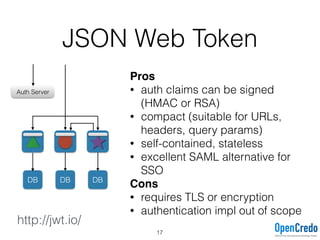
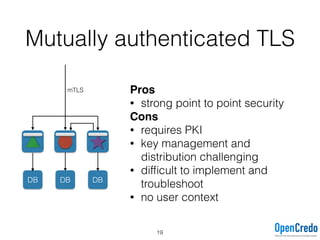
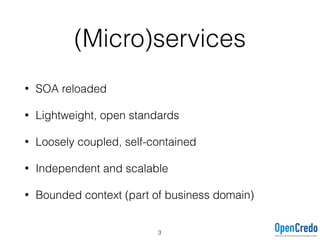
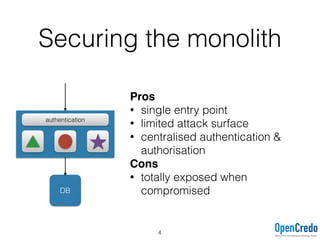
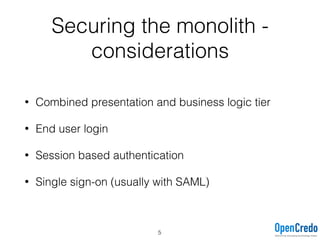
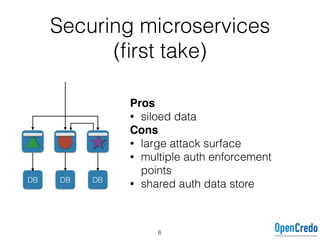
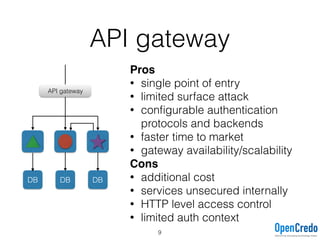
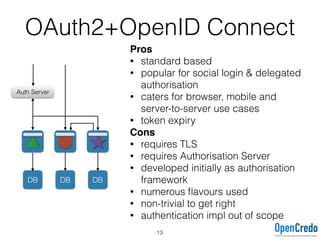
The document provides insights on securing microservices using Play and Akka HTTP, discussing various authentication and authorization strategies applicable to microservices architecture. It outlines the pros and cons of different security measures, including API gateways, OAuth2, OpenID Connect, and mutual TLS, while emphasizing the importance of considering project requirements and the evolving technology landscape. Key takeaways highlight the complexity of securing microservices and the necessity for tailored security solutions.





![Akka HTTP
• authenticateBasicX directives
• http://doc.akka.io/docs/akka-stream-and-http-experimental/2.0-M2/scala/http/routing-dsl/directives/
security-directives/authenticateBasic.html#authenticatebasic
def myUserPassAuthenticator(credentials: Credentials): Future[Option[String]] =
credentials match {
case p @ Credentials.Provided(id) =>
Future {
// potentially
if (p.verify("s3cr3t")) Some(id)
else None
}
case _ => Future.successful(None)
}
val route =
Route.seal {
path("secured") {
authenticateBasicAsync(realm = "secure site", myUserPassAuthenticator)
{ userName =>
complete(s"The user is '$userName'")
}
}
}
12](https://image.slidesharecdn.com/securingmicroservicesusingplayandakkahttp-160128131658/85/Securing-Microservices-using-Play-and-Akka-HTTP-12-320.jpg)

:
AuthenticationDirective[T]
Usage the same as HTTP basic but requires validating access
token retrieved from the header (not supported natively).
15](https://image.slidesharecdn.com/securingmicroservicesusingplayandakkahttp-160128131658/85/Securing-Microservices-using-Play-and-Akka-HTTP-15-320.jpg)