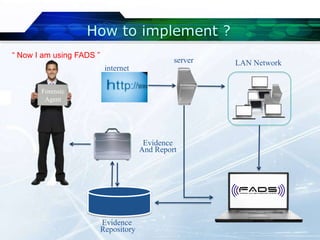
The document describes FADS (Forensic Agent Detection System), a digital forensics tool developed by the Security Research Group at Universiti Sains Malaysia. FADS allows for real-time network monitoring, detection of cyber attacks, and collection of evidence from server and client systems. It features several interfaces for forensic agents, notification of attacks, and storage of evidence in multiple databases for reporting purposes. FADS provides an easier way for law enforcement and organizations to conduct network forensics investigations and gather evidence of cyber crimes.