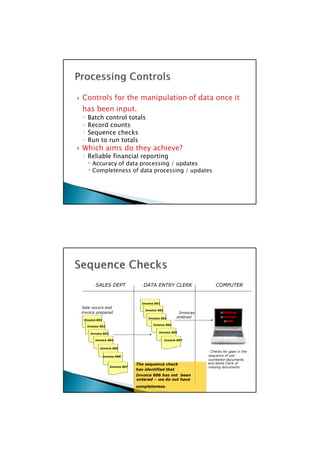
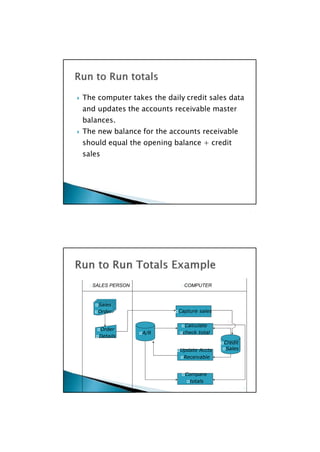
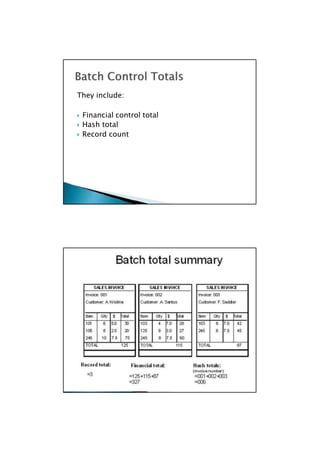
This document discusses internal controls for computerized accounting information systems. It describes general controls that apply across systems, such as policies for access, backup procedures, and segregation of duties. It also discusses application controls that operate within specific systems or processes to ensure proper authorization, recording, completeness and accuracy of transactions. Examples provided include input and output edit checks, sequence checks, and comparison of control totals. Threats to internal controls like fraud or system errors are also mentioned.