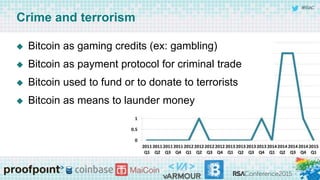
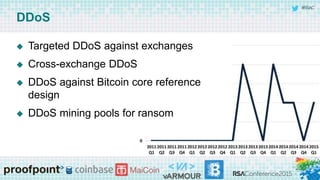
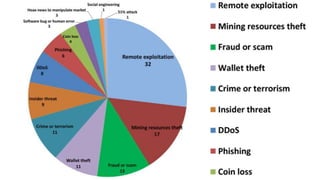
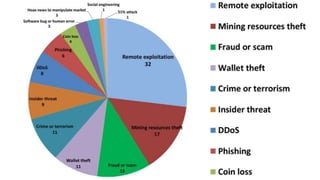
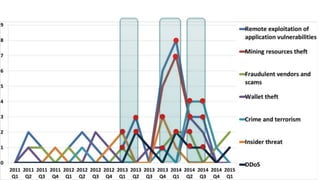
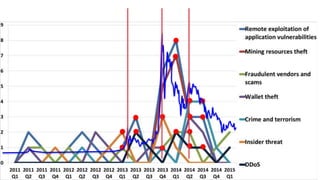
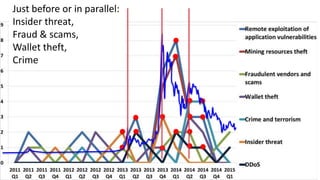
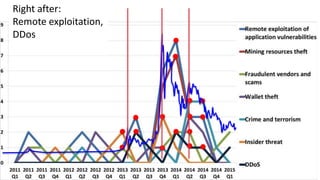
The panel discussion focuses on various threats to Bitcoin, emphasizing its attractiveness as a target for criminals due to insider threats, fraud, wallet theft, and remote exploitation. Participants explore potential future challenges, including scams and theft of mining resources, as well as the implications of Bitcoin on the security industry. Key topics include the risks of malware, the importance of defense strategies, and the overall adoption of Bitcoin in a changing landscape.













![#RSAC
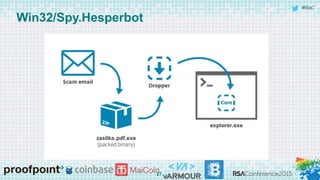
Bitcoin malware trends
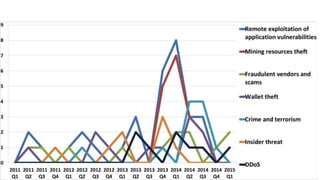
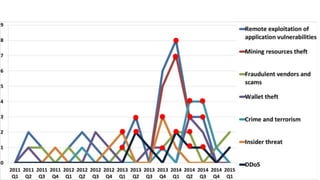
Malware is and will be an important tool for coin thieves against
end users
Attack wallet files or website logins
Desktop and mobile
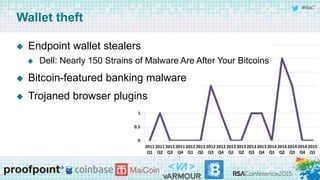
Interest from malware authors is proportional to the Bitcoin price
and adoption in their target demographic
Dropped in 2014 along with price [Symantec]
As adoption grows, average technical savvy of user will drop](https://image.slidesharecdn.com/rsac2015htaf03bitcoinv4-150424122501-conversion-gate01/85/RSA-2015-Bitcoin-s-Future-Threats-Expert-s-Roundtable-based-on-150-Case-Studies-26-320.jpg)