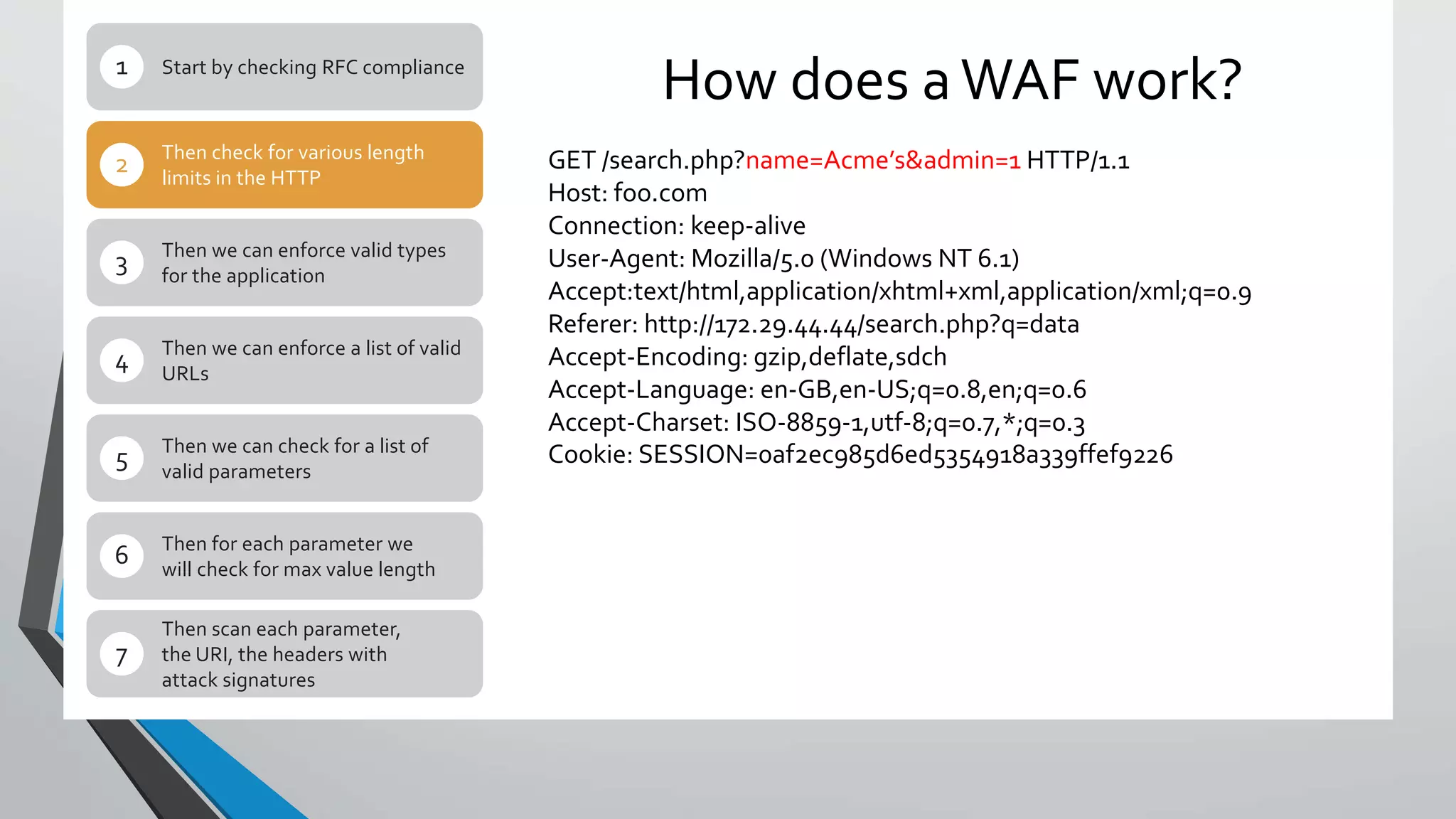
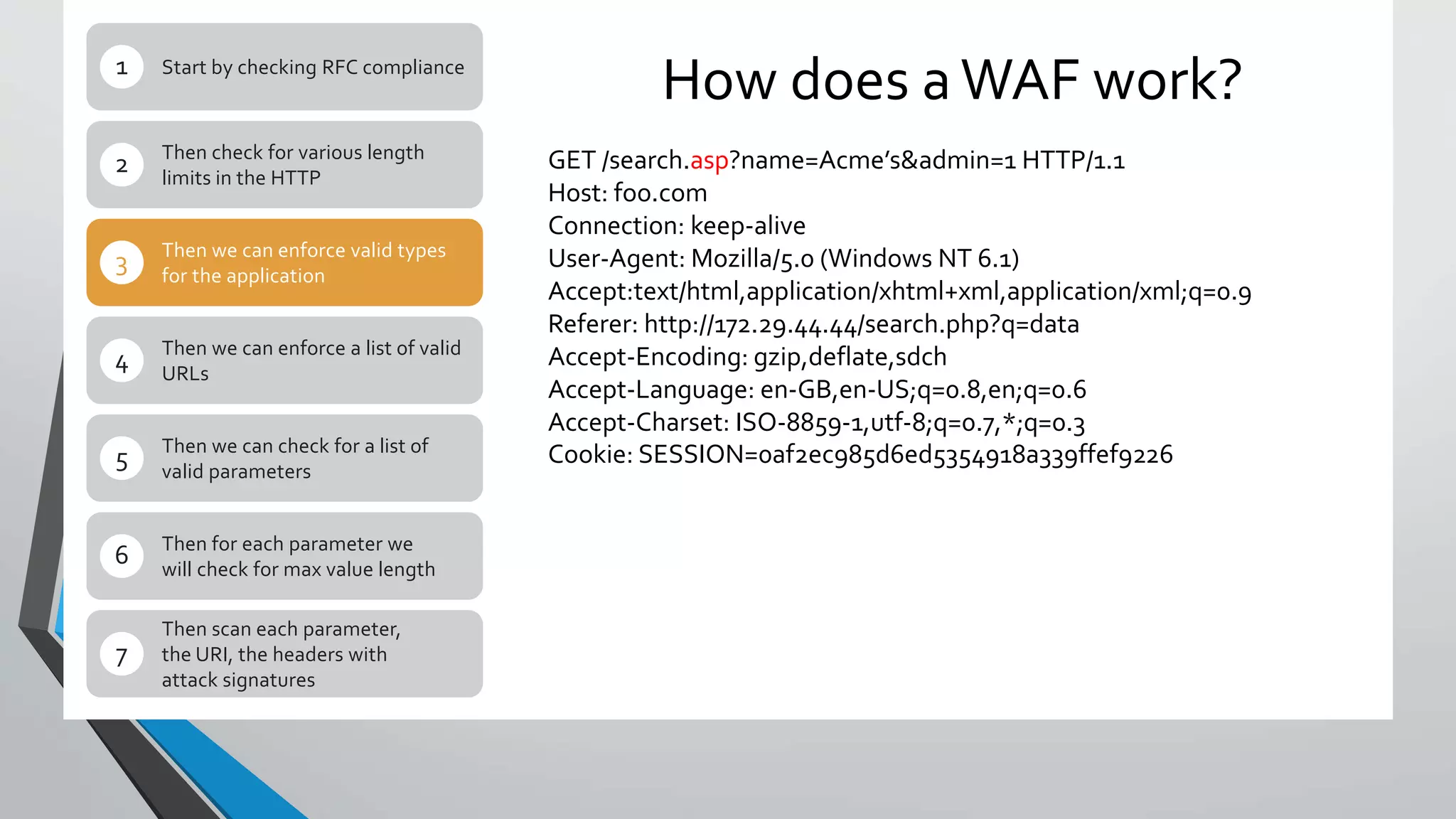
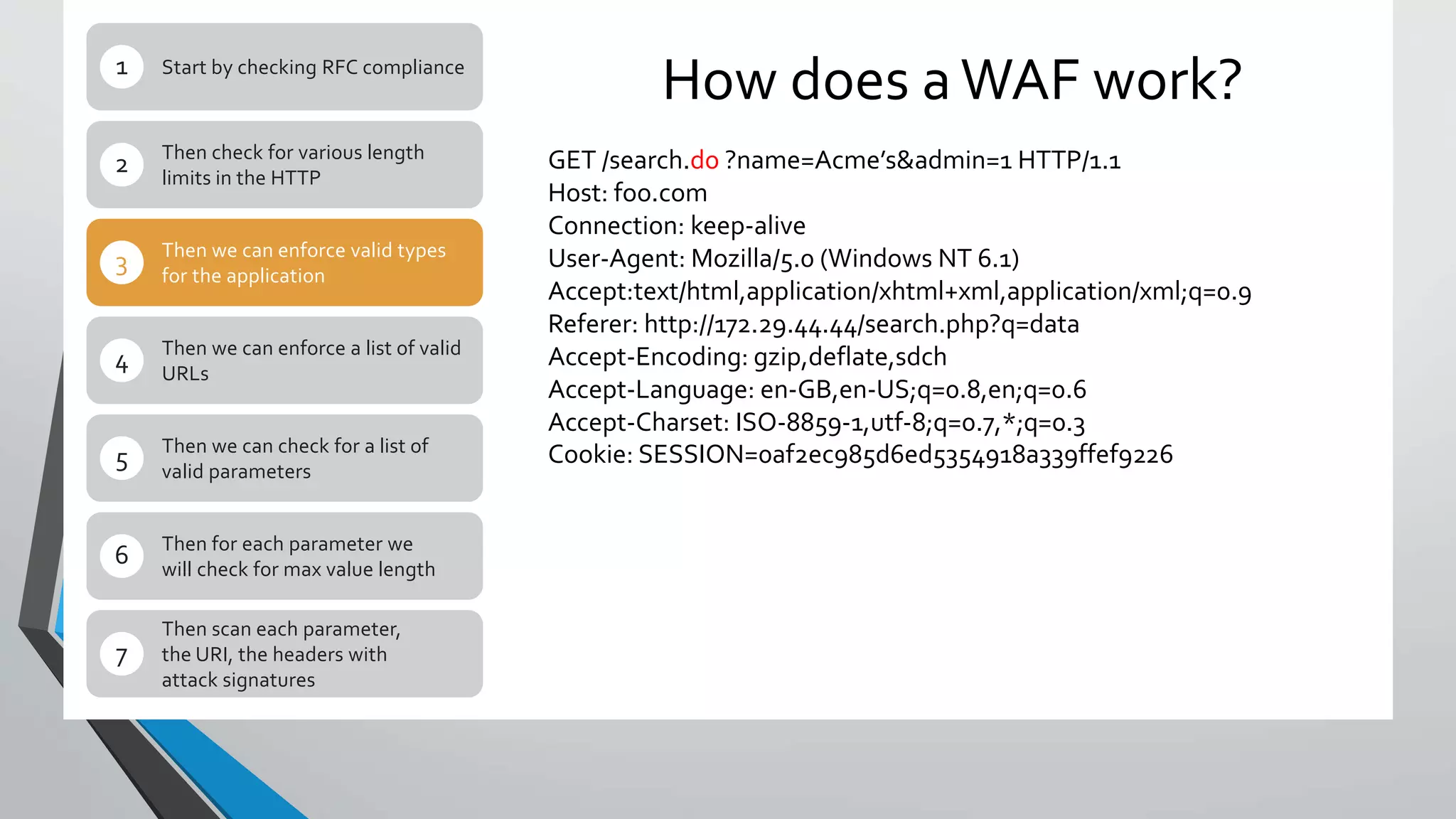
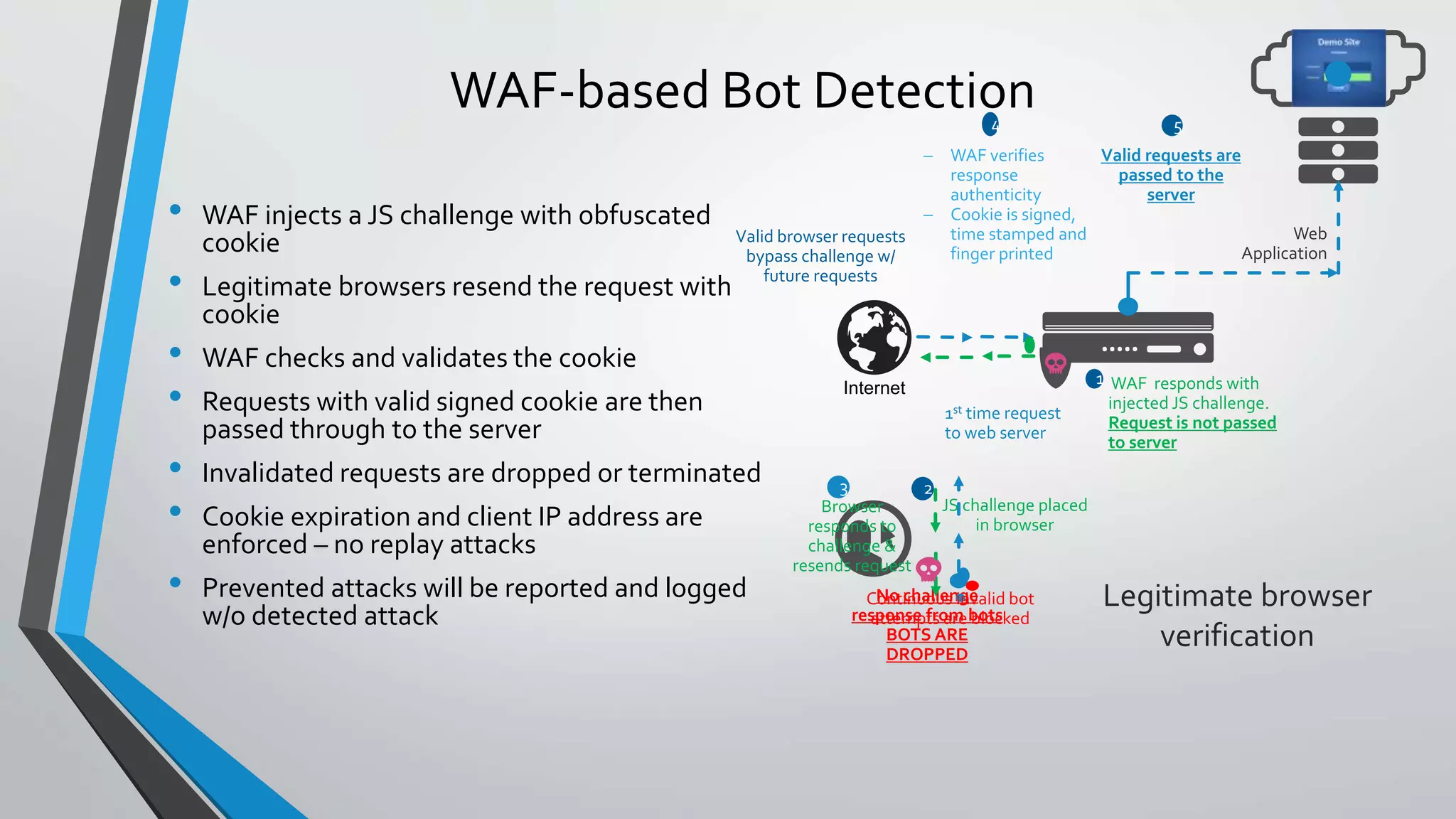
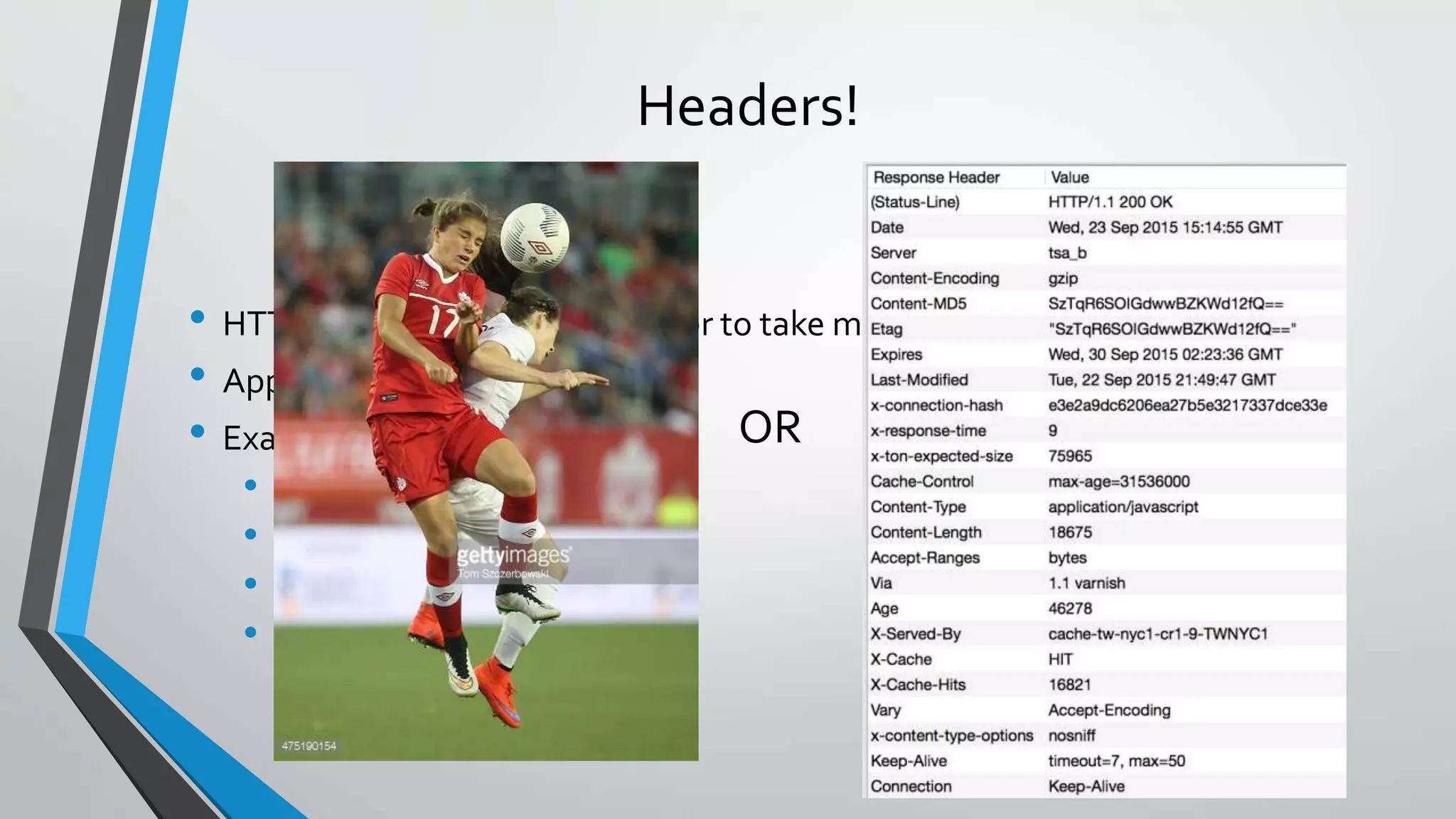
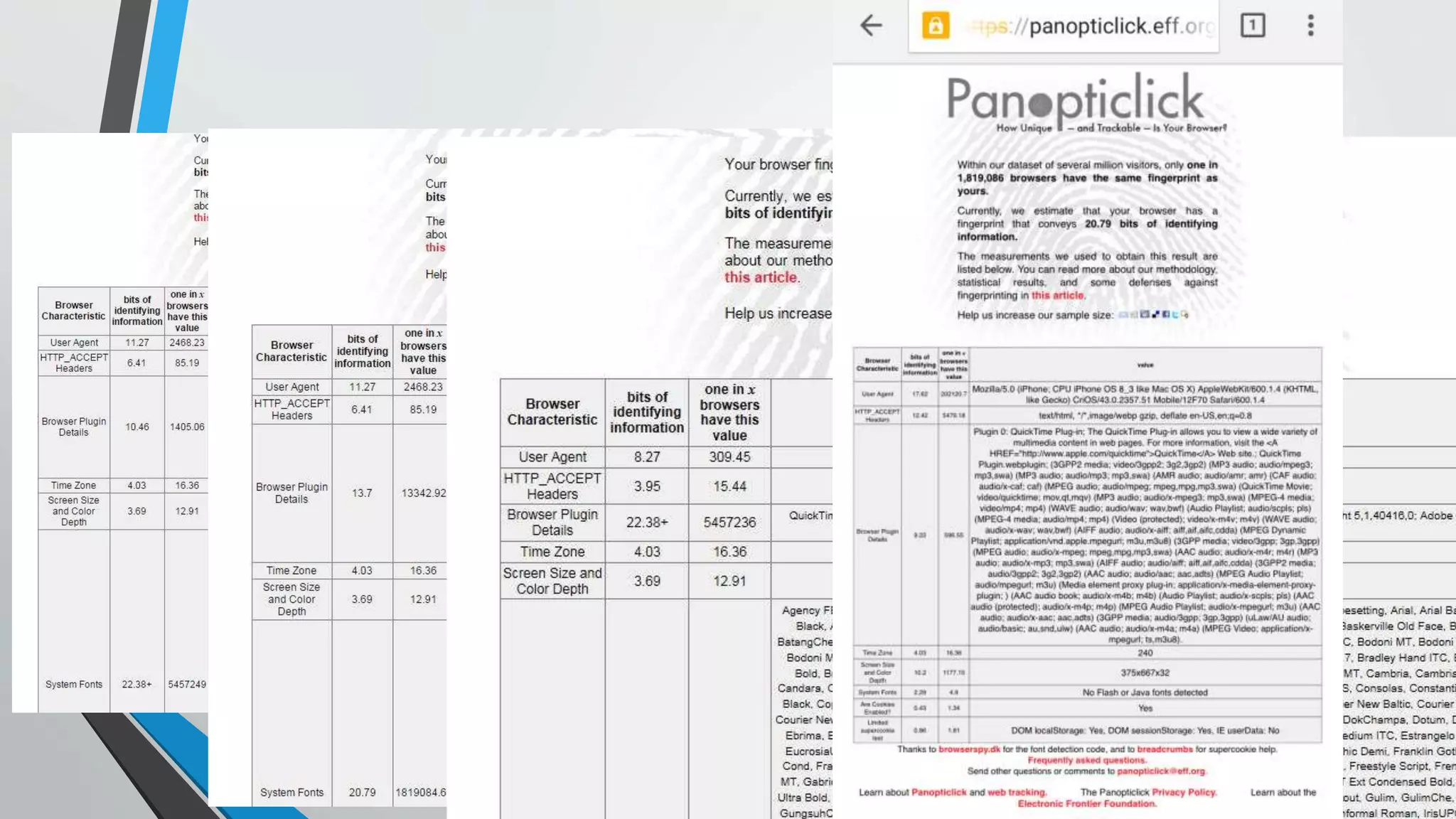
The document describes how traditional web application firewalls (WAFs) work by checking requests against rules for things like RFC compliance, URL and parameter validation, length limits, and attack signatures. However, the document argues this approach will become outdated as applications evolve and new attacks emerge. A new approach is needed for WAFs to stay relevant and enhance application security.