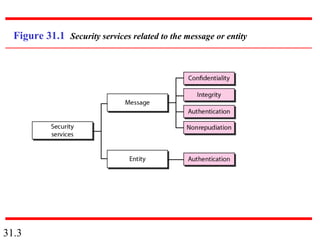
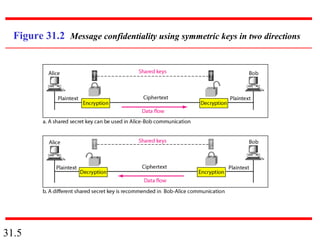
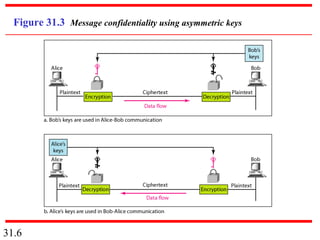
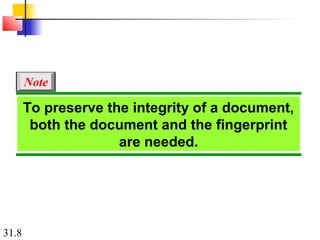
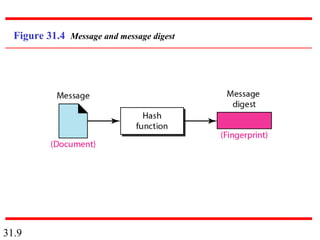
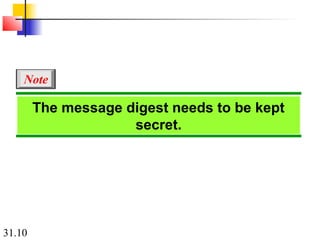
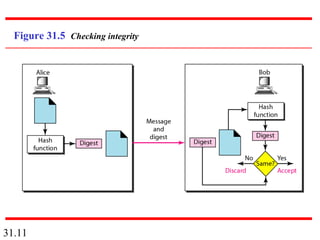
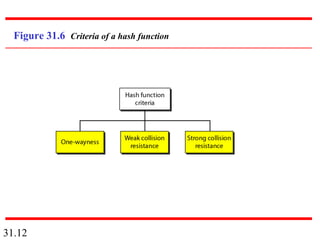
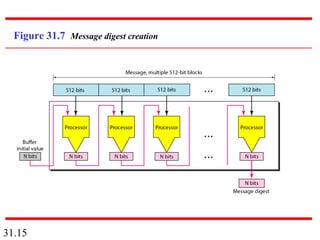
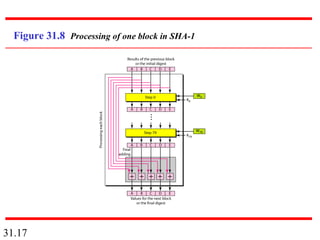
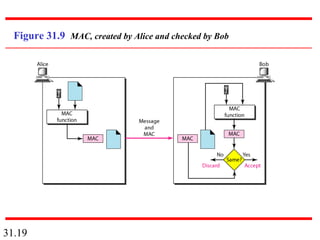
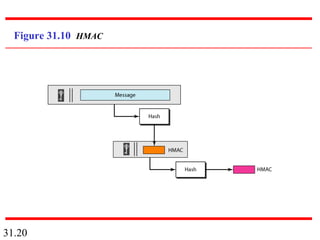
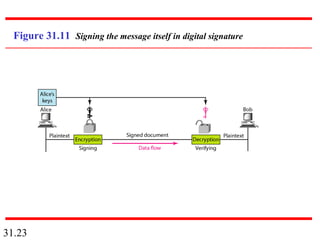
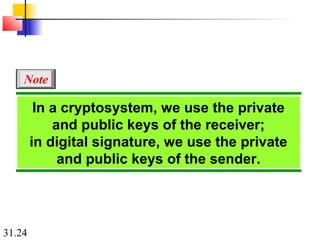
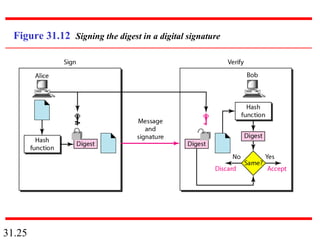
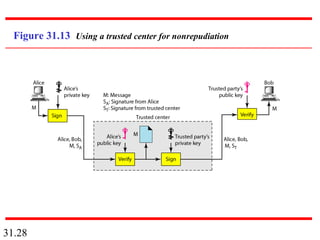
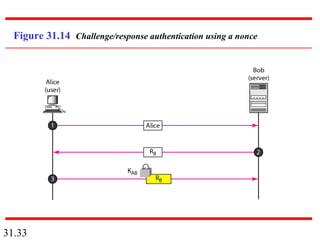
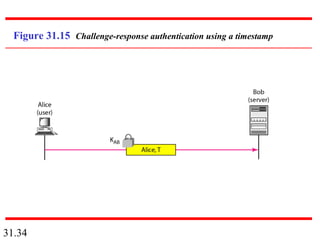
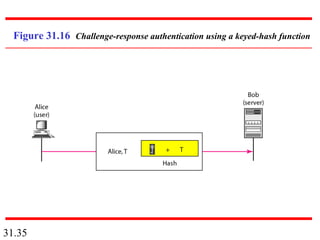
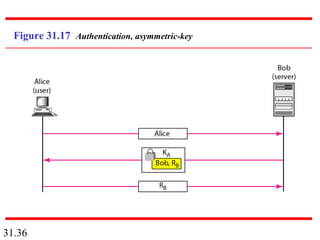
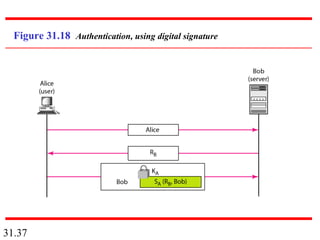
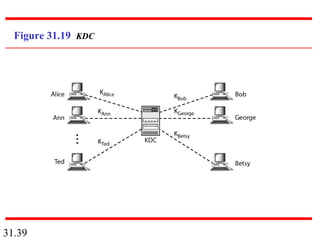
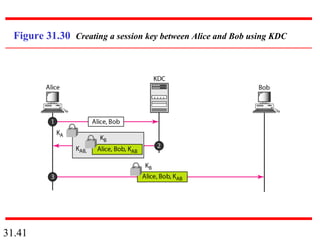
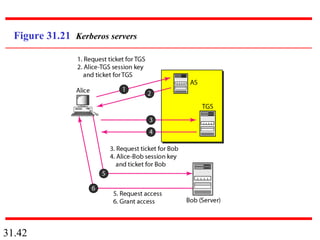
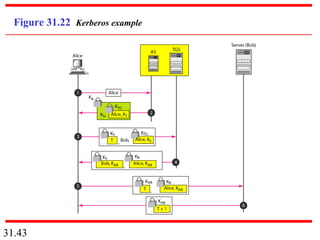
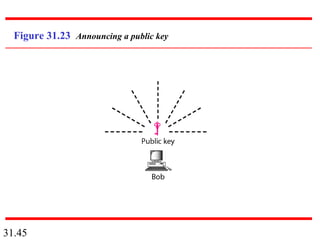
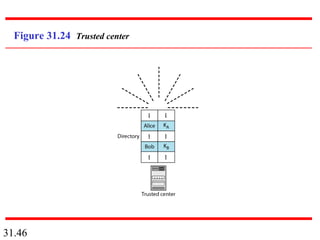
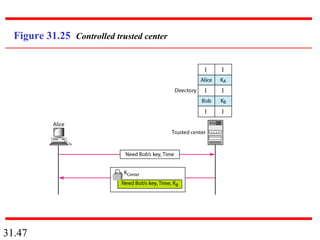
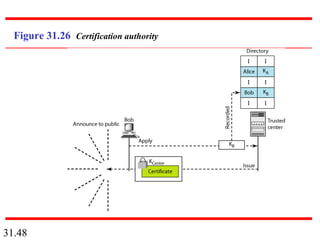
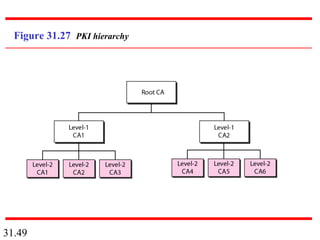
Network security can provide five services: message confidentiality, message integrity, message authentication, message nonrepudiation, and entity authentication. These services use cryptographic techniques like encryption, hashing, digital signatures, and challenge-response authentication to protect messages and verify identities on a network. Key management is also important to securely distribute and maintain the cryptographic keys needed to provide these security services.