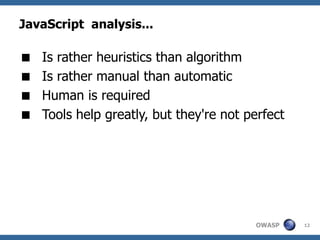
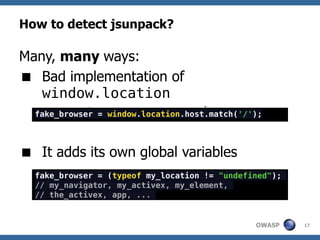
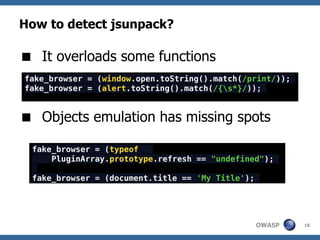
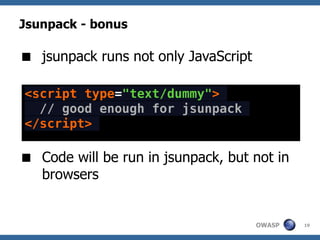
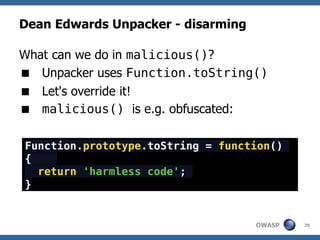
The document discusses techniques for creating, obfuscating, and analyzing JavaScript malware. It covers various obfuscation methods, the challenges of malware analysis, and introduces tools like JSUnpack for analyzing malicious code. The author emphasizes the importance of human analysis, creativity, and the limitations of automatic tools in detecting obfuscated malware.


![Obfuscation
There is no perfect obfuscation [cs.princeton.edu]
Analysis as debugging
Debugging is twice as hard as
writing a program in the first
place. So if you're as clever as
you can be when you write it,
how will you ever debug it?
Brian Kernighan, The Elements of Programming Style
OWASP 5](https://image.slidesharecdn.com/owasp-malicious-javascript-en-100908112334-phpapp02/85/Creating-obfuscating-and-analyzing-malware-JavaScript-5-320.jpg)
![Obfuscation methods
for while + if
Iteration recursion
Complex logical tests
Dummy code branches
Quasitautologies [blog.didierstevens.com]
Enigmatic variable names
OWASP 6](https://image.slidesharecdn.com/owasp-malicious-javascript-en-100908112334-phpapp02/85/Creating-obfuscating-and-analyzing-malware-JavaScript-6-320.jpg)
![Obfuscation methods in JS
JavaScript is a dynamic and functional language
Code created at runtime – eval
String.fromCharCode, unescape
Regular expressions - String.replace
Packers, e.g.
[dean.edwards.name]
[developer.yahoo.com]
[malwareguru.org]
[closure-compiler.appspot.com]
Others - e.g. WhiteSpace Obfuscation [ktcorpsecurity.com]
OWASP 7](https://image.slidesharecdn.com/owasp-malicious-javascript-en-100908112334-phpapp02/85/Creating-obfuscating-and-analyzing-malware-JavaScript-7-320.jpg)
![Active defense against analysis
Function.toString /
arguments.callee.toString [isc.sans.org]
autoencryption [isc.sans.org]
browser detection
DOM
window, navigator
timings
cookies
mouse position, screen resolution
Malware served only once per IP [research.zscaler.com]
OWASP 8](https://image.slidesharecdn.com/owasp-malicious-javascript-en-100908112334-phpapp02/85/Creating-obfuscating-and-analyzing-malware-JavaScript-8-320.jpg)
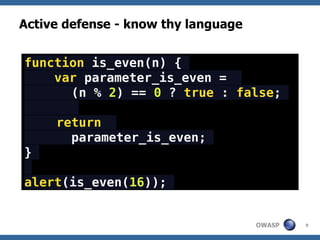


![jsunpack
Runs JS inside SpiderMonkey [mozilla.org]
JS fetched from URL, PCAP, JS/HTML file…
SM is modified to include:
DOM emulation
browser objects emulation
onload() event
monitors eval(), setTimeout() and
others
scans the code using signatures file
OWASP 14](https://image.slidesharecdn.com/owasp-malicious-javascript-en-100908112334-phpapp02/85/Creating-obfuscating-and-analyzing-malware-JavaScript-14-320.jpg)

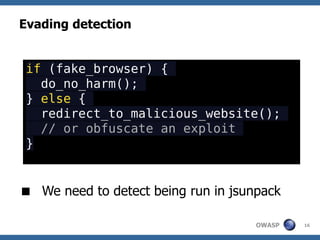


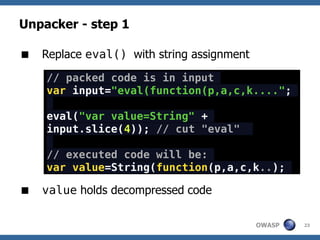
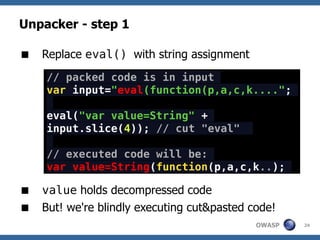
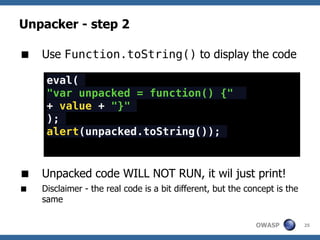
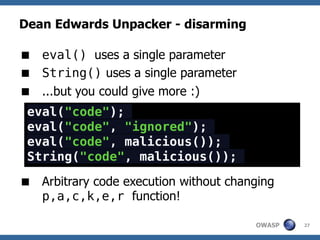
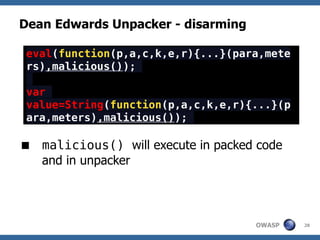
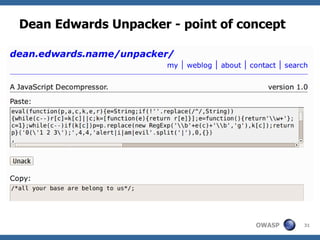
![Dean Edwards' Unpacker
A JavaScript Decompressor [dean.edwards.name]
Reverses Dean Edward's packer
Packer works like this:
eval(function(p,a,c,k,e,r){/*code*/}(para,
meters))
/* which is the same as */
var packer = function(p,a,c,k,e,r) {/**/};
var s = packer(para,meters);
eval(s);
OWASP 22](https://image.slidesharecdn.com/owasp-malicious-javascript-en-100908112334-phpapp02/85/Creating-obfuscating-and-analyzing-malware-JavaScript-22-320.jpg)


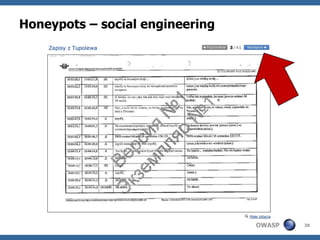
![High interaction client honeypots
Capture-HPC [projects.honeynet.org] as an example
Code is run in real browser in a virtual machine
Server serves URL list to visit
Client starts browsers and waits…
Code side-effects are monitored
Filesystem
Registry
Processes
If anything suspicious happens with the system, URL
is reported to server as a malware
OWASP 32](https://image.slidesharecdn.com/owasp-malicious-javascript-en-100908112334-phpapp02/85/Creating-obfuscating-and-analyzing-malware-JavaScript-32-320.jpg)