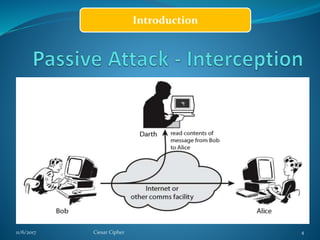
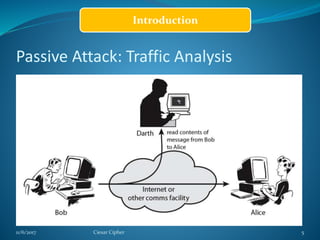
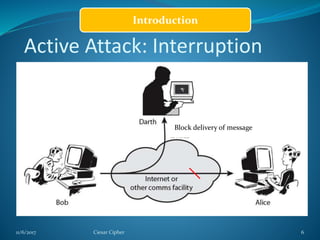
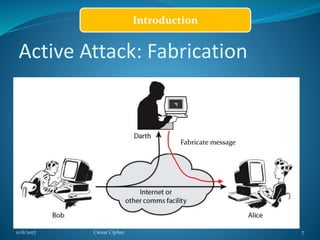
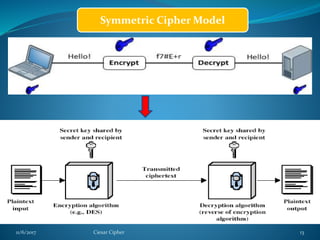
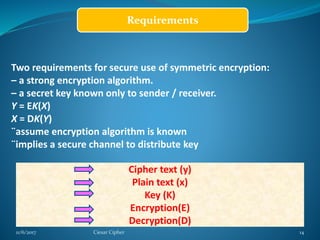
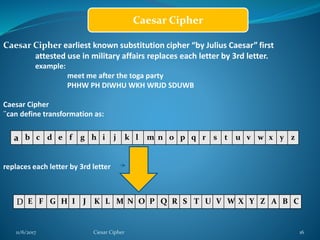
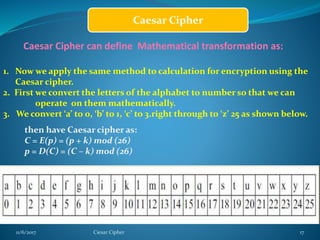
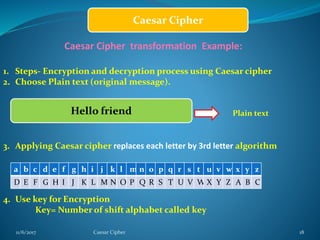
This document provides information about the Caesar cipher encryption technique. It begins with an introduction to cryptography and discusses why encryption is needed for secure communication. It then explains the Caesar cipher specifically, which is one of the earliest and simplest substitution ciphers. It works by shifting each letter in the plaintext message by a set number of places in the alphabet, using a key. An example is provided to demonstrate the encryption and decryption process using the Caesar cipher.