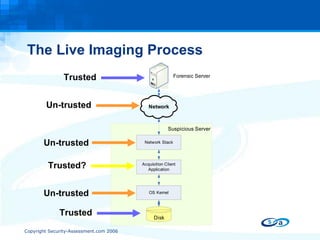
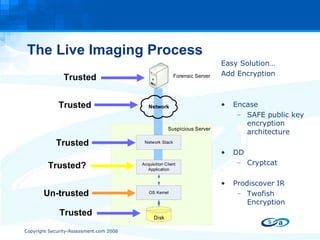
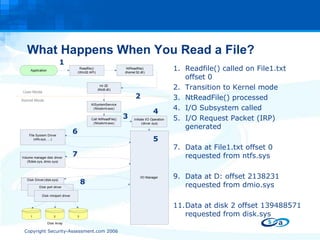
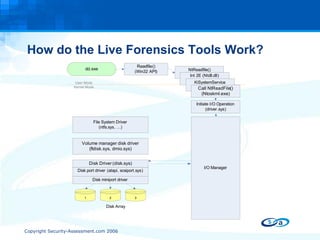
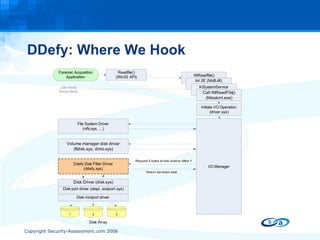
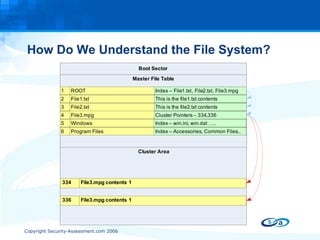
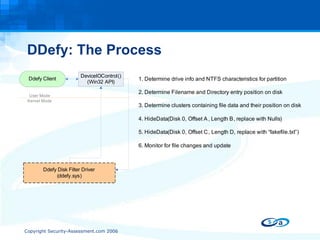
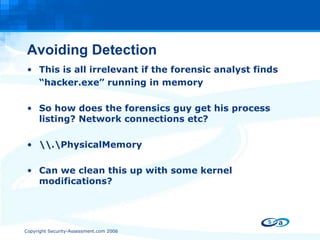
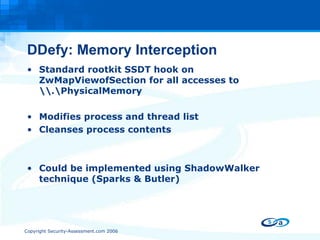
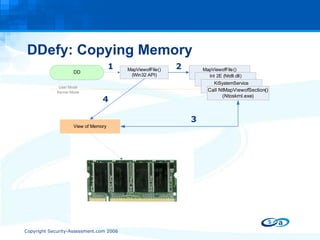
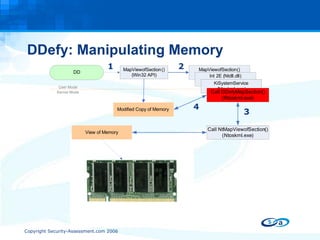
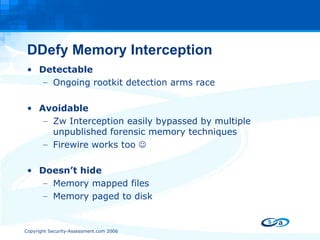
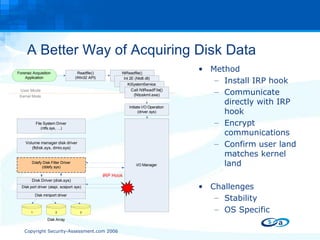
The document discusses anti-forensic rootkits and techniques that can manipulate digital evidence collected through live forensic imaging. It presents DDefy, a proof-of-concept anti-forensic rootkit that intercepts disk read requests and modifies the data returned to hide sensitive information from live forensic tools. DDefy demonstrates that current live imaging methods are insufficient to guarantee collection of untainted evidence, as they rely on the compromised system to provide the data. Better techniques are needed to directly acquire disk data and confirm it matches the kernel and userland views.



















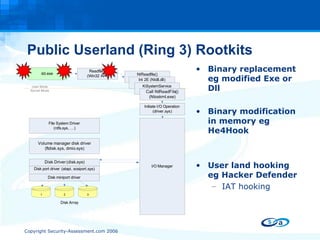
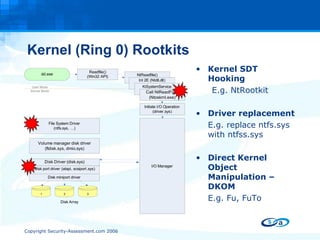
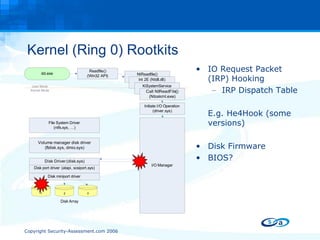
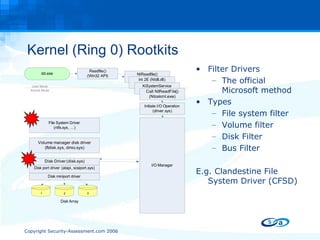





![Questions ? http://www.security-assessment.com [email_address]](https://image.slidesharecdn.com/antiforensic-rootkits-17017/85/Anti-Forensic-Rootkits-48-320.jpg)
