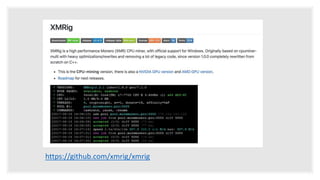
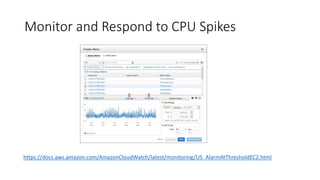
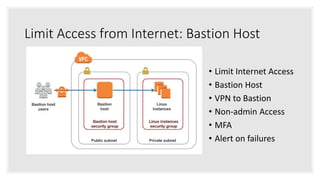
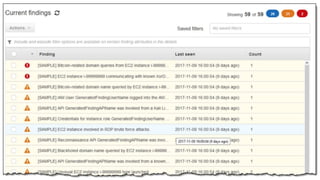
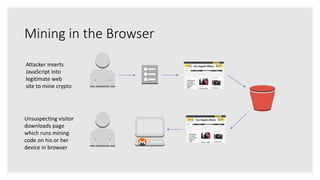
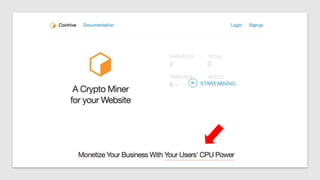
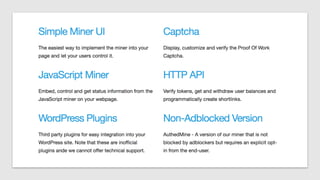
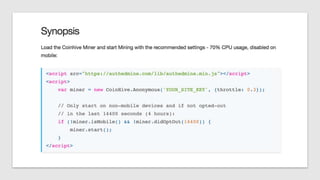
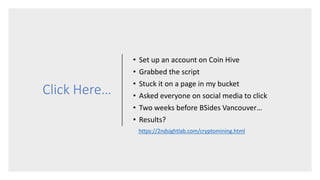
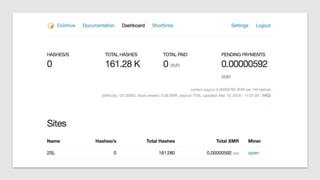
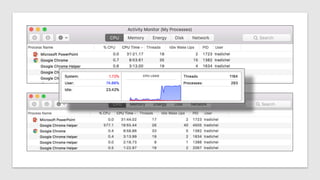
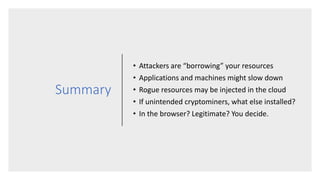
The document discusses how attackers can use cloud resources and websites to secretly mine cryptocurrency without permission. Attackers can upload cryptomining software to virtual machines in the cloud, slowing them down. They can also insert cryptomining JavaScript into legitimate websites, using visitors' CPUs without their knowledge. Defenses include monitoring for unusual processes, services, and network traffic that could indicate mining, as well as preventing public access to cloud resources and ensuring websites' code is secure. Vigilance is needed to detect unintended mining activities.

![Agenda
• Crypto Mining + Cryptojacking
• Some malicious examples…
• How they [may have] happened
• Indicators of compromise
• What you can do about it](https://image.slidesharecdn.com/cryptominersinthecloud-180313230318/85/Crypto-Miners-in-the-Cloud-2-320.jpg)





![Bypass the
Ransomware
• Figured out how to get to […] in UI
• Open Windows Explorer
• Recursively make files readable from root
• Woot! (Some things still inaccessible…)
• Navigate and open cmd.exe
• Usually C:WindowsSystem32cmd.exe](https://image.slidesharecdn.com/cryptominersinthecloud-180313230318/85/Crypto-Miners-in-the-Cloud-12-320.jpg)