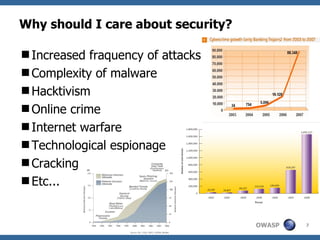
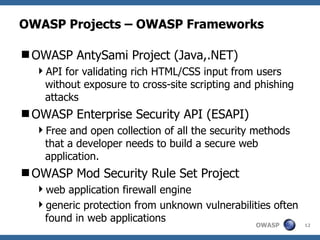
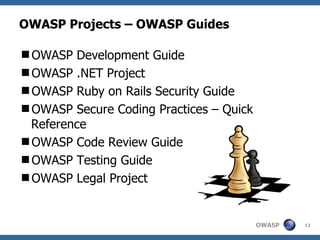
The document provides an overview of OWASP Serbia, which is a local chapter of OWASP (Open Web Application Security Project). It summarizes what OWASP is, its mission to improve application security, core values of being open, innovative, global and with integrity. It also describes some of OWASP's projects like the Top 10 vulnerabilities, Application Security Verification Standard, and tools like ZAP and WebGoat. Finally it discusses the local chapter in Serbia, its activities and goals.