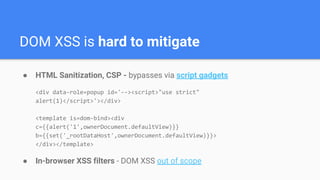
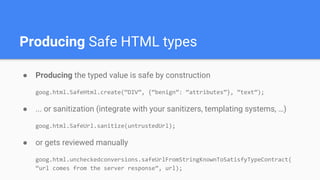
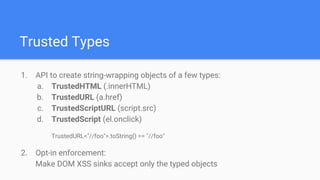
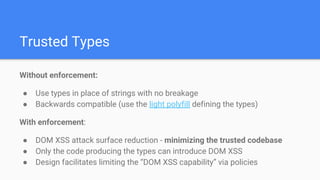
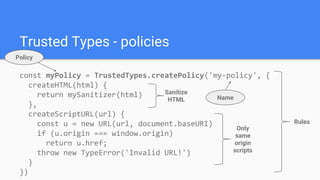
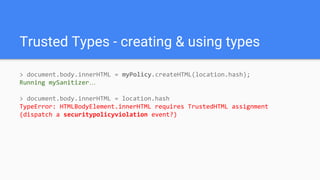
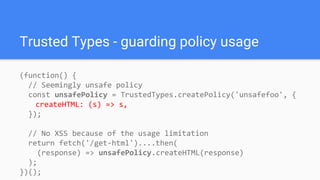
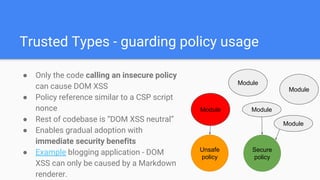
Trusted Types aims to prevent DOM-based cross-site scripting (DOM XSS) by introducing a new API for creating string-wrapping objects that can only be used in safe ways. It allows defining policies that create these trusted types, limiting where DOM XSS can be introduced. With enforcement, web platforms would only accept trusted types for DOM sinks like innerHTML, reducing the attack surface. Policies can be guarded and their creation controlled via response headers to further limit security risks. Initial implementations show it can help secure applications with minimal changes.



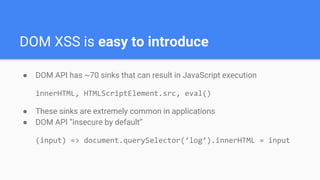
![● Sources far away from sinks, complex data flows (e.g. server roundtrip)
● Static checks don’t work reliably:
foo.innerHTML = bar // what is bar?
foo[(_ => "innerHTML")()] = bar
foo[k] = v
● Manual review is infeasible
● Dynamic (taint-tracking, fuzzing) has a small code coverage
DOM XSS is hard to detect](https://image.slidesharecdn.com/trustedtypesw3ctpac-190423082527/85/Trusted-Types-W3C-TPAC-2018-5-320.jpg)