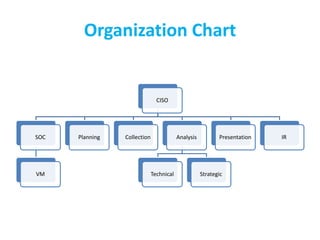
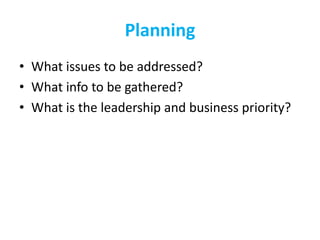
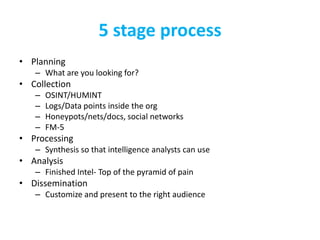
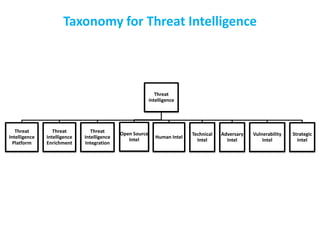
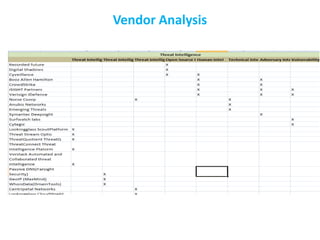
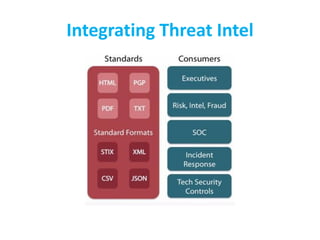
The CISO Platform Decision Summit, held in New Delhi, focused on the growing field of threat intelligence, projected to reach $1.5 billion in 2018. The discussions included key elements of actionable intelligence, types of intelligence, and a structured five-stage process for threat intelligence management. Prominent vendors were analyzed across various categories, and the document emphasized the importance of sharing and integration in building effective threat intelligence programs.