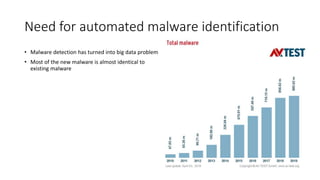
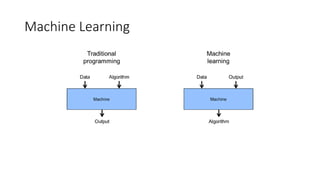
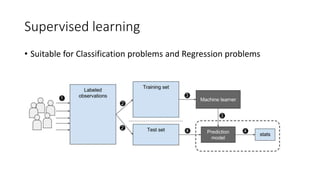
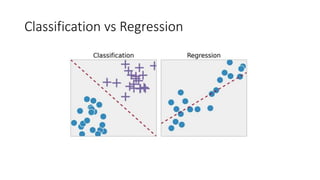
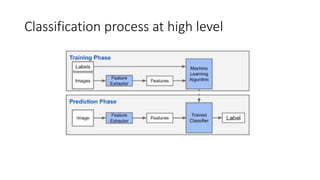
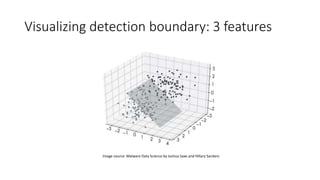
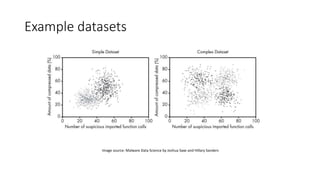
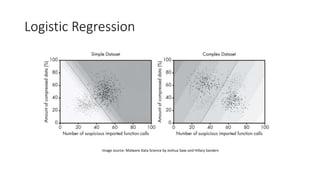
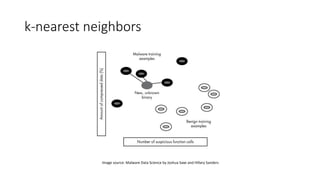
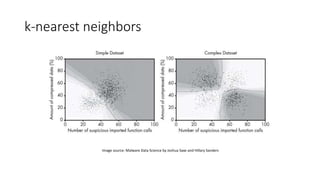
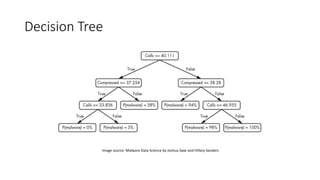
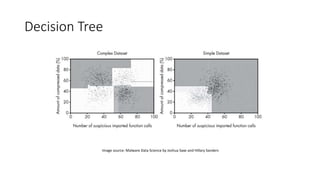
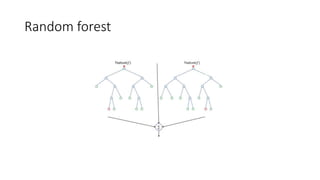
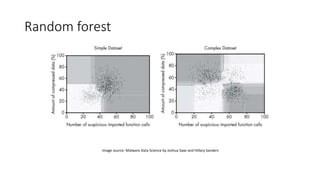
The document discusses the process of malware identification using machine learning, outlining the necessity for automated malware analysis due to the increasing complexity of malware threats. It details the stages of malware detection by antivirus companies, which include in-house analysis, training machine learning models on both benign and malicious samples, and real-time classification on customer machines. Various machine learning algorithms such as logistic regression, k-nearest neighbors, decision trees, and random forests are identified as tools for improving classification efficacy.