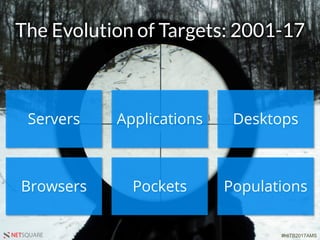
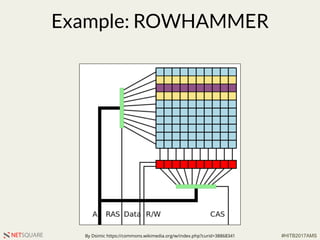
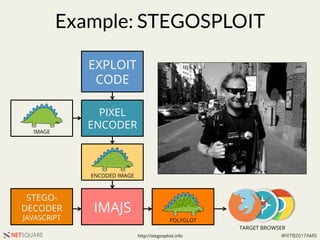
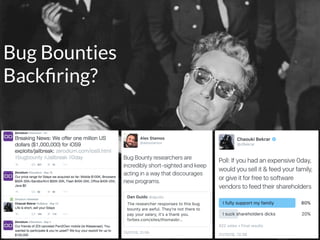
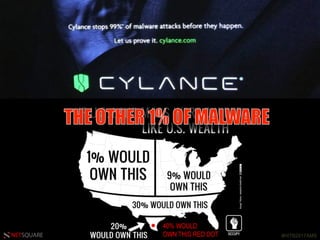
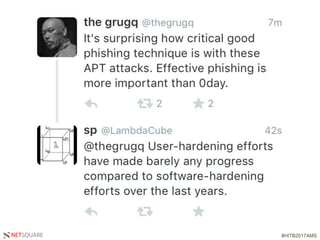
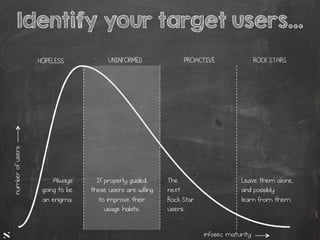
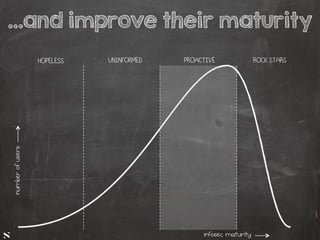
The document presents a talk by Saumil Shah at HITB 2017, discussing the evolution of cybersecurity attacks and defenses from 2001 to 2017. It emphasizes the need for proactive security measures and a shift from reactive strategies, highlighting the importance of metrics and creative defenses in modern information security. Shah outlines seven axioms of security aimed at improving the effectiveness of security defenses and addressing the challenges posed by evolving threats.