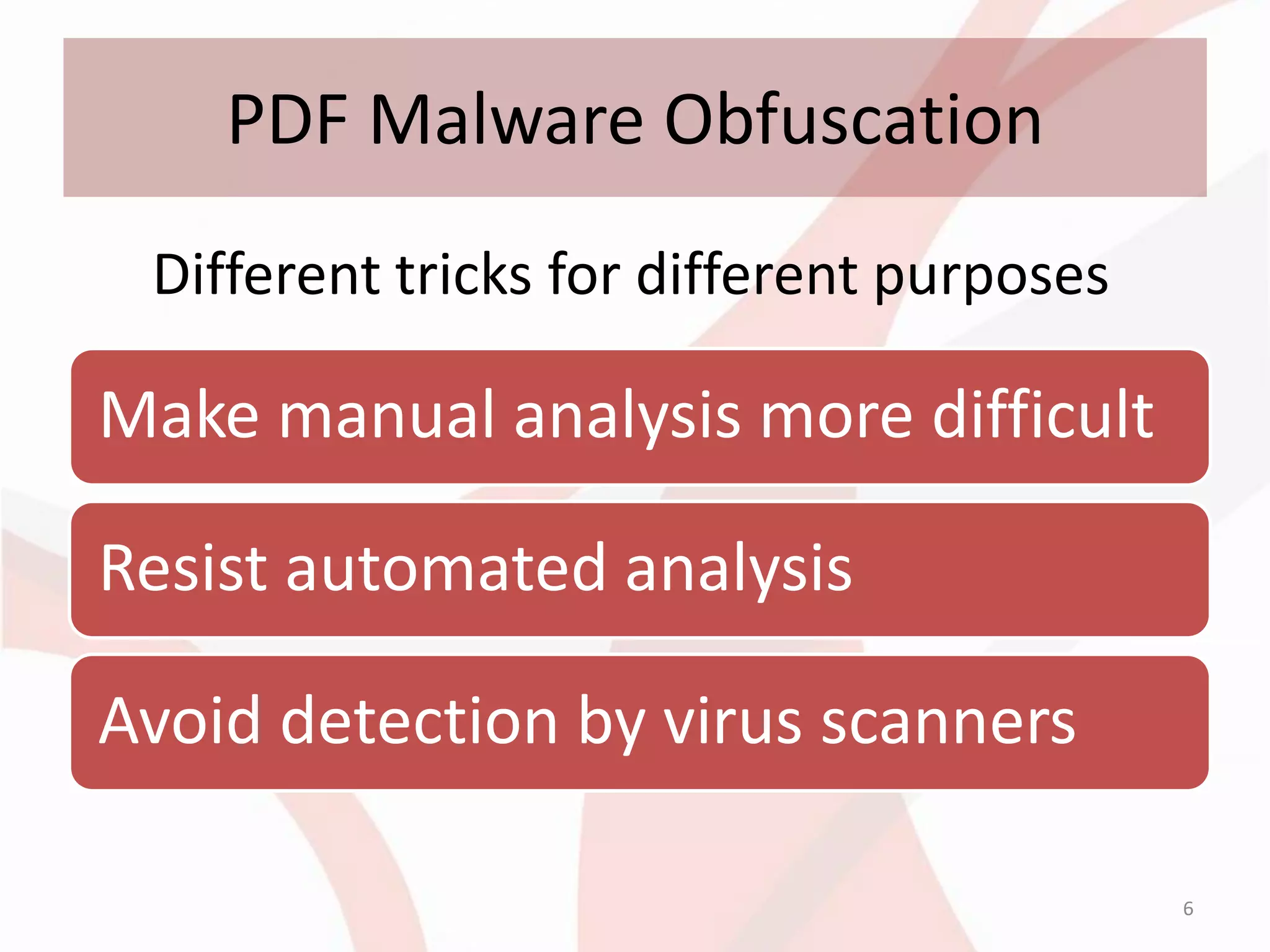
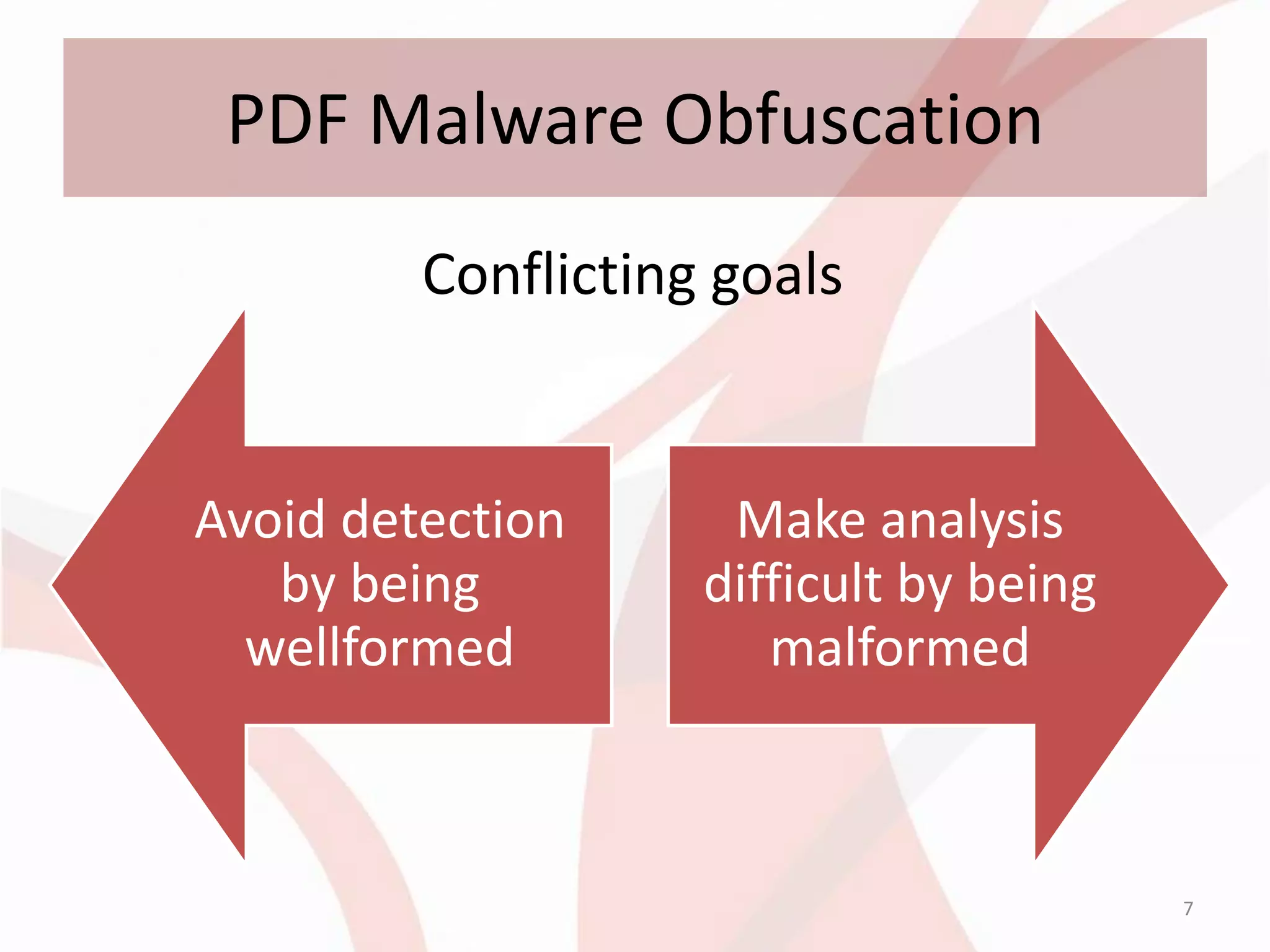
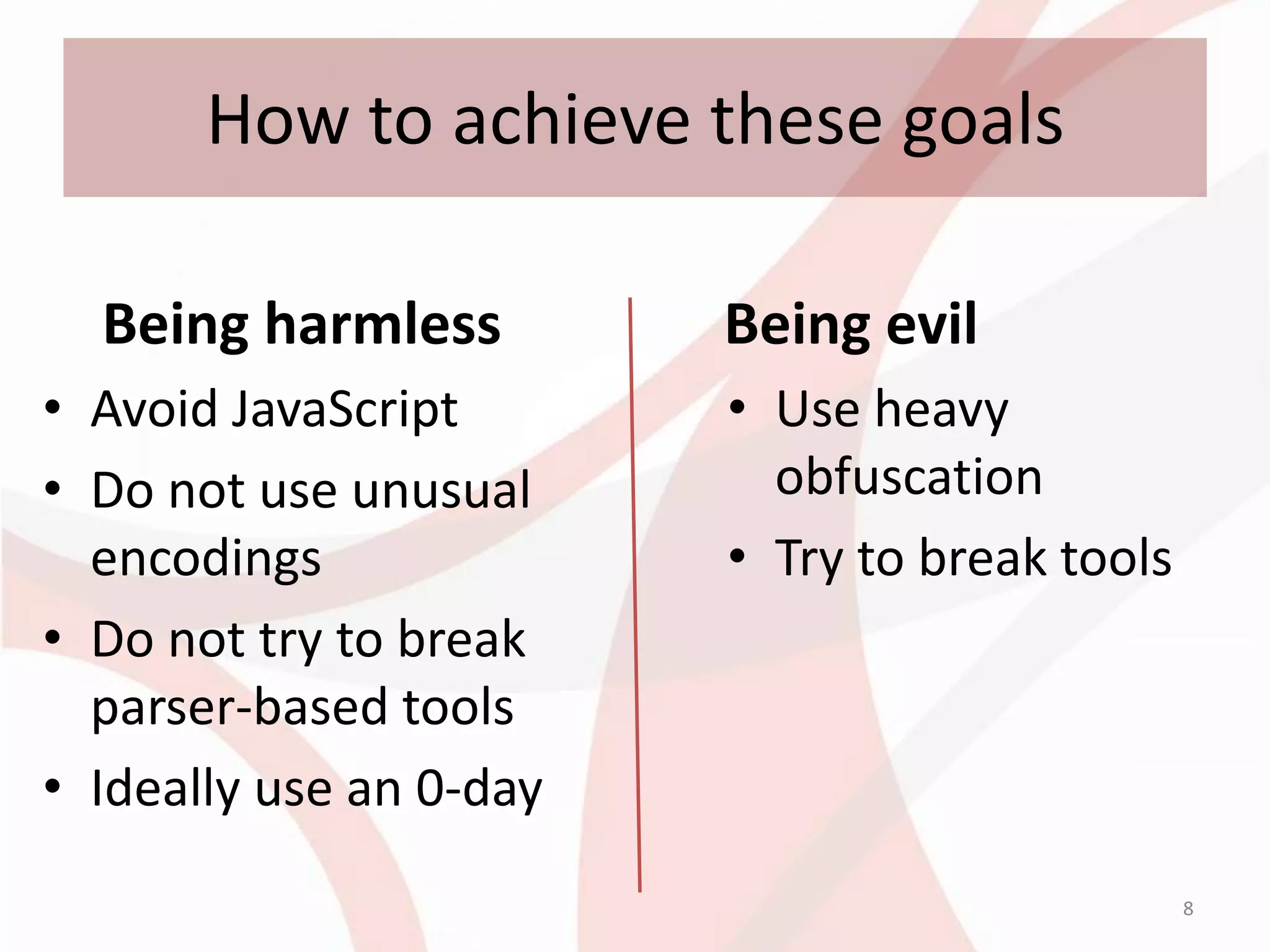
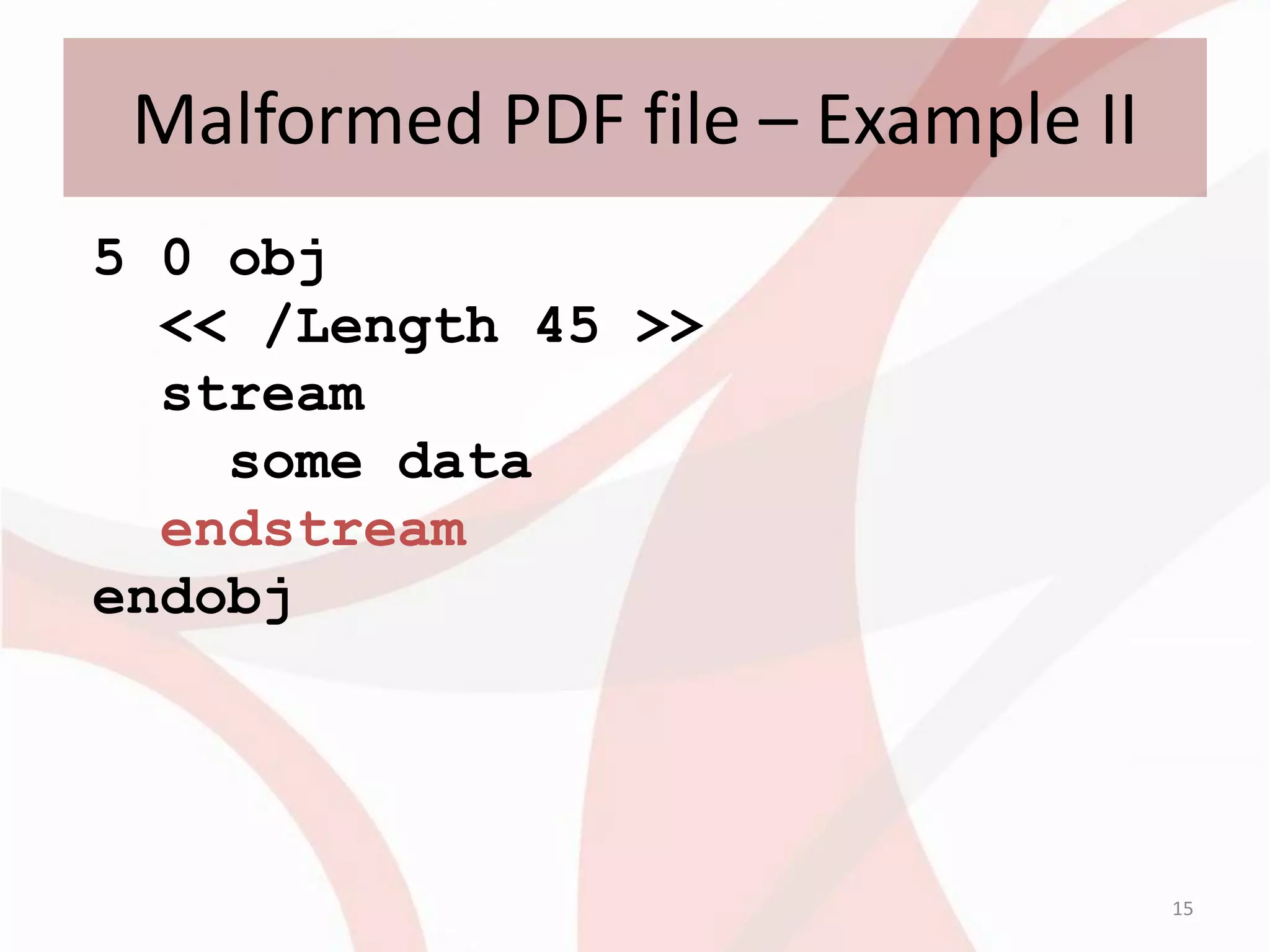
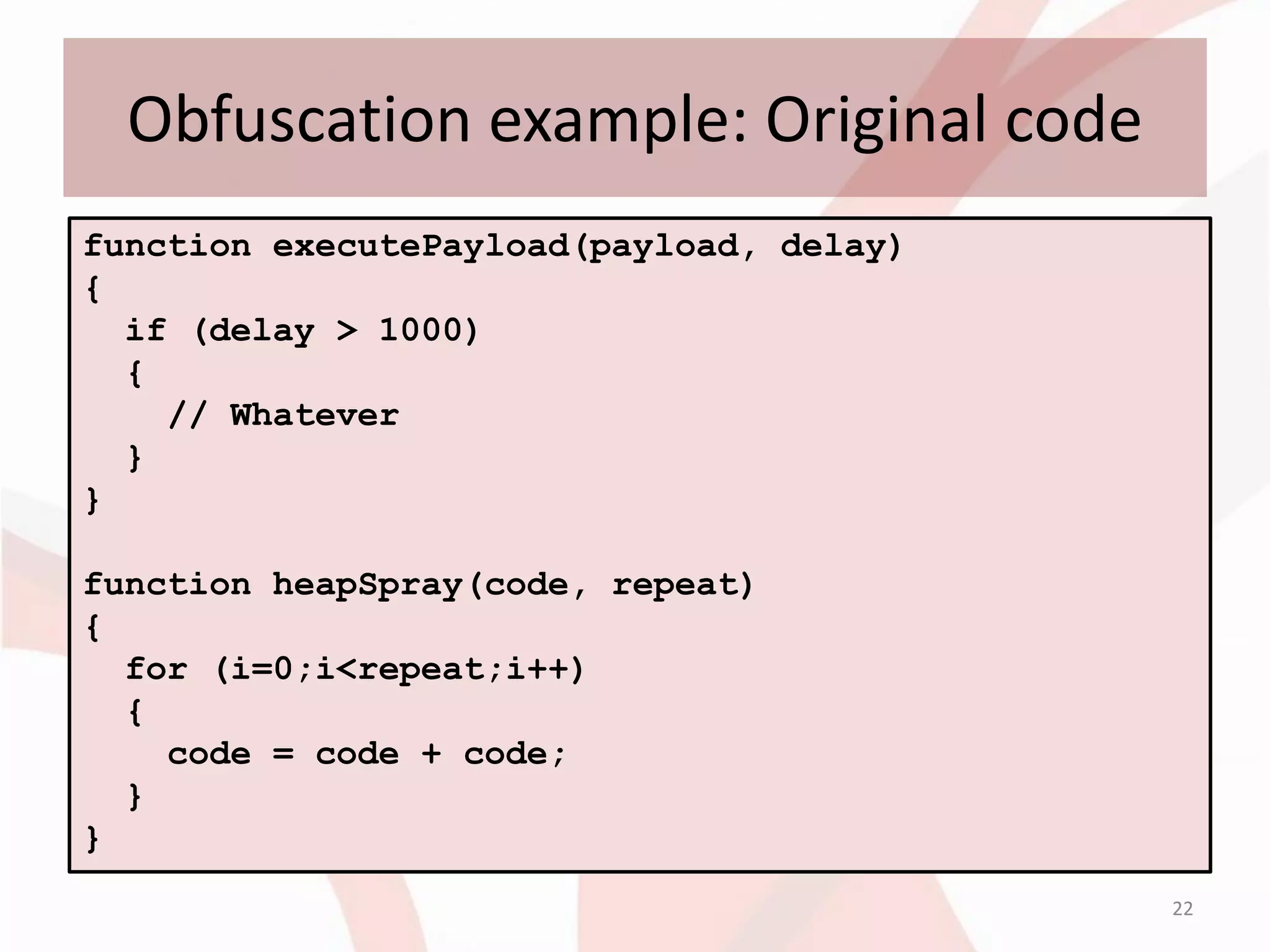
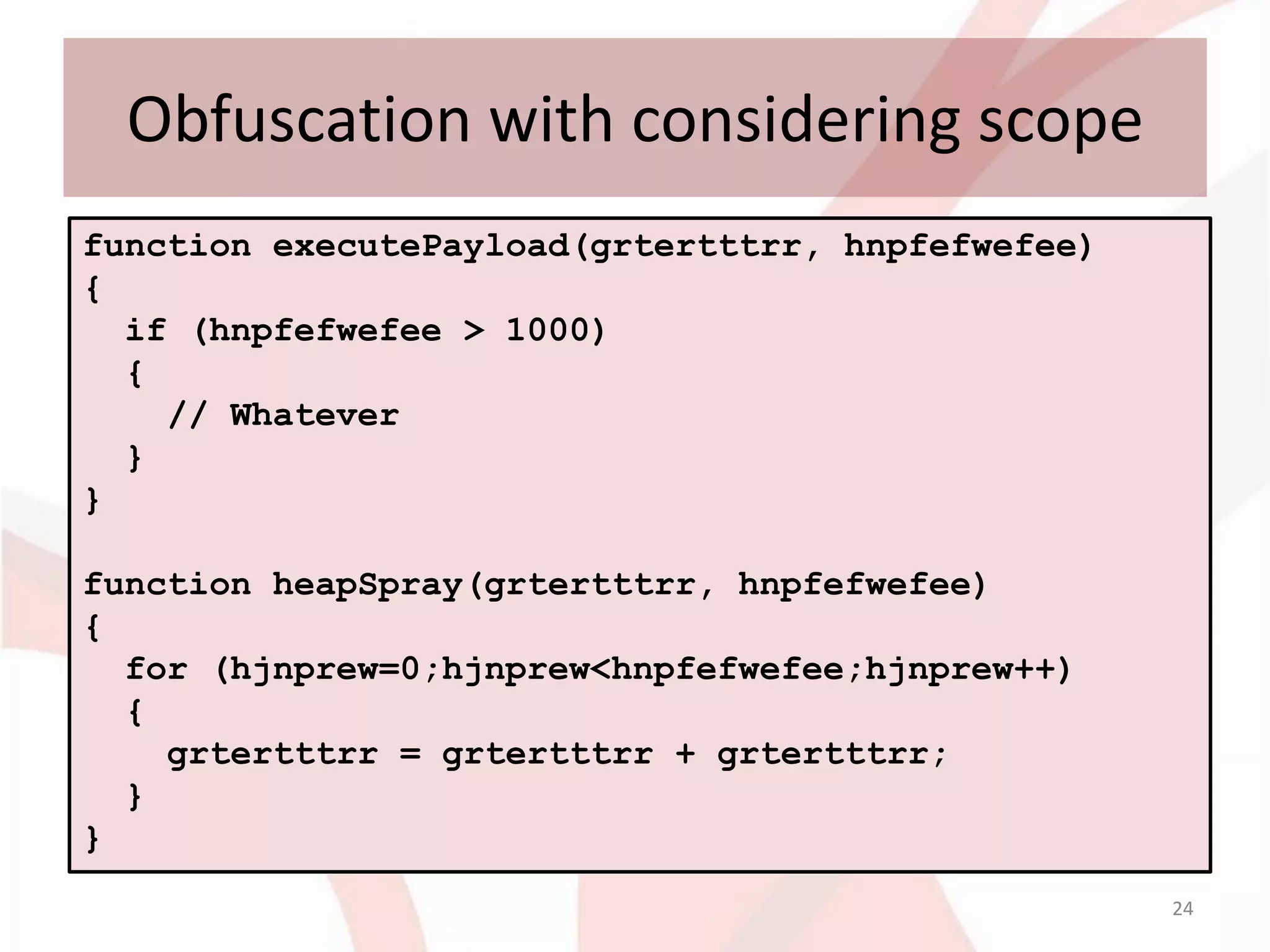
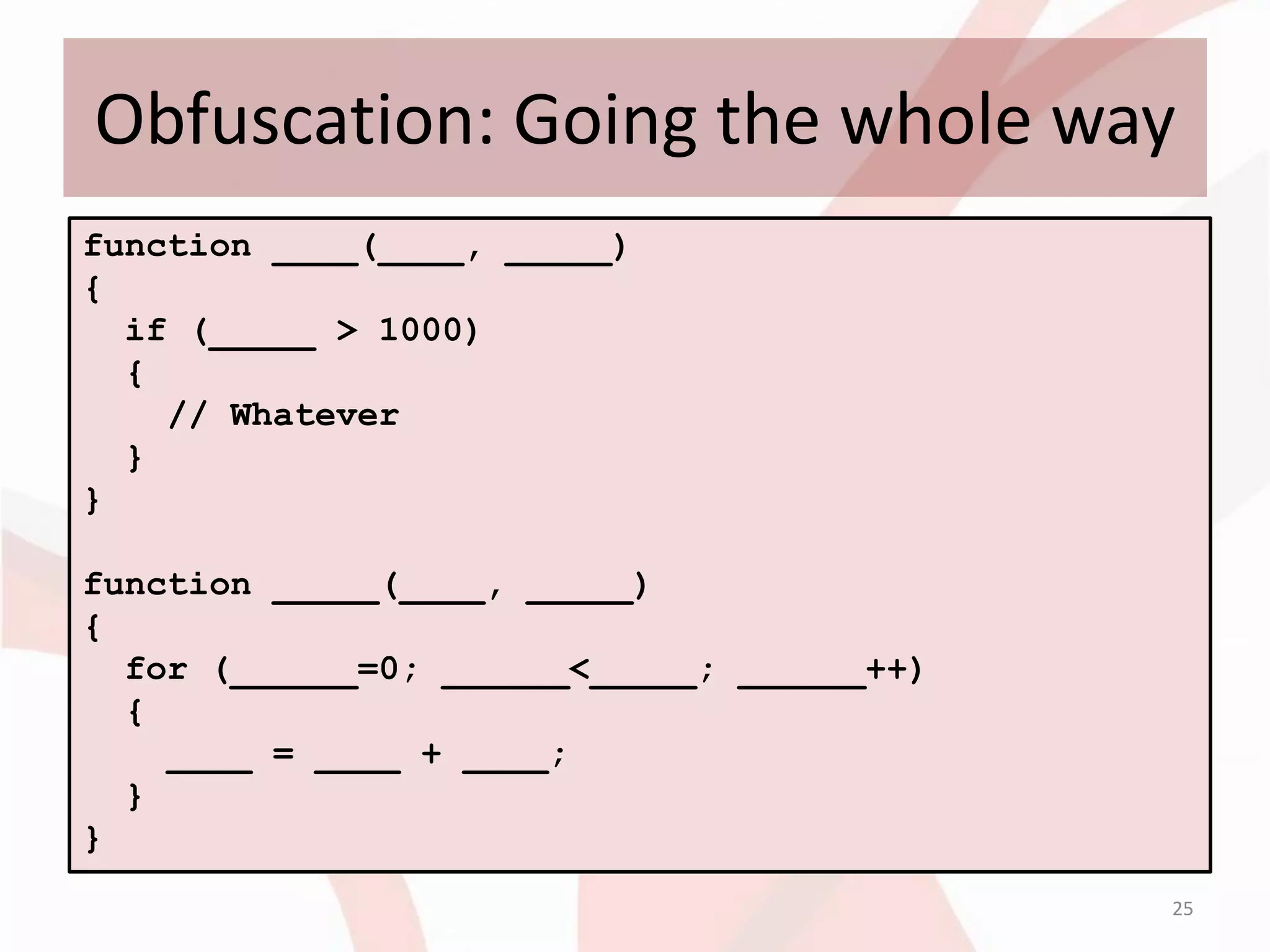
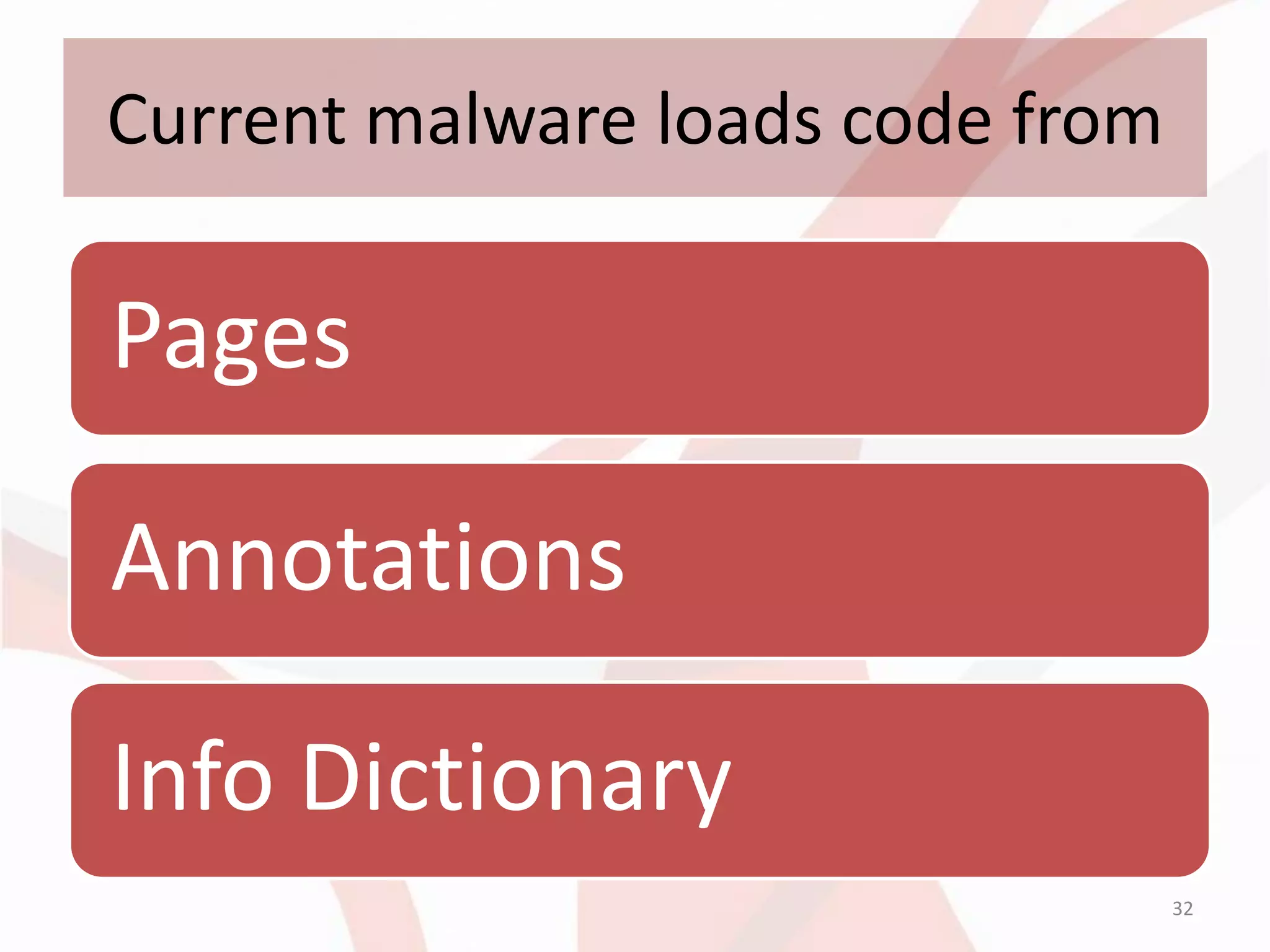
This document discusses techniques for obfuscating PDF malware to make analysis more difficult. It describes using malformed PDF structures, splitting JavaScript code across multiple objects, and using anti-emulation techniques that exploit idiosyncrasies in Adobe Reader's JavaScript engine. The goal is to avoid detection by antivirus software while confusing manual and automated analysis tools. It also covers obfuscating JavaScript code through techniques like name obfuscation and eval chains.






















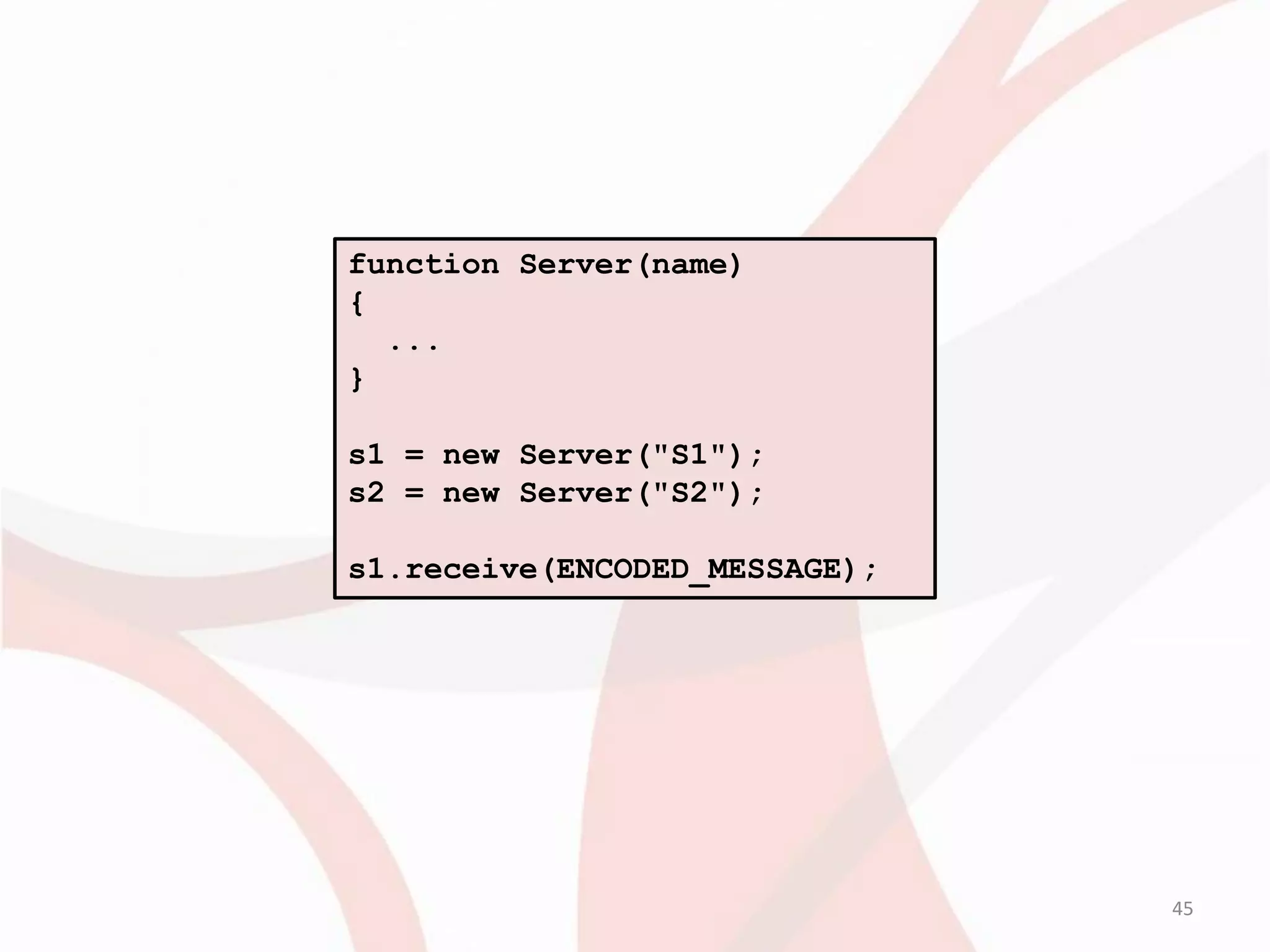
;
var s = p[0].subject;
eval(s);
33](https://image.slidesharecdn.com/howtoreallyobfuscateyourpdfmalware-100713095253-phpapp01/75/How-to-really-obfuscate-your-pdf-malware-33-2048.jpg)
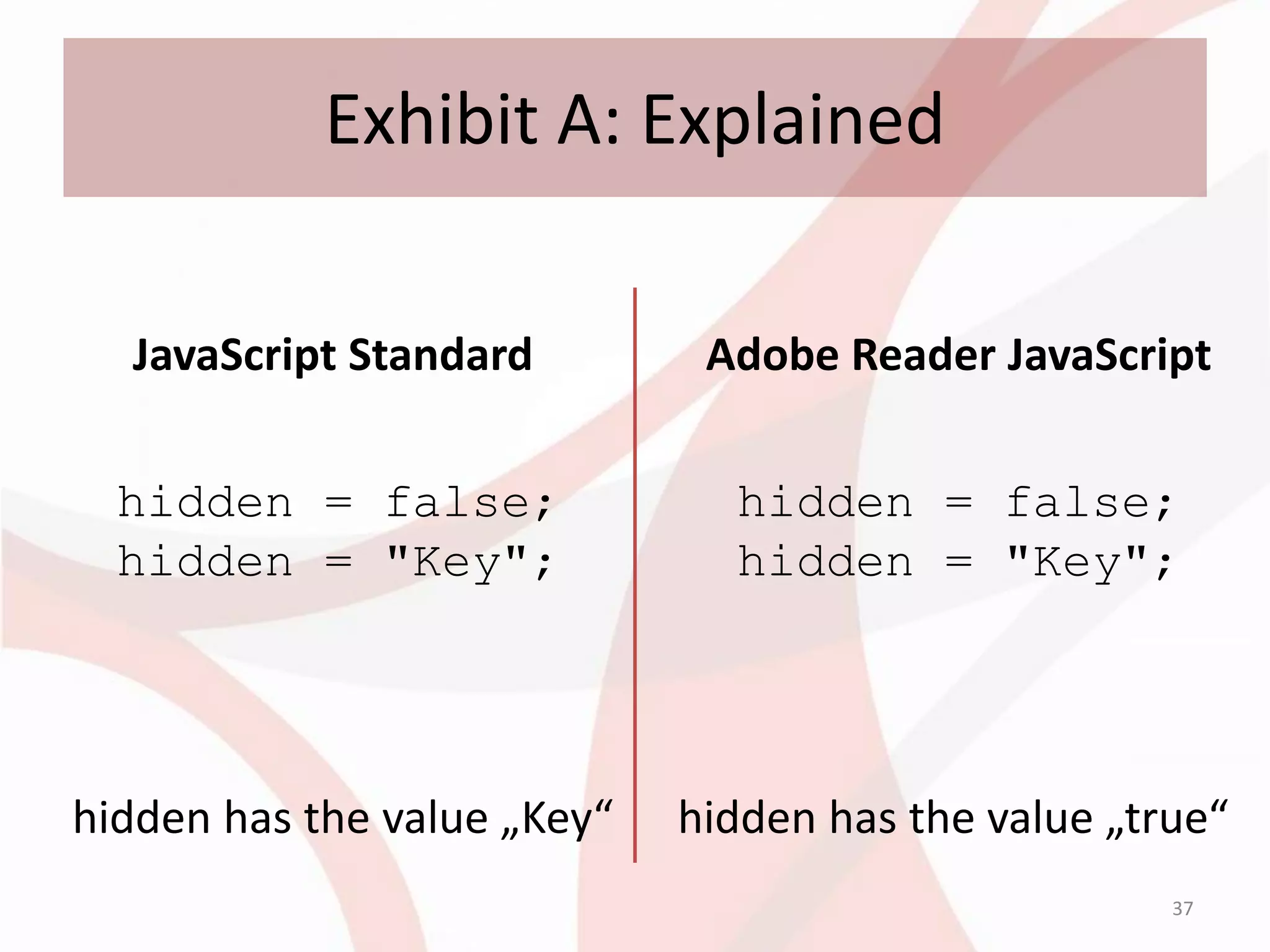
![Exhibit A: Idiosyncrasy
cypher = [7, 17, 28, 93, 4, 10, 4, 30, 7, 77, 83, 72];
cypherLength = cypher.length;
hidden = "ThisIsNotTheKeyYouAreLookingFor";
hiddenLength = hidden.toString().length;
for(i=0,j=0;i<cypherLength;i++,j++)
{
cypherChar = cypher[i];
keyChar = hidden.toString().charCodeAt(j);
cypher[i] = String.fromCharCode(cypherChar ^ keyChar);
if (j == hiddenLength - 1)
j = -1;
}
eval(cypher.join(""));
36](https://image.slidesharecdn.com/howtoreallyobfuscateyourpdfmalware-100713095253-phpapp01/75/How-to-really-obfuscate-your-pdf-malware-36-2048.jpg)


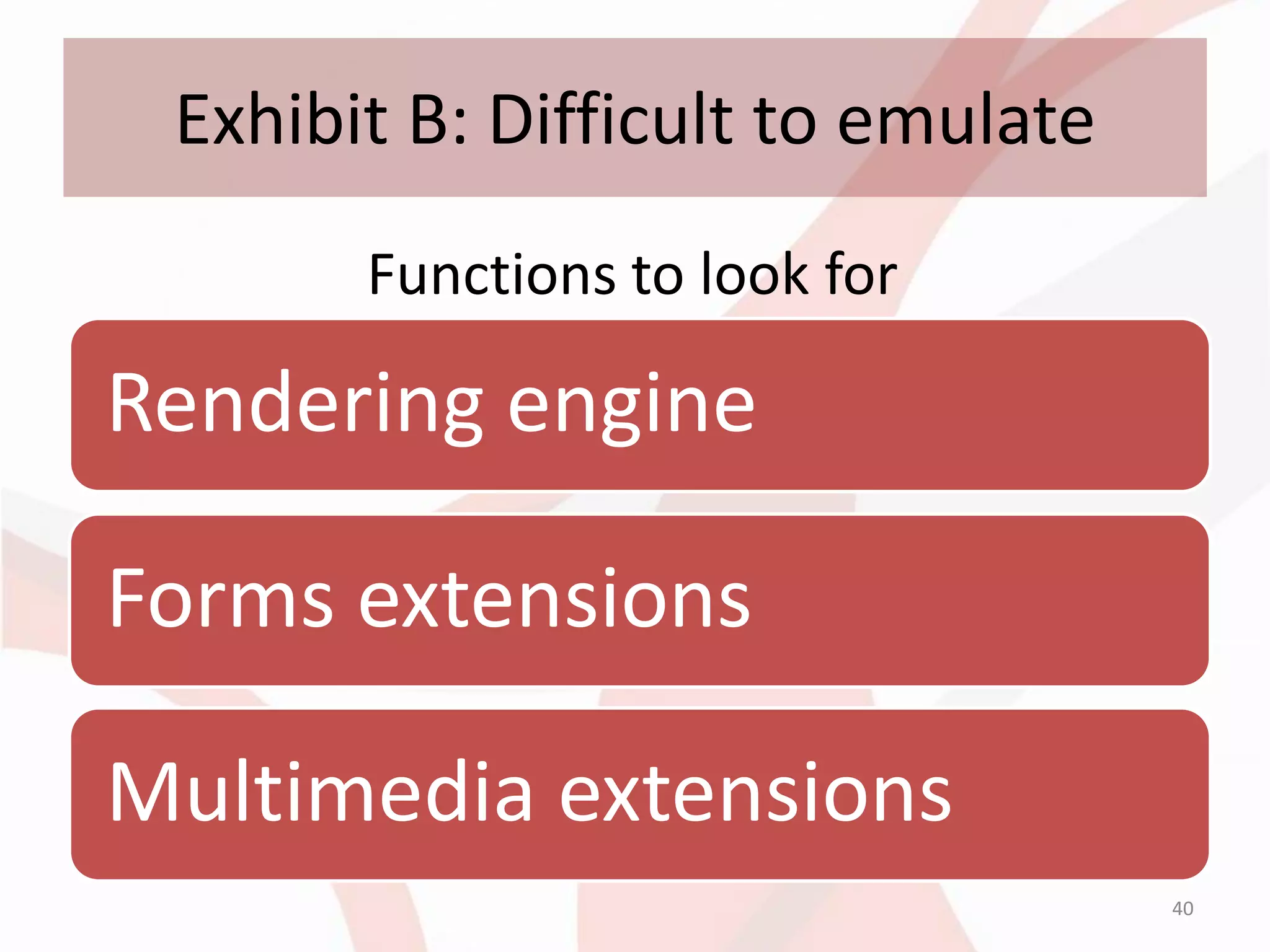
![Exhibit B: Difficult to emulate
crypt = "T^_]^[T IEYYD__ FuRRKBD ";
plain = Array();
key = getPageNthWordQuads(0, 0).toString().split(",")[1];
for (i=0,j=0;i<crypt.length;i++,j++)
{
plain = plain + String.fromCharCode((crypt.charCodeAt(i) ^
key.charCodeAt(j)));
if (j >= key.length)
j = 0;
}
app.alert(plain);
)
41](https://image.slidesharecdn.com/howtoreallyobfuscateyourpdfmalware-100713095253-phpapp01/75/How-to-really-obfuscate-your-pdf-malware-41-2048.jpg)