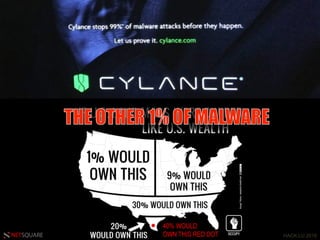
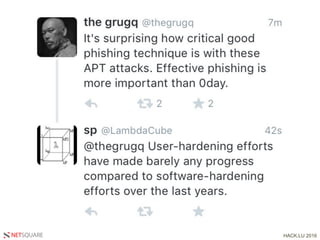
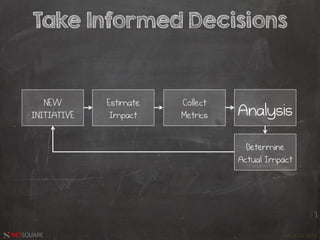
The document discusses the evolution of information security threats and defenses, highlighting a shift from individual efforts to team-oriented approaches in combating attacks. It emphasizes the need for proactive security measures, including the importance of metrics, user understanding, and intelligence-driven strategies. The speaker advocates for a comprehensive security framework that adapts to evolving attack strategies rather than relying on reactive measures.