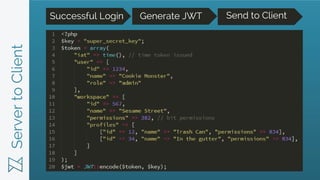
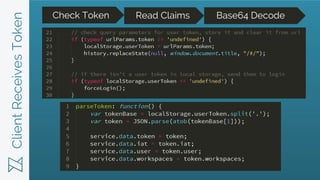
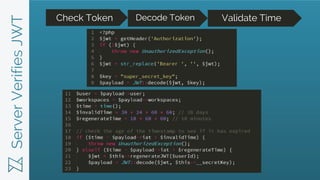
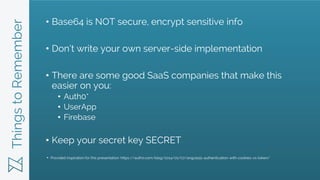
JWTs provide a more secure and scalable alternative to cookie-based authentication. JWTs contain encrypted user information that is verified on the client-side and transmitted with each request, avoiding the need for database lookups on the server-side. In contrast, cookies require server-side sessions and database lookups to validate the user on each request. JWTs also enable cross-domain requests and work across mobile and web platforms, while cookies have limitations in these areas. Developers are advised to use a third-party service to handle JWT generation and verification rather than implementing it themselves.