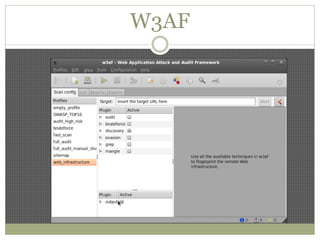
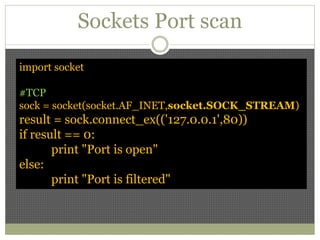
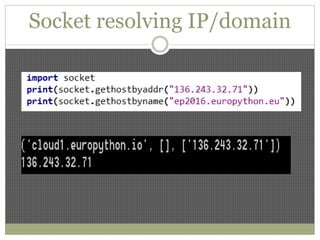
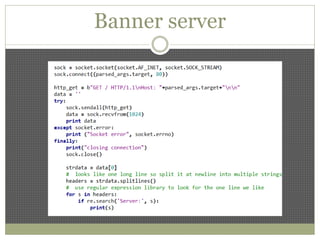
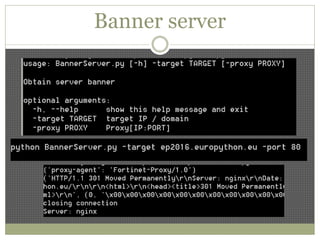
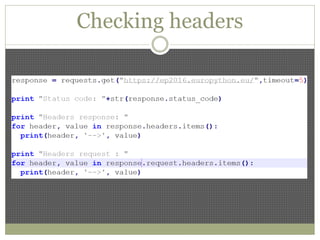
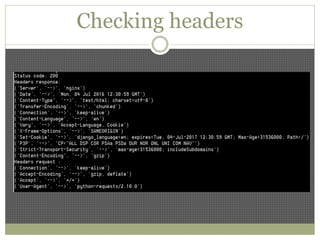
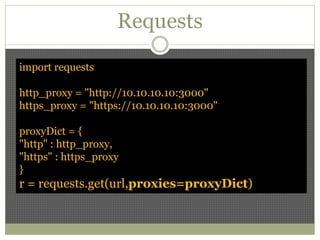
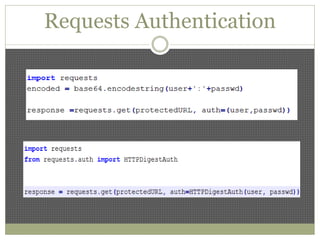
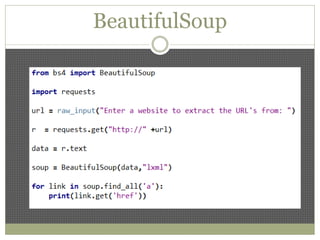
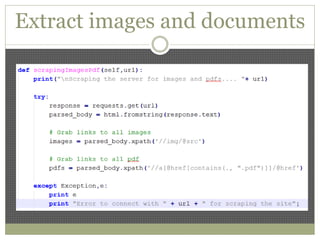
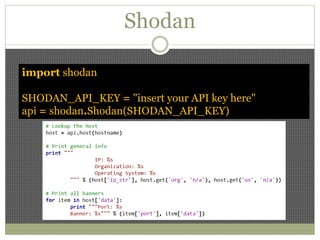
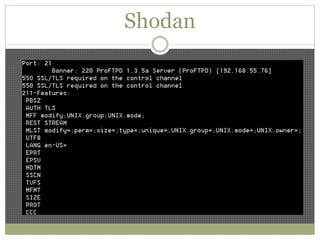
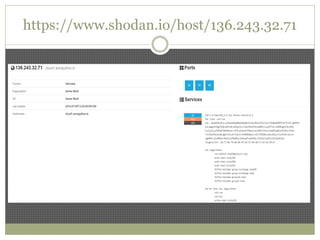
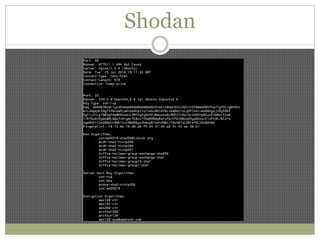
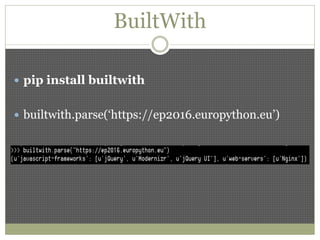
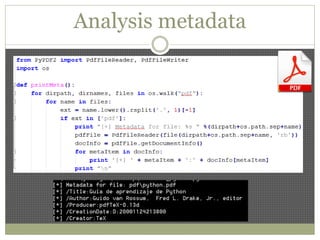
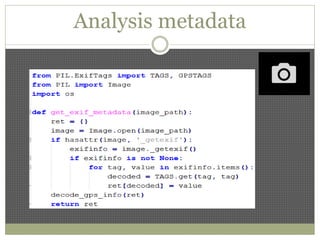
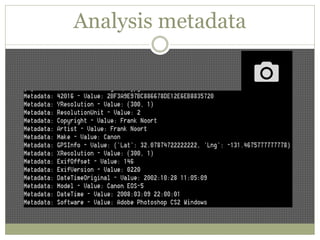
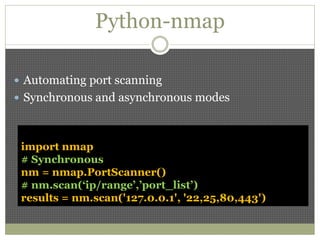
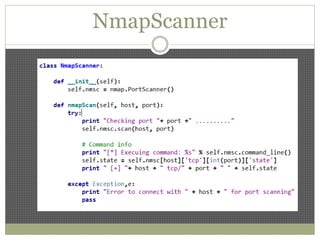
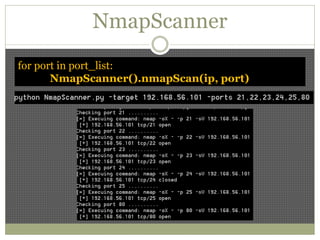
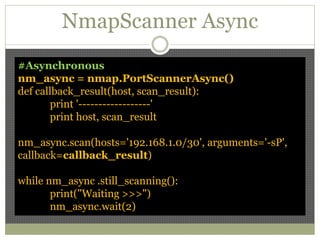
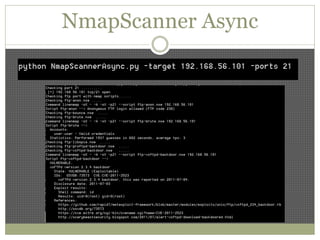
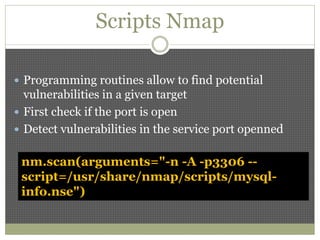
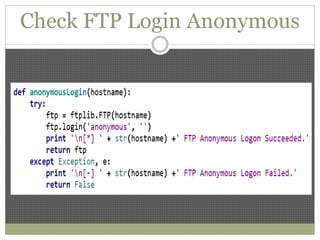
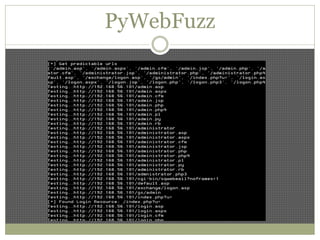
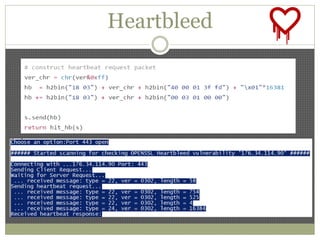
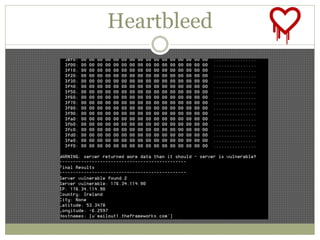
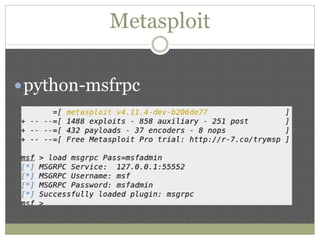
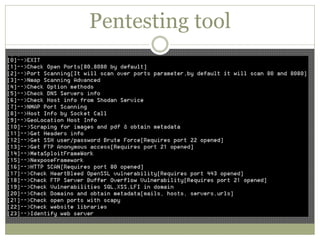
The document discusses using Python tools for ethical hacking and penetration testing. It provides an overview of several Python modules like Sockets, Requests, BeautifulSoup, and Shodan that can be used for tasks like port scanning, banner grabbing, web scraping, and online reconnaissance. It also describes popular Python tools for vulnerability scanning and penetration testing like Nmap, Metasploit, Nexpose, and provides code examples of using them for tasks like port scanning, vulnerability detection, and web application testing.