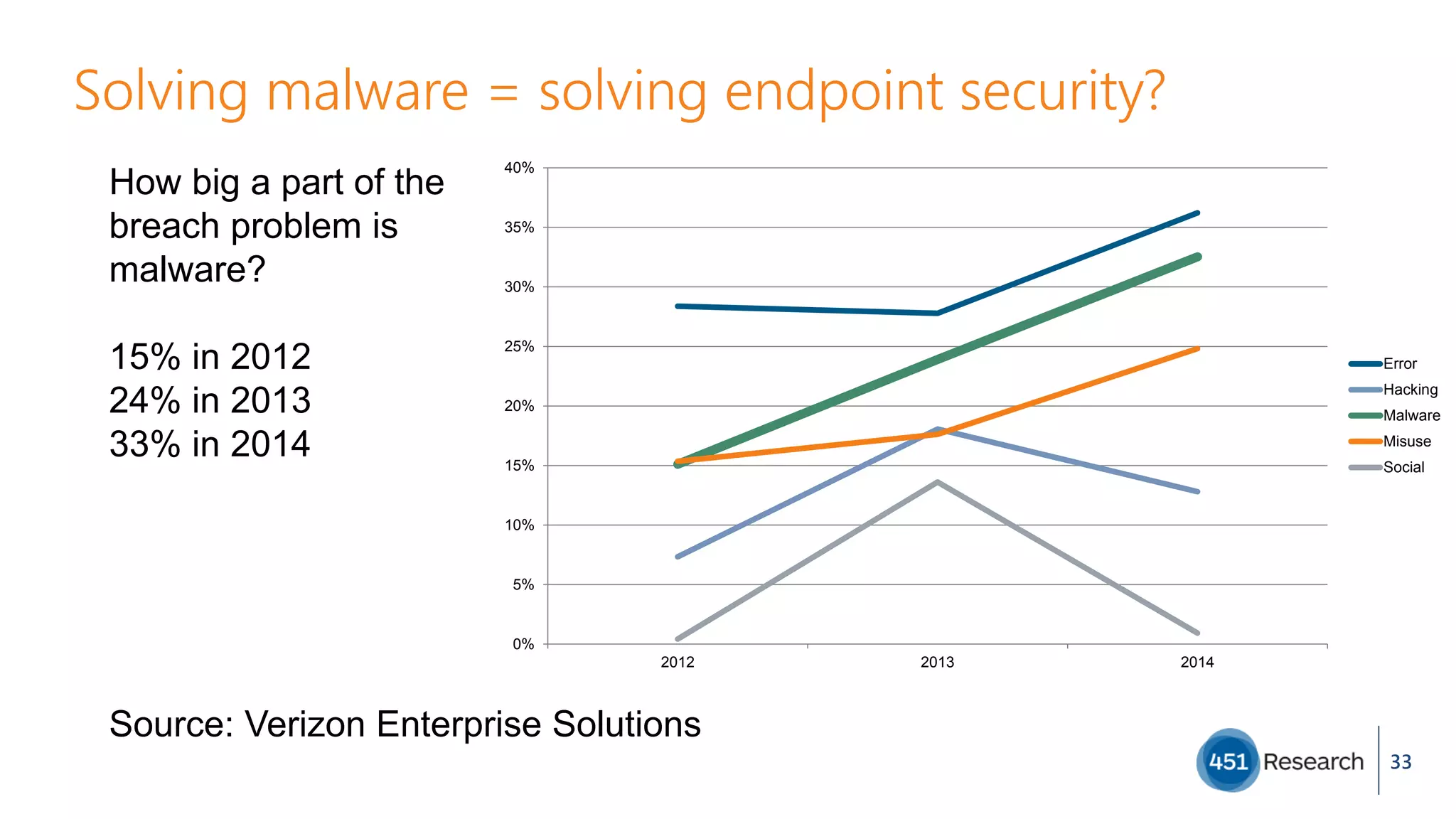
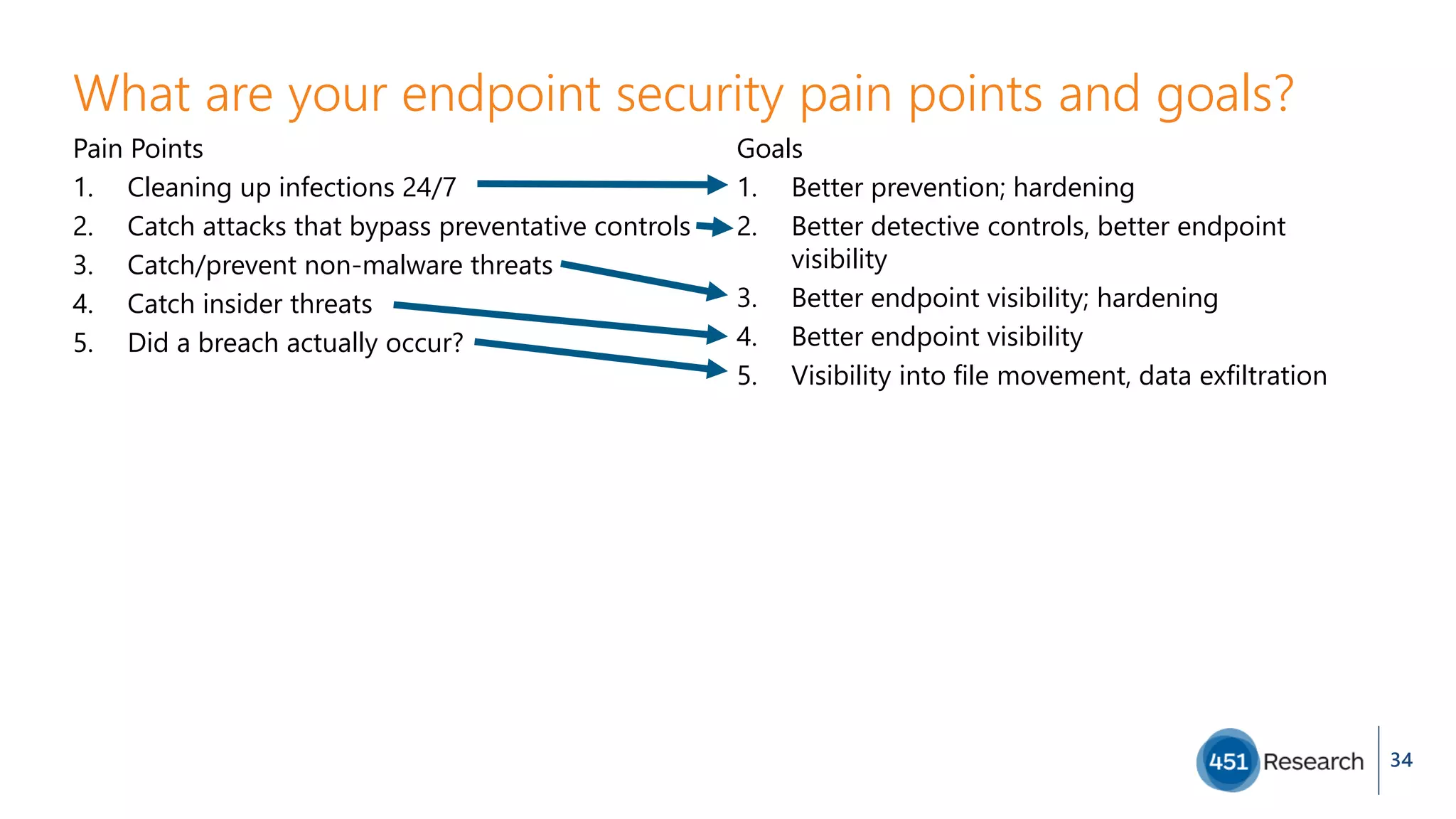
The document discusses the complexities of malware prevention, highlighting the importance of endpoints as critical points of vulnerability within organizations. It outlines a roadmap for improving endpoint security, including developing better detection techniques and enhancing system visibility while addressing non-malware threats. Additionally, it emphasizes the need for root cause analysis and process improvements to effectively tackle the evolving landscape of cybersecurity threats.