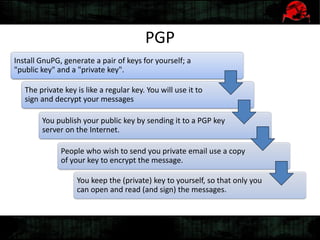
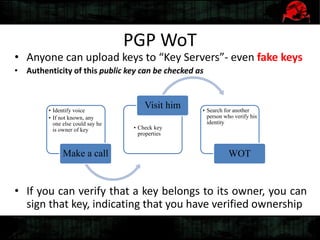
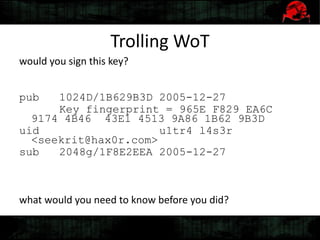
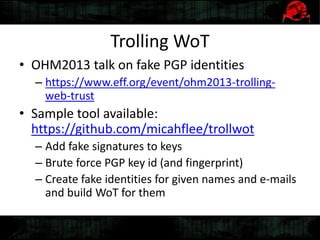
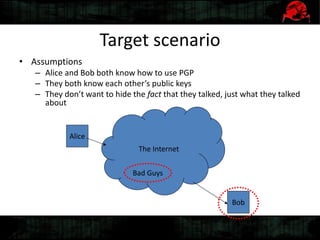
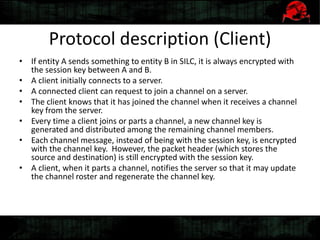
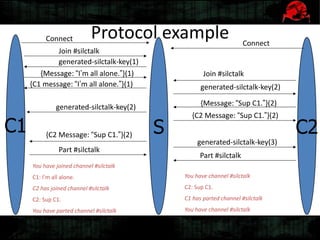
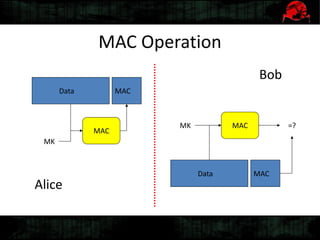
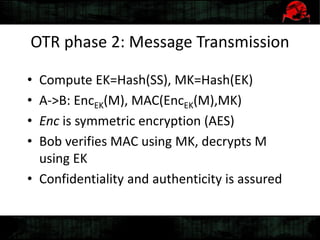
Dennis Gamayunov discusses the history of undercover communications and encryption techniques. He describes how early systems like BBS, SMTP, and IRC lacked privacy and authentication. PGP introduced public-key cryptography for encrypting and signing messages. The Web of Trust model allows people to verify ownership of keys. However, fake keys and identities can undermine the system. The SILC protocol provides encryption for chat channels. OTR messaging provides forward secrecy, deniability, and no third-party proofs. Future work includes improving usability and expanding these techniques to group messaging.