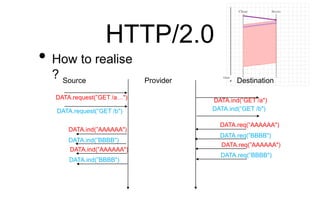
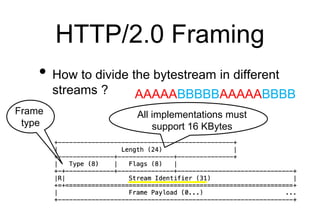
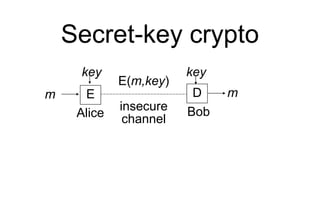
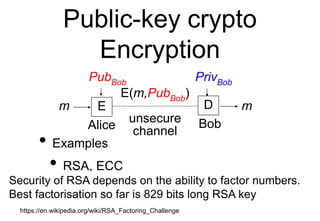
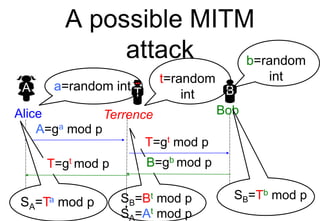
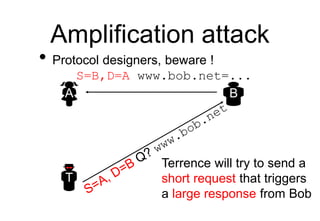
This document provides a high-level summary of Transport Layer Security (TLS):
- TLS establishes an encrypted connection between a client and server through a handshake that authenticates the server and negotiates encryption parameters.
- The handshake includes the client sending a ClientHello, the server responding with a Certificate and ServerHello, and agreeing on encryption keys.
- Once established, the connection uses the record protocol to securely transmit encrypted and authenticated data between the client and server. Sessions can also be resumed later using the agreed session ID.