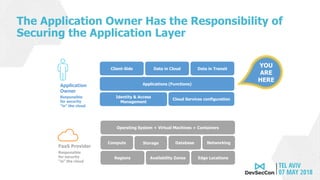
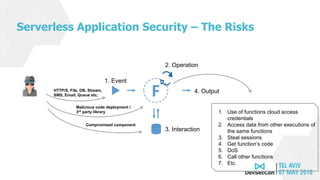
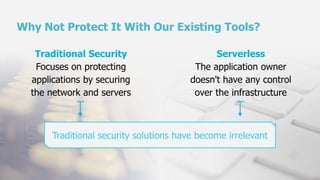
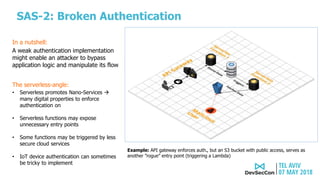
The document discusses serverless application security, highlighting the evolving responsibilities of application owners and the inadequacy of traditional security tools. It outlines the top 10 most common weaknesses in serverless environments and emphasizes the importance of protecting against these vulnerabilities through proper permissions, monitoring, and secure practices. The author, Avi Shulman, leverages his extensive cybersecurity experience to guide developers in enhancing their serverless applications' security.