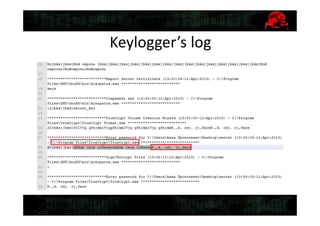
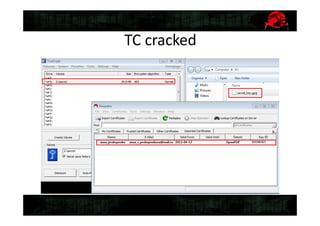
This document summarizes a digital forensics case discussion between two security experts, Anton and George. They describe recovering data from a damaged hard drive image to help an employee named Anna avoid legal trouble. Techniques discussed include recovering the partition table, system files to obtain machine details, searching for malware, and analyzing a keylogger log file. Ultimately they were able to obtain secret key files that were potentially used in a crime, helping resolve Anna's case.

![/wh0x41mi
George Lagoda
Security expert
Pentester
Interests: [deep|web]penetrations,
revers, forensics,
Work at . . .](https://image.slidesharecdn.com/2-150409134645-conversion-gate01/85/5-2-Digital-forensics-3-320.jpg)
![Digital forensics, The.
[quote]
Digital forensics (sometimes known as
digital forensic science) is a branch of forensic
science encompassing the recovery and
investigation of material found in digital devices,
often in relation to computer crime.
[/quote]](https://image.slidesharecdn.com/2-150409134645-conversion-gate01/85/5-2-Digital-forensics-4-320.jpg)


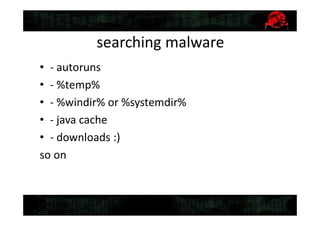
![Why also we need data recovery
• Damaged discs
• Damaged images
• Deleted files
• Something encrypted
• Something partially missing
• Something damaged by malware
[…]
All these things can omit evidence of crime](https://image.slidesharecdn.com/2-150409134645-conversion-gate01/85/5-2-Digital-forensics-8-320.jpg)



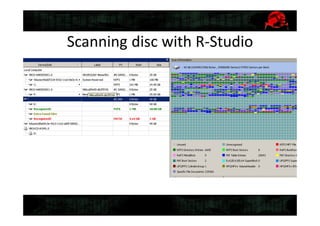
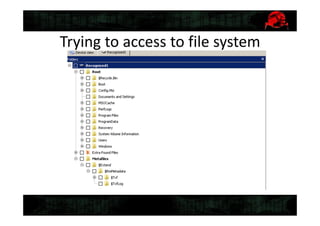


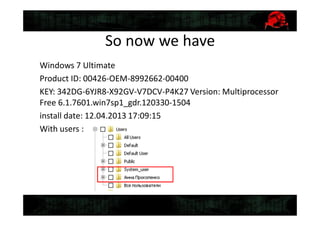
![Gathering system info
• Recovering files from
WindowsSystem32config
– System, Software, Security, Sam,
• Recovering NTUSER.dat from
Users[username]
• Downloading MiTec Windows Registry
Recovery(www.mitec.cz/wrr.html)
• Obtaining system info](https://image.slidesharecdn.com/2-150409134645-conversion-gate01/85/5-2-Digital-forensics-16-320.jpg)