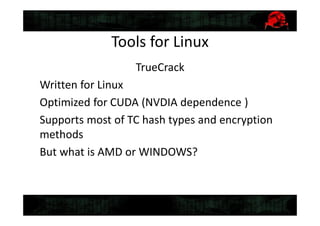
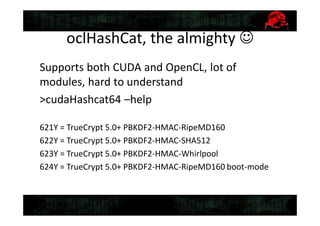
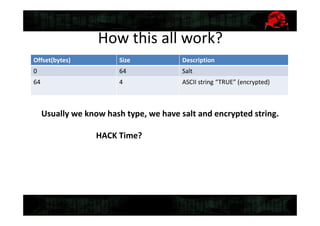
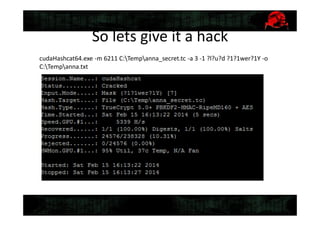
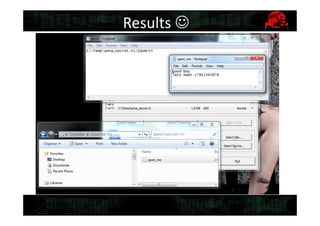
This document discusses tools for recovering a partially lost Truecrypt password using a GPU when 4-5 symbols of the password are unknown. It describes the tools TrueCrack and oclHashCat, how they work by using the salt and encrypted string in the Truecrypt header to brute force possible passwords, and provides an example command to use oclHashCat to try passwords with unknown case and symbols replaced with wildcards.

![/wh0x41mi
George Lagoda
Security expert
Pentester
Interests: [deep|web]penetrations,
revers, forensics,
Work at . . .](https://image.slidesharecdn.com/dailyhacktruecrypt-150409134639-conversion-gate01/85/5-Daily-hack-Truecrypt-2-320.jpg)
![What I had?
• Partialy lost TC passwd
• 4-5 symbols lost or we have something like:
[Y|y]a[L|l]ublu[S|s]vou[K|k]isku
So we either do not remember 1-2-3-4-5
symbols
Or Don’t remember symbols’ case](https://image.slidesharecdn.com/dailyhacktruecrypt-150409134639-conversion-gate01/85/5-Daily-hack-Truecrypt-5-320.jpg)