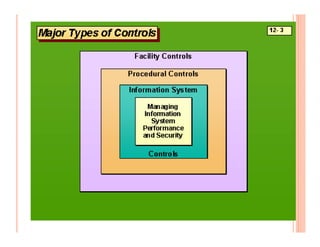
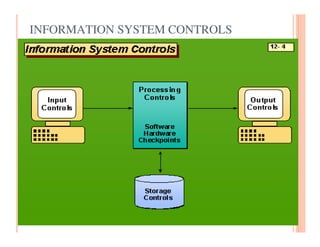
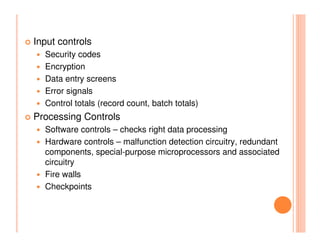
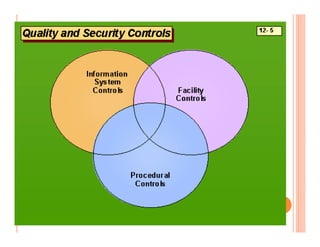
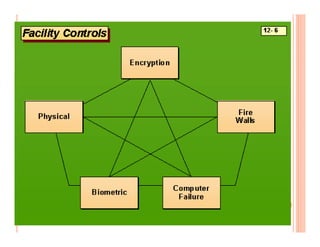
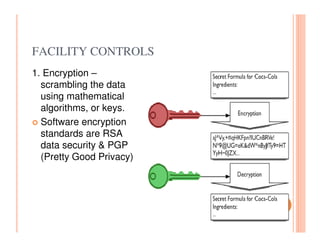
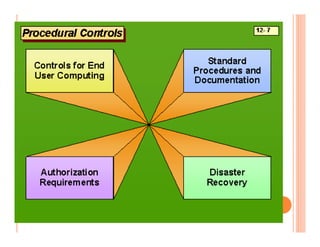
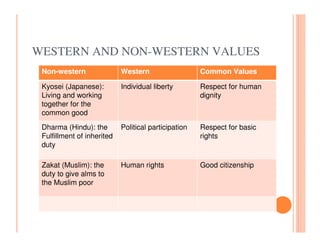
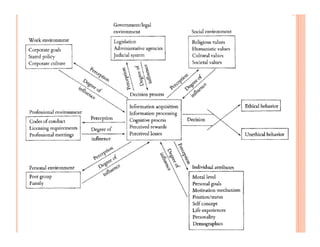
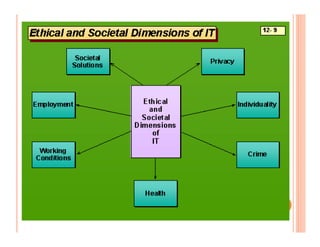
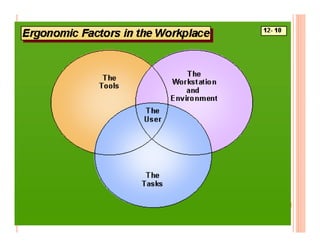
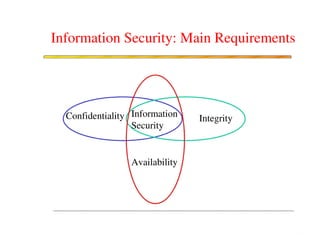
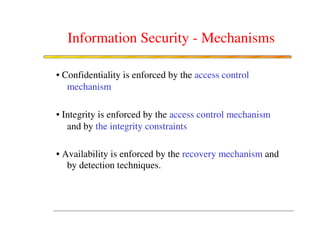
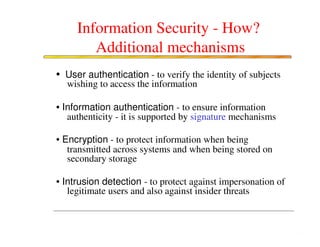
The document discusses various security challenges and controls related to information technology and e-commerce. It covers privacy, authenticity, integrity, and reliability as key security requirements. It then describes different types of controls including input controls, processing controls, output controls, storage controls, facility controls like encryption and firewalls, procedural controls, and auditing. Key points around spoofing, outsourcing, information protection goals of confidentiality, integrity and availability are also summarized.