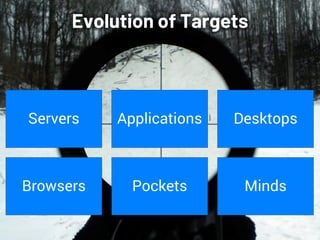
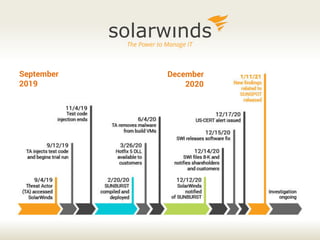
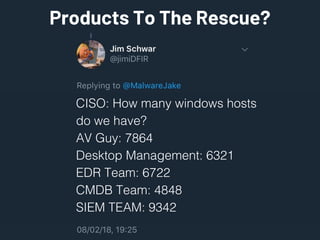
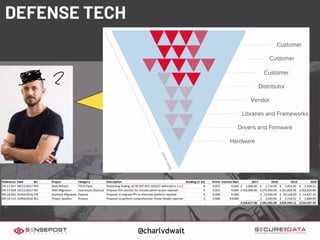
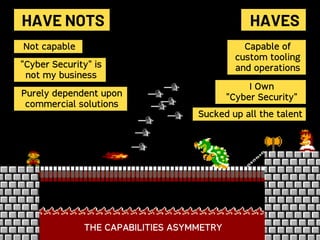
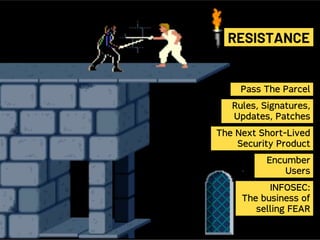
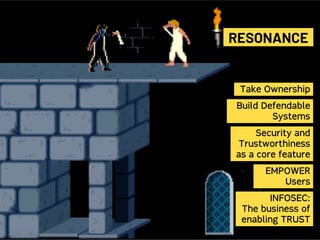
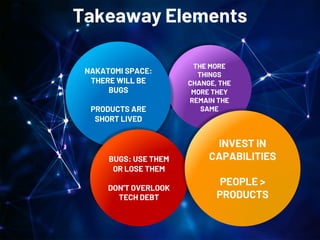
Saumil Shah's keynote at HITB2023AM focuses on the evolution of cybersecurity attacks and defenses over time, highlighting the increasing complexity and commercialization of exploits. He discusses the historical context, technological advancements, and socio-political challenges facing security defenses while underscoring the need for a proactive approach to building trustworthy computing systems. The talk emphasizes the importance of investing in capabilities and fosters a shift in the infosec narrative from selling fear to enabling trust.