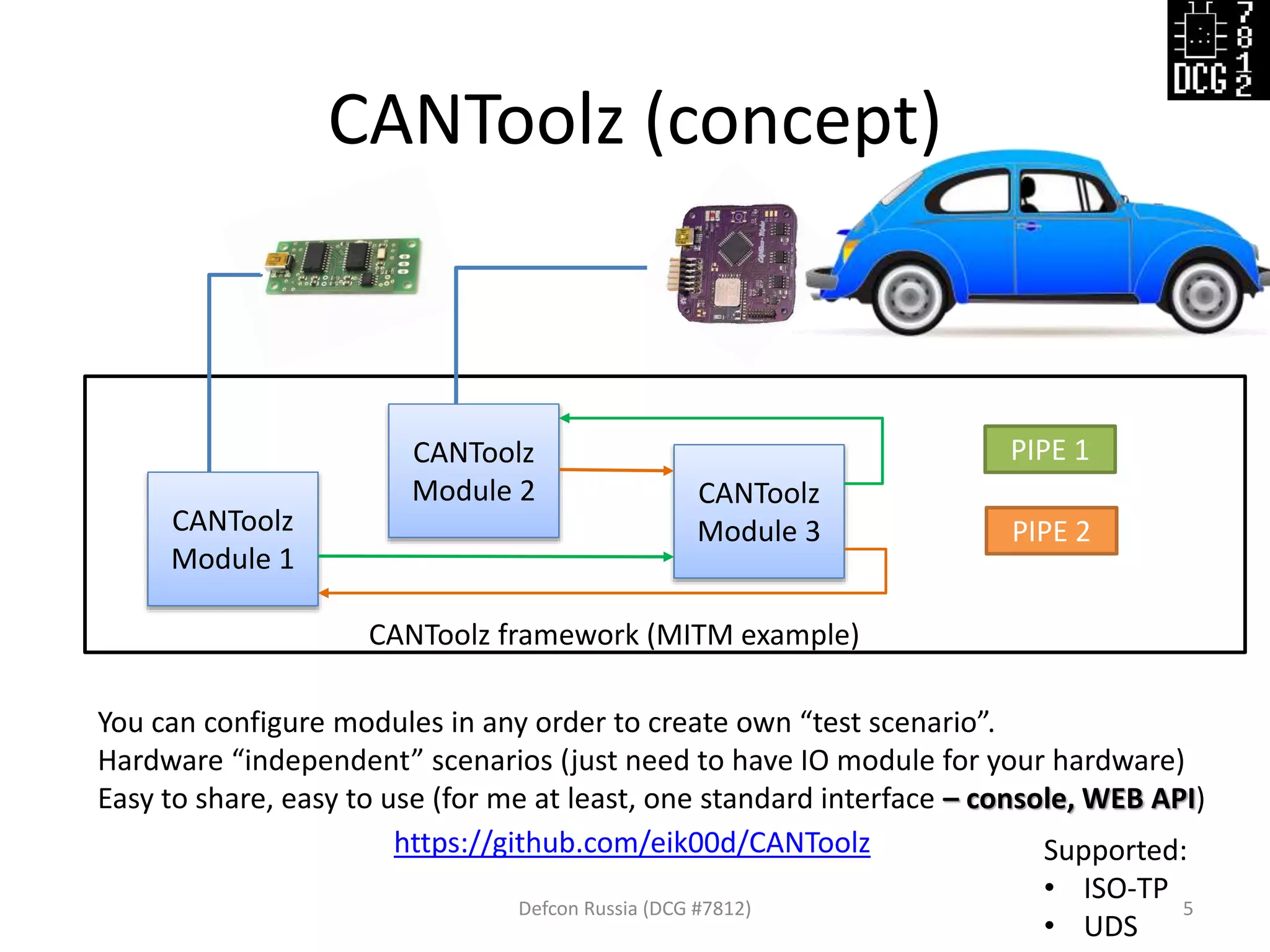
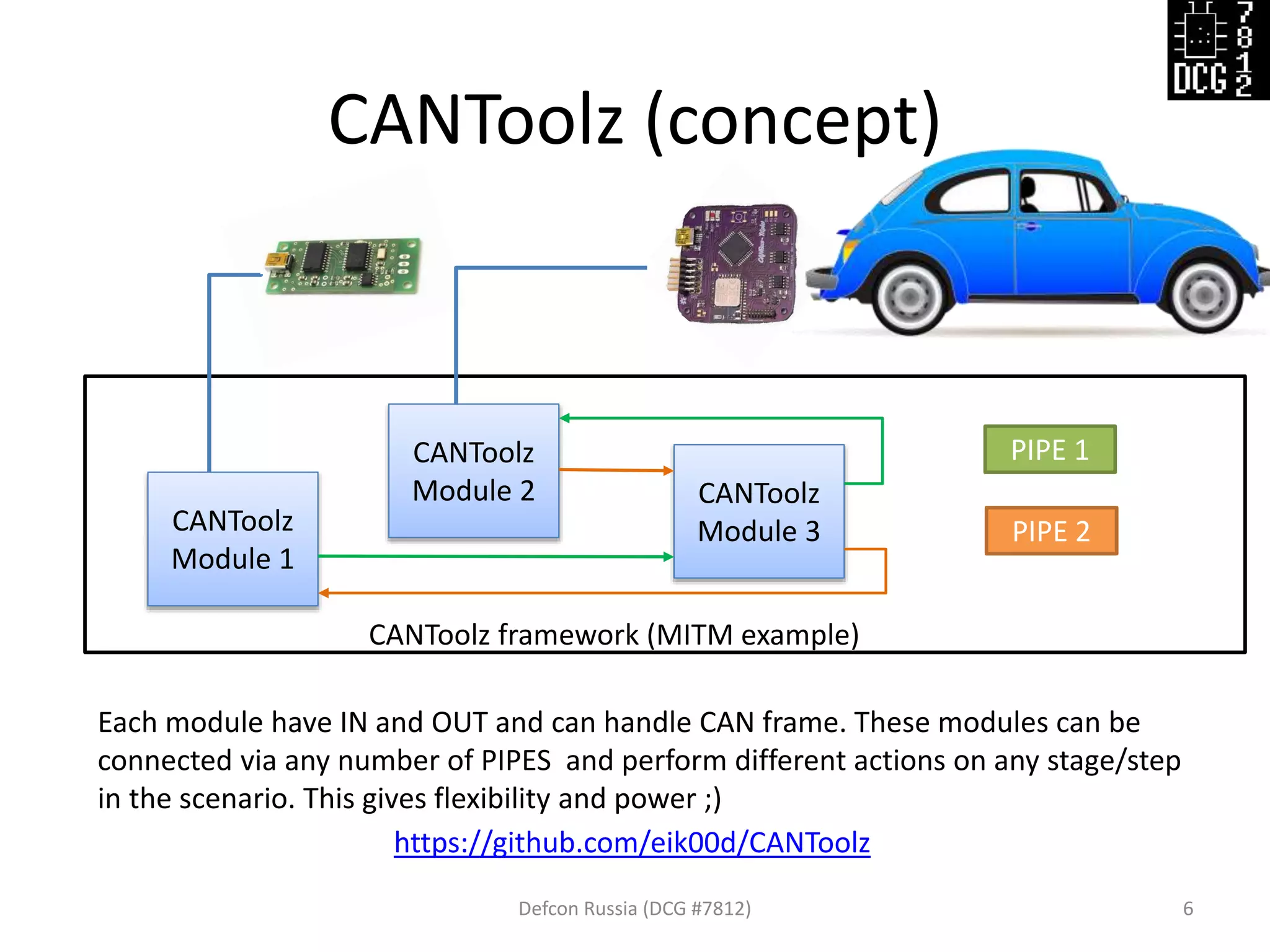
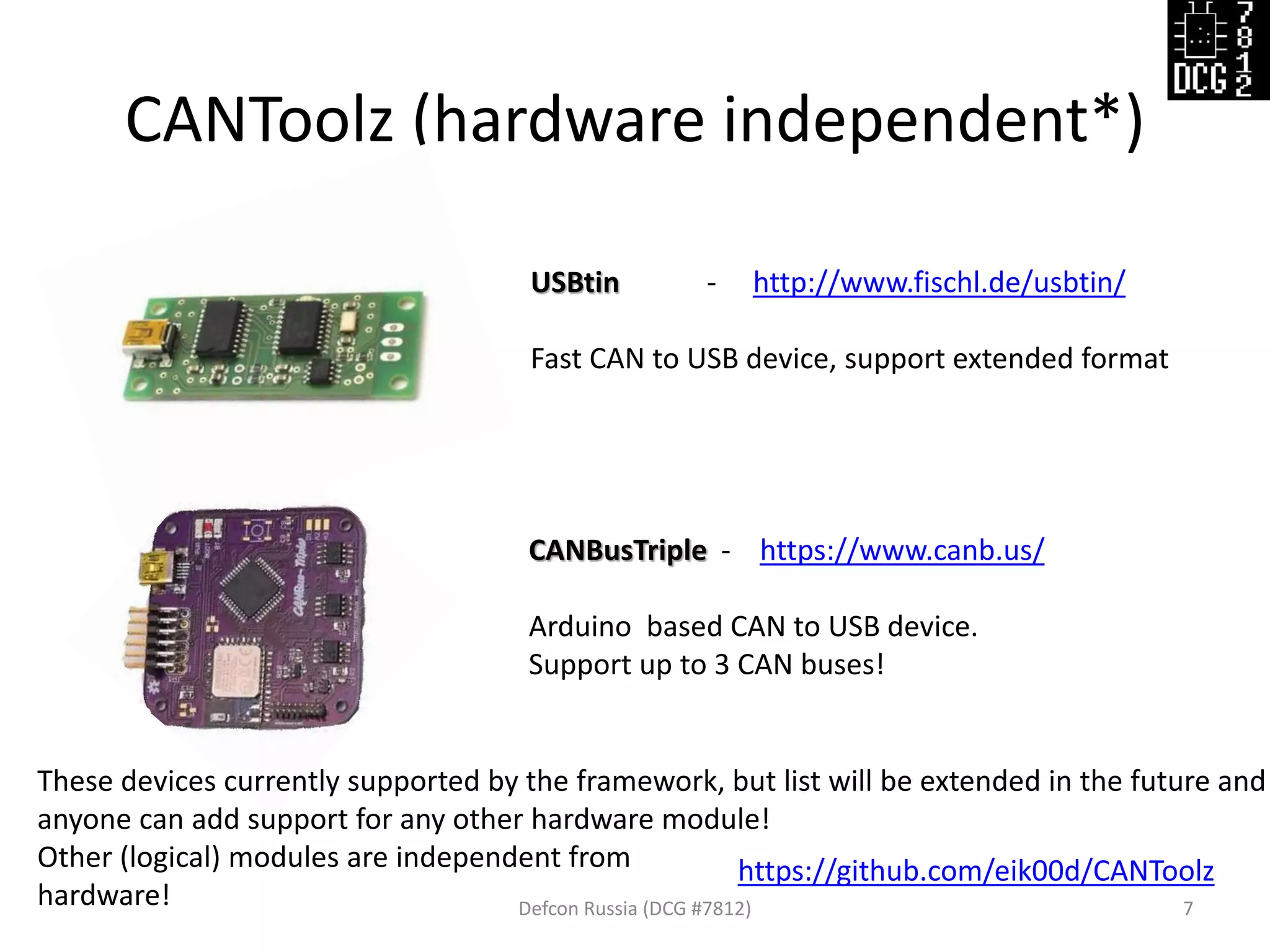
This document discusses using the CANToolz framework and modules to test and analyze CAN networks. CANToolz allows connecting hardware interfaces and logical modules in different configurations ("pipes") to create customizable testing scenarios. Examples provided include using CANToolz for firewall/MITM testing, CAN gateway scanning to identify passed frames, and replaying captured traffic to isolate frames that trigger actions. UDS protocol testing is also discussed, including detection of UDS traffic and scanning target ECUs.


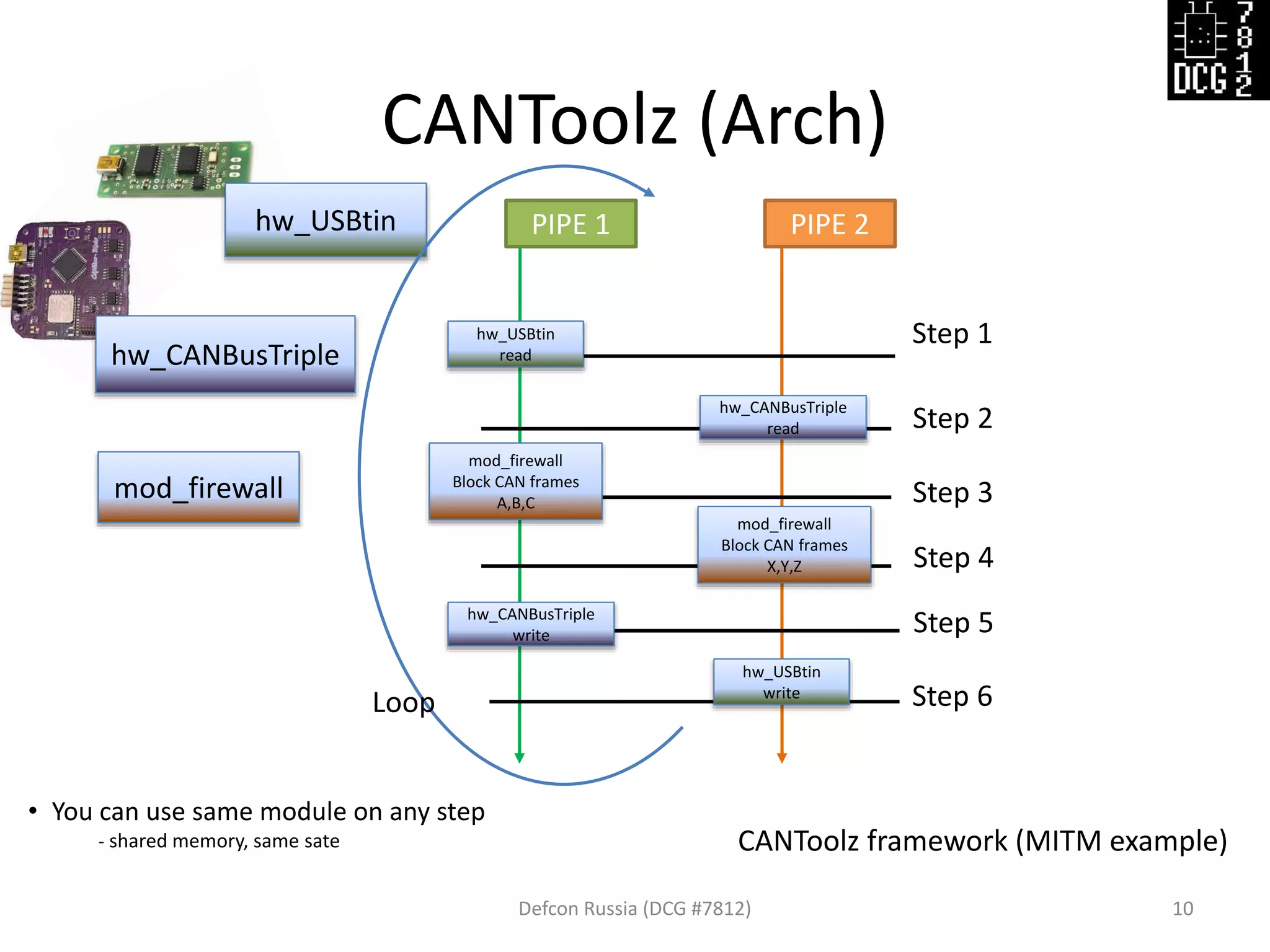
![Config file example:
Defcon Russia (DCG #7812) 11
# Load modules
load_modules = {
'hw_USBtin' :
‘hw_CANBusTriple' : {'port':'auto', 'debug':1, 'speed':500},
'mod_firewall' : {},
}
# Scenario with steps
actions = [
{'hw_USBtin' : {'pipe': 1, 'action': 'read'}},
{'hw_CANBusTriple': {'pipe': 2, 'action': 'read'}},
{'mod_firewall' : {'pipe': 1, 'black_list': [1337, 31337]}},
{'mod_firewall' : {'pipe': 2, 'black_list': [0x1122, 0x2211]}},
{'hw_CANBusTriple': {'pipe': 1, 'action': 'write'}},
{'hw_USBtin' : {'pipe': 2, 'action': ‘write'}}
]
{'port':'auto', 'debug':1, 'speed':500},](https://image.slidesharecdn.com/cantoolz-160323174947/75/Testing-CAN-network-with-help-of-CANToolz-11-2048.jpg)
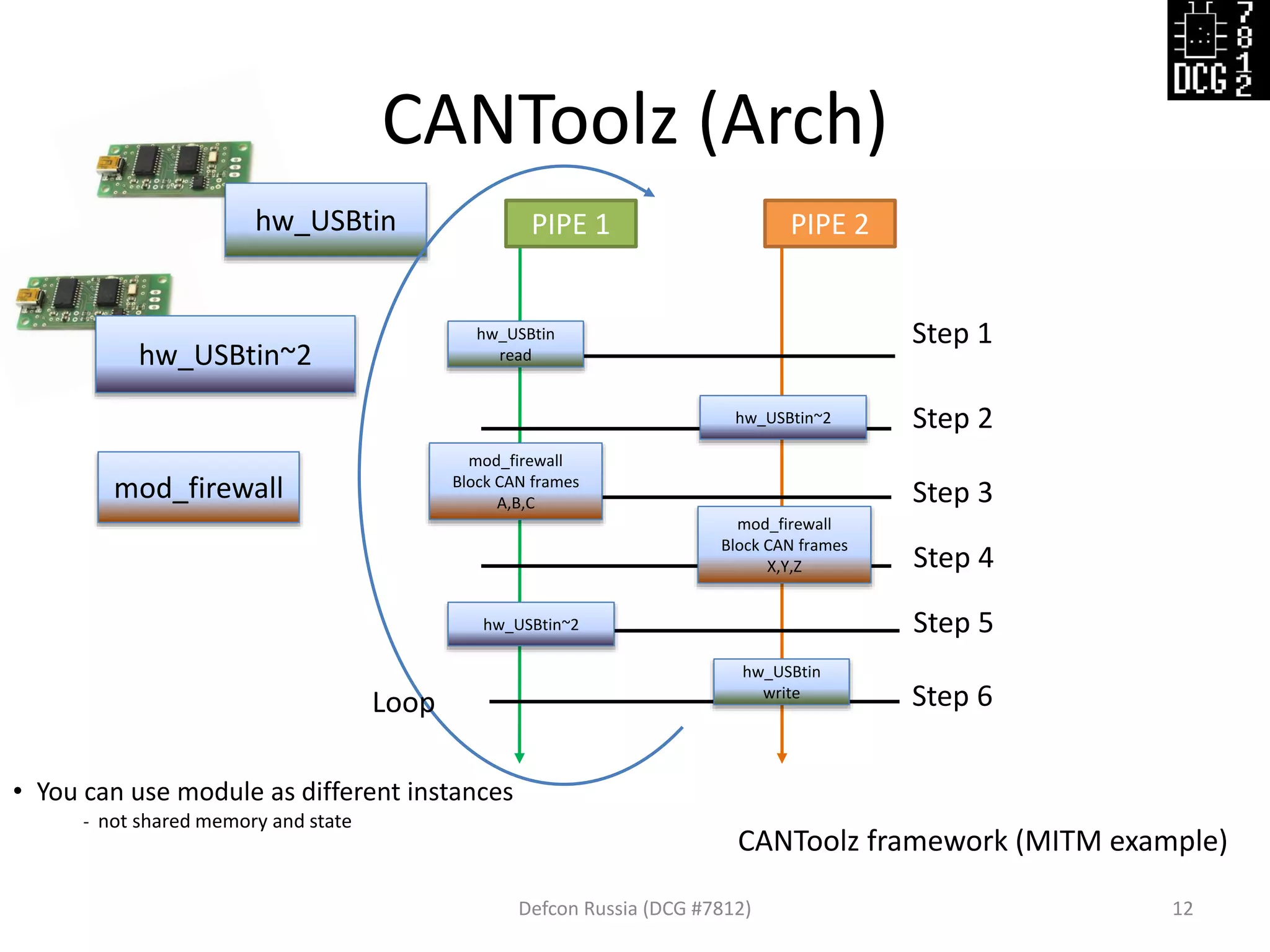
![Defcon Russia (DCG #7812) 13
# Load modules
load_modules = {
'hw_USBtin' :,
‘hw_USBtin~2' : ,
'mod_firewall' : {},
}
# Scenario with steps
actions = [
{'hw_USBtin' : {'pipe': 1, 'action': 'read'}},
{'hw_USBtin~2': {'pipe': 2, 'action': 'read'}},
{'mod_firewall' : {'pipe': 1, 'black_list': [1337, 31337]}},
{'mod_firewall' : {'pipe': 2, 'black_list': [0x1122, 0x2211]}},
{'hw_USBtin~2': {'pipe': 1, 'action': 'write'}},
{'hw_USBtin' : {'pipe': 2, 'action': ‘write'}}
]
Config file example:
{'port':'auto', 'debug':1, 'speed':500},
{'port':'auto', 'debug':1, 'speed':500, ‘bus':62},](https://image.slidesharecdn.com/cantoolz-160323174947/75/Testing-CAN-network-with-help-of-CANToolz-13-2048.jpg)
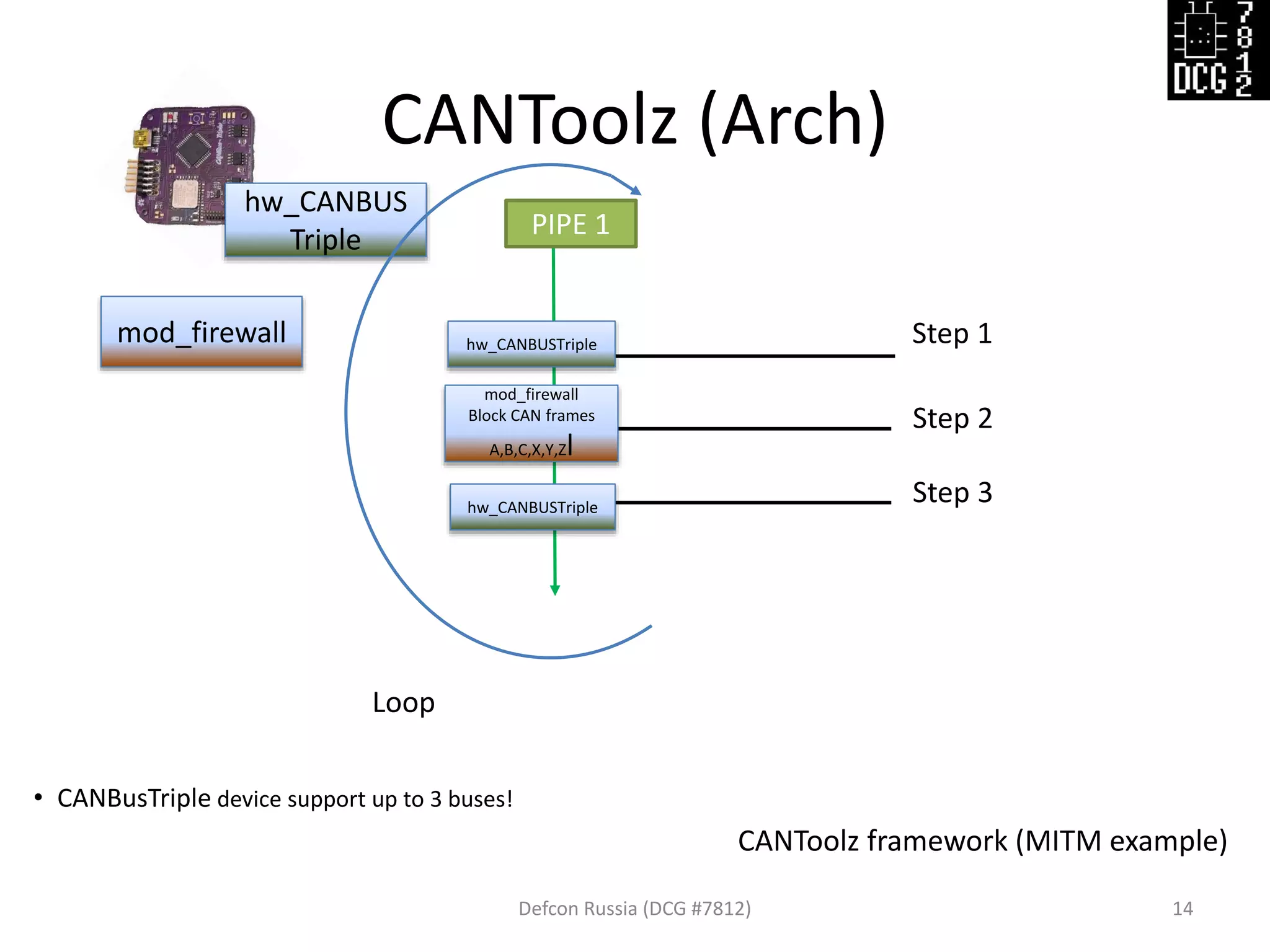
![Defcon Russia (DCG #7812) 15
# Load modules
load_modules = {
'hw_CANBUSTriple': {'bus_1': 1, 'bus_2': 2}, # Init parameters
'mod_firewall' : {},
}
# Scenario with steps
actions = [
{'hw_CANBUSTriple' : {'pipe': 1, 'action': 'read'}},
{'mod_firewall' : {'pipe': 1, 'black_list': [1337, 31337, 0x1122, 0x2211]}},
{'hw_CANBUSTriple' : {'pipe': 1, 'action': ‘write'}}
]
Config file example:](https://image.slidesharecdn.com/cantoolz-160323174947/75/Testing-CAN-network-with-help-of-CANToolz-15-2048.jpg)
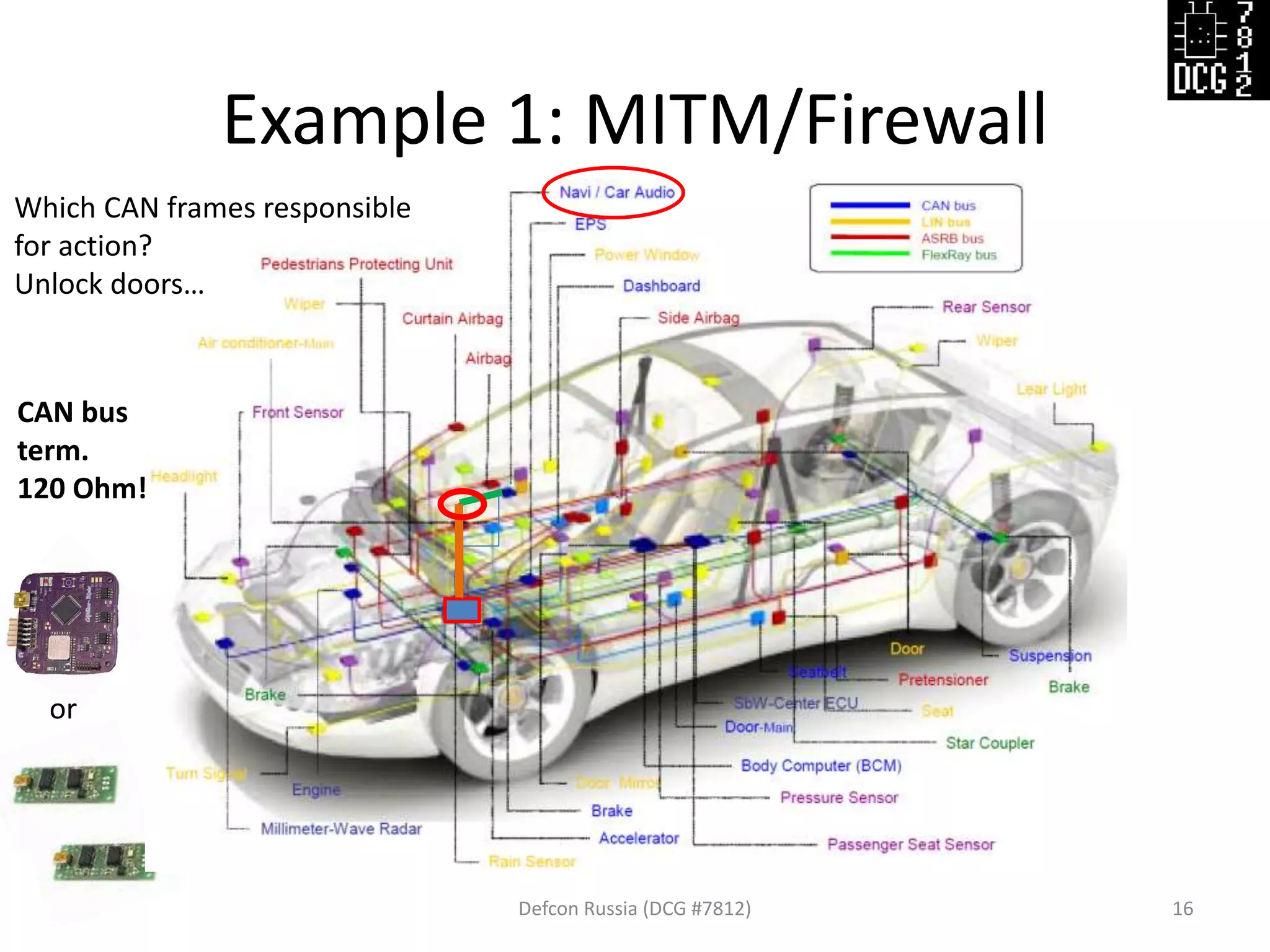
![Example 1: MITM/Firewall
Defcon Russia (DCG #7812) 17
# Load modules
load_modules = {
'mod_firewall' : {},
'mod_stat' : {},
'hw_USBtin' : {'port':'auto', 'debug':1, 'speed':500},
'hw_USBtin~2' : {'port':'auto', 'debug':1, 'speed':500,'bus':62}
}
# Scenario
actions = [
{'hw_USBtin' : {'action':'read'}},
{'mod_firewall' : {‘white_list':[1337]}},
{'hw_USBtin~2' : {'action':'read', 'pipe':2}},
{'mod_stat': {'pipe': 1}}, {'mod_stat': {'pipe': 2}},
{'hw_USBtin' : {'action':'write','pipe':2}},
{'hw_USBtin~2' : {'action':'write'}}
]](https://image.slidesharecdn.com/cantoolz-160323174947/75/Testing-CAN-network-with-help-of-CANToolz-17-2048.jpg)
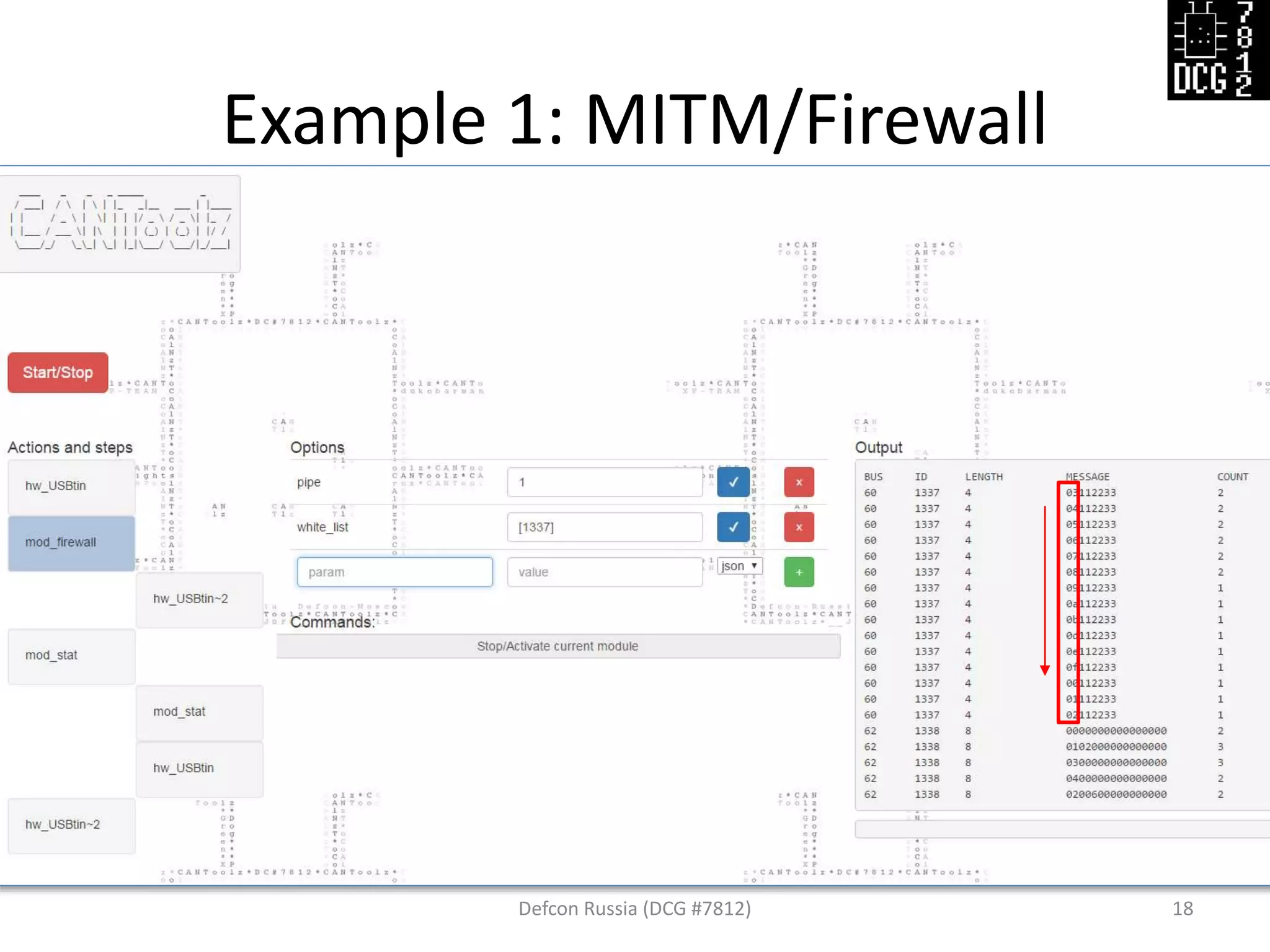
![Example 1: MITM/Firewall
Defcon Russia (DCG #7812) 19
black_body [[0,0x11,0x22,0x33]]](https://image.slidesharecdn.com/cantoolz-160323174947/75/Testing-CAN-network-with-help-of-CANToolz-19-2048.jpg)
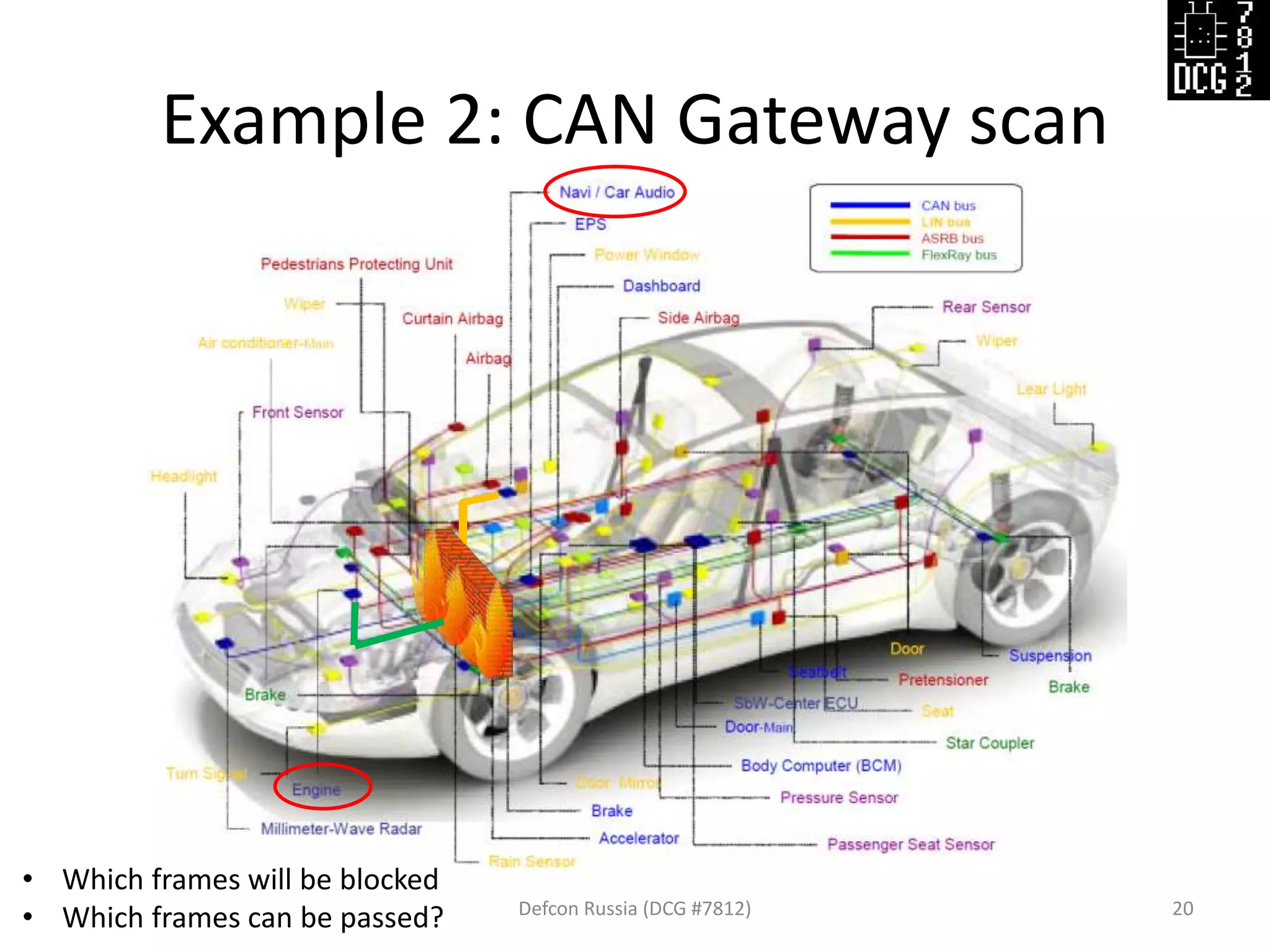
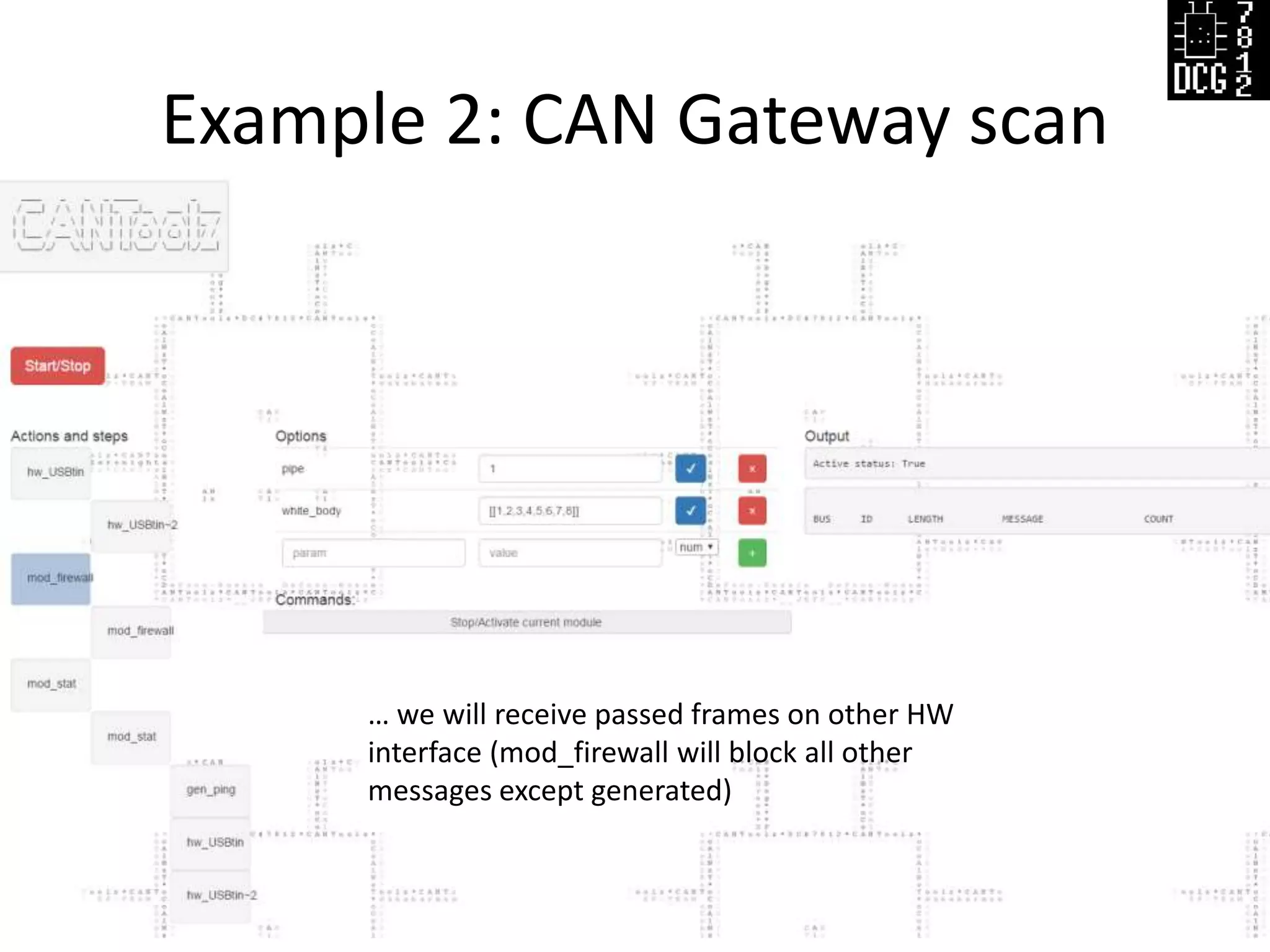
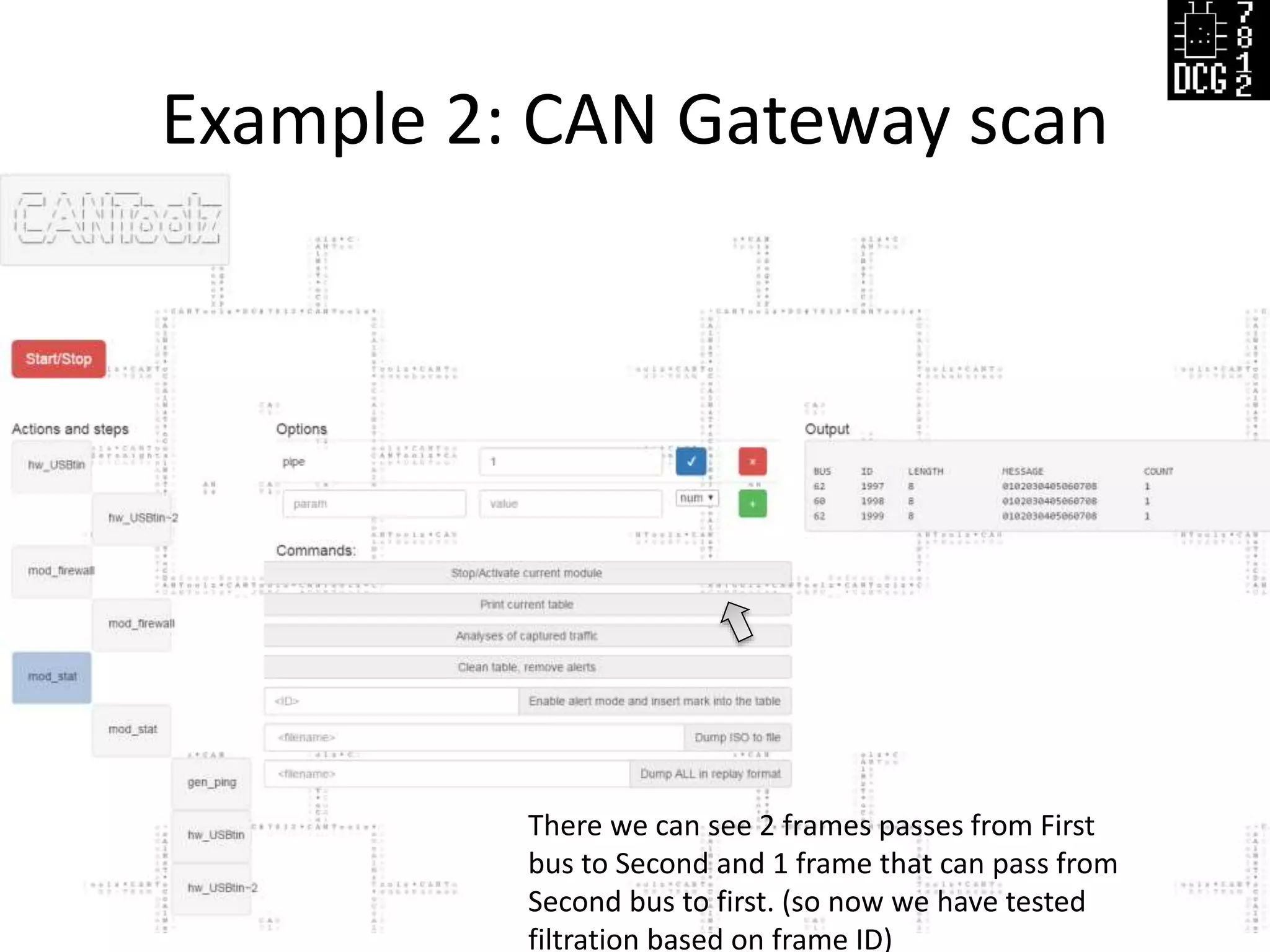
![Example 2: CAN Gateway scan
Defcon Russia (DCG #7812) 21
# Load needed modules
load_modules = {
# IO hardware module connected to first BUS (IVI)
'hw_USBtin': {'port':'auto', 'debug':1, 'speed':500},
# IO hardware module (connected to OBD2)
'hw_USBtin~2': {'port':'auto', 'debug':1, 'speed':500, 'bus': 62 },
'gen_ping' : {}, # Generator/Ping
'mod_firewall': {}, # We need firewall to block all other packets
'mod_stat': {} # Mod stat to see results
}
actions = [
{'hw_USBtin': {'action': 'read','pipe': 1}}, # Read to PIPE 1 from IVI
{'hw_USBtin~2': {'action': 'read','pipe': 2}}, # Read to PIPE 2 from OBD2 port
# Block all other CAN frames, but let frames with
# data "x01x02x03x04x05x06x07x08" pass
{'mod_firewall': {'white_body':[[1,2,3,4,5,6,7,8]],'pipe': 1}},
{'mod_firewall': {'white_body':[[1,2,3,4,5,6,7,8]], 'pipe': 2}},
{'mod_stat': {'pipe': 1}}, {'mod_stat': {'pipe': 2}}, # read from both pipes after filtration
{'gen_ping': {'range': [1,2000],'mode':'CAN','body':'0102030405060708','pipe':3}},
# Generate CAN frames to PIPE 3
{'hw_USBtin': {'pipe': 3, 'action': 'write'}},# Write generated packets to both buses
{'hw_USBtin~2': {'pipe': 3, 'action': 'write'}}
]](https://image.slidesharecdn.com/cantoolz-160323174947/75/Testing-CAN-network-with-help-of-CANToolz-21-2048.jpg)
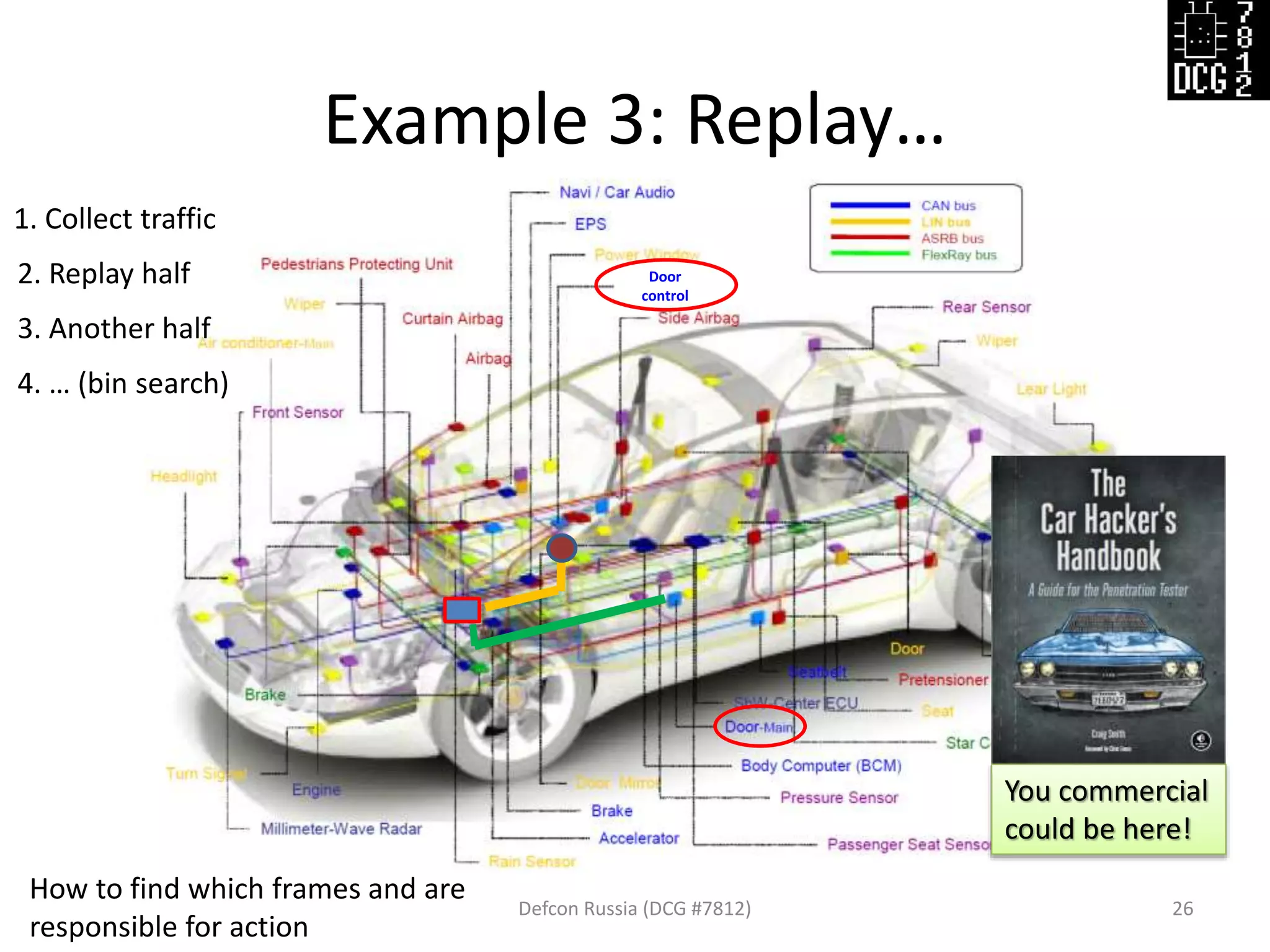
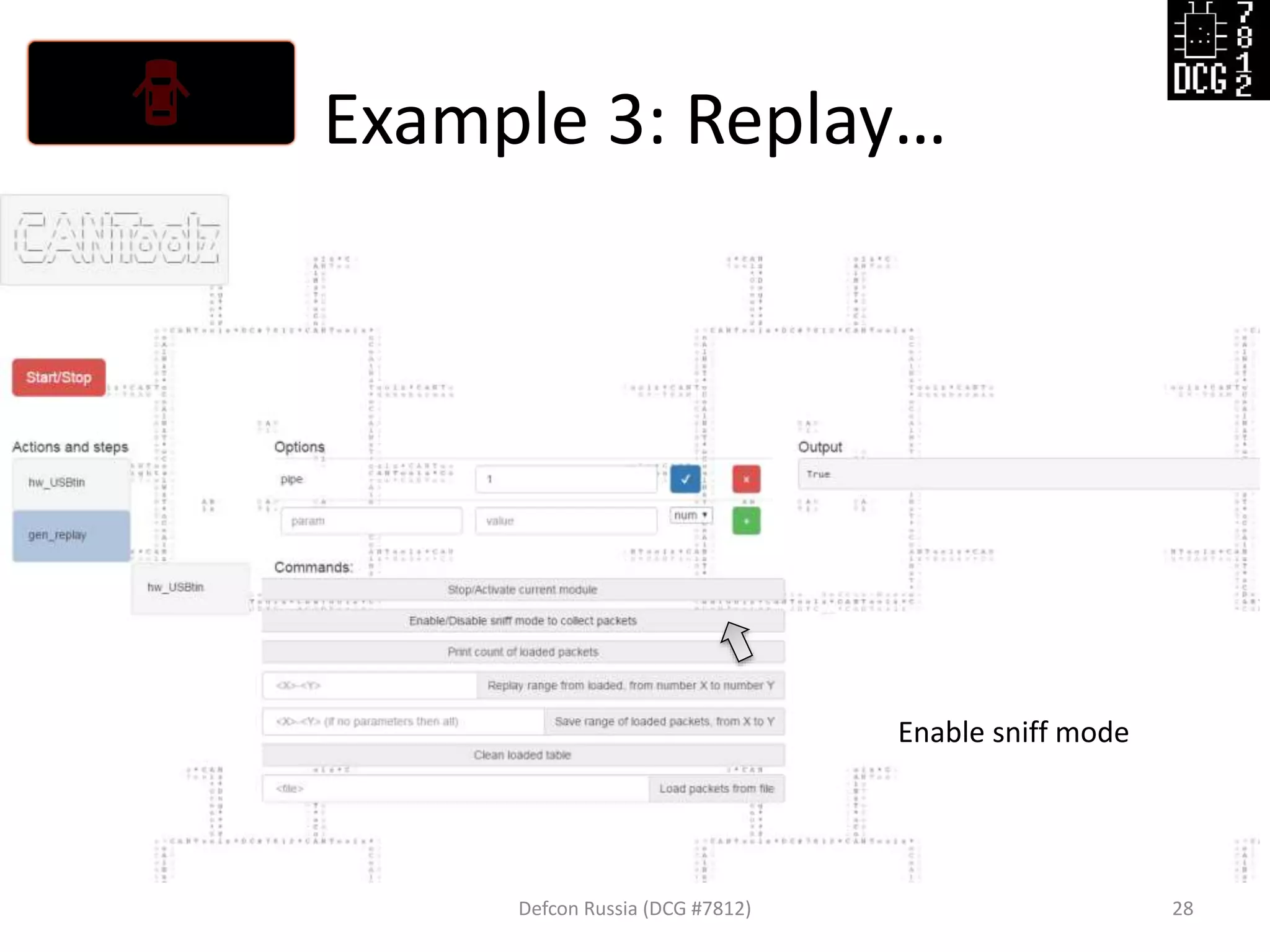
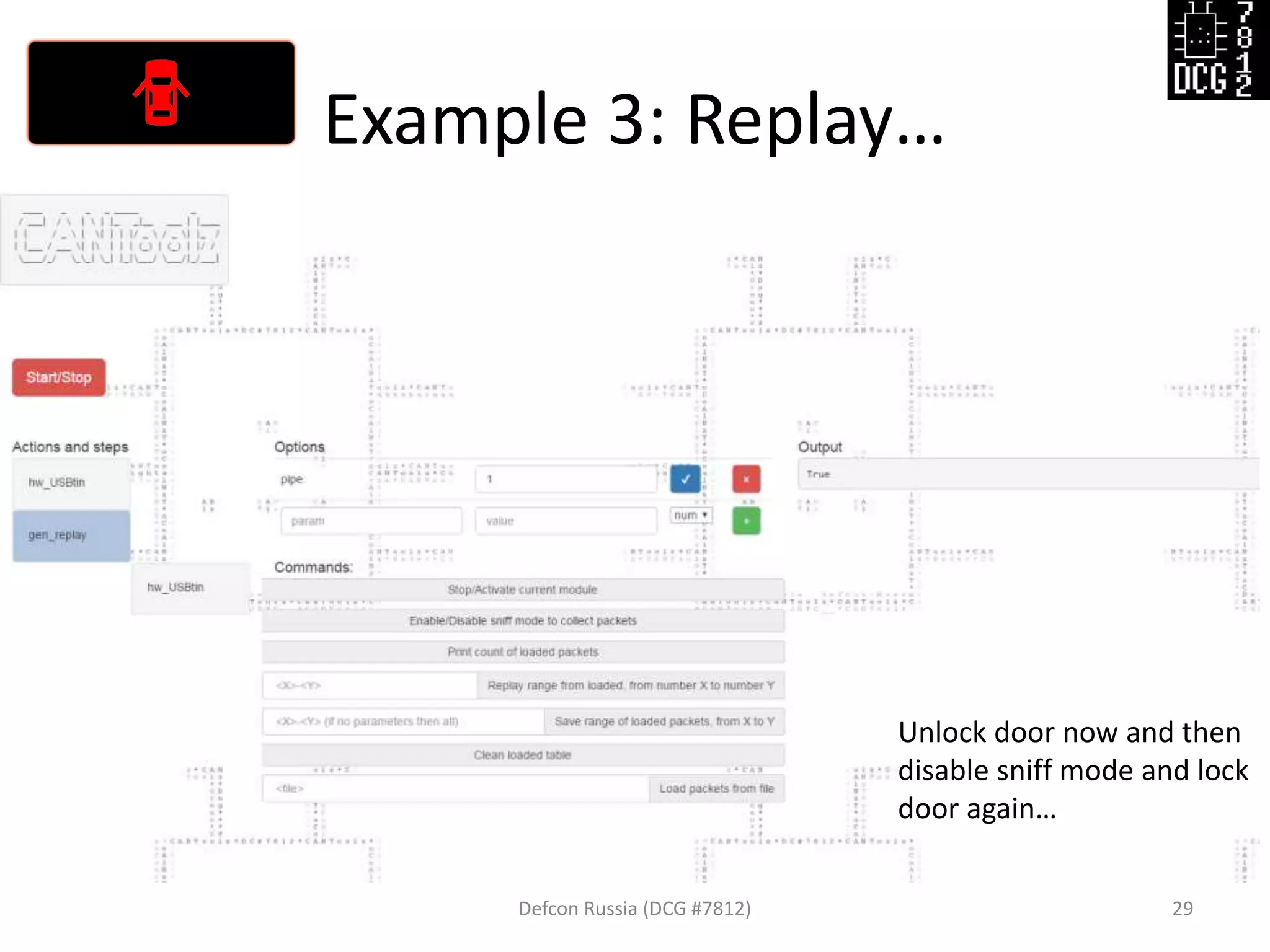
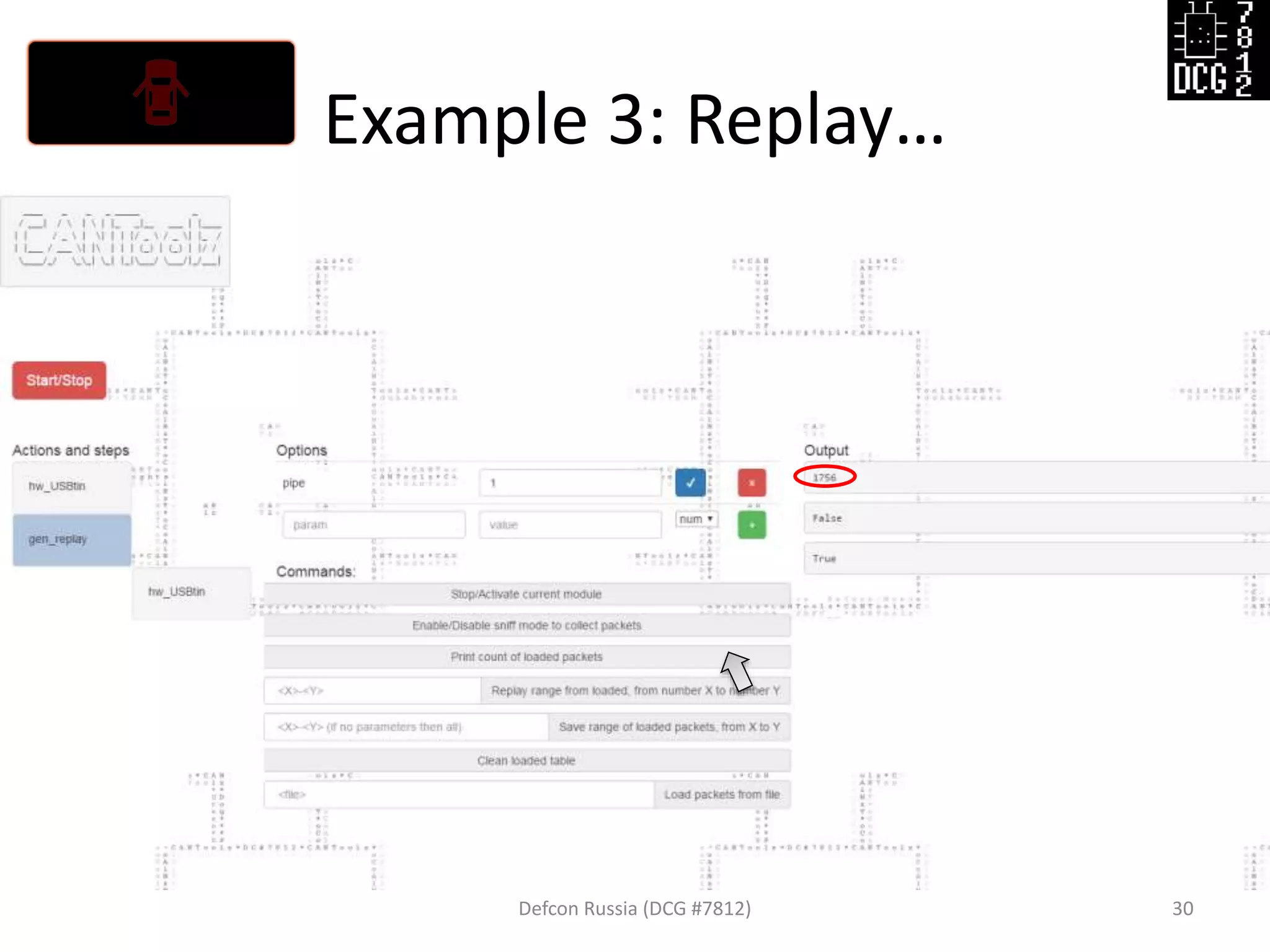
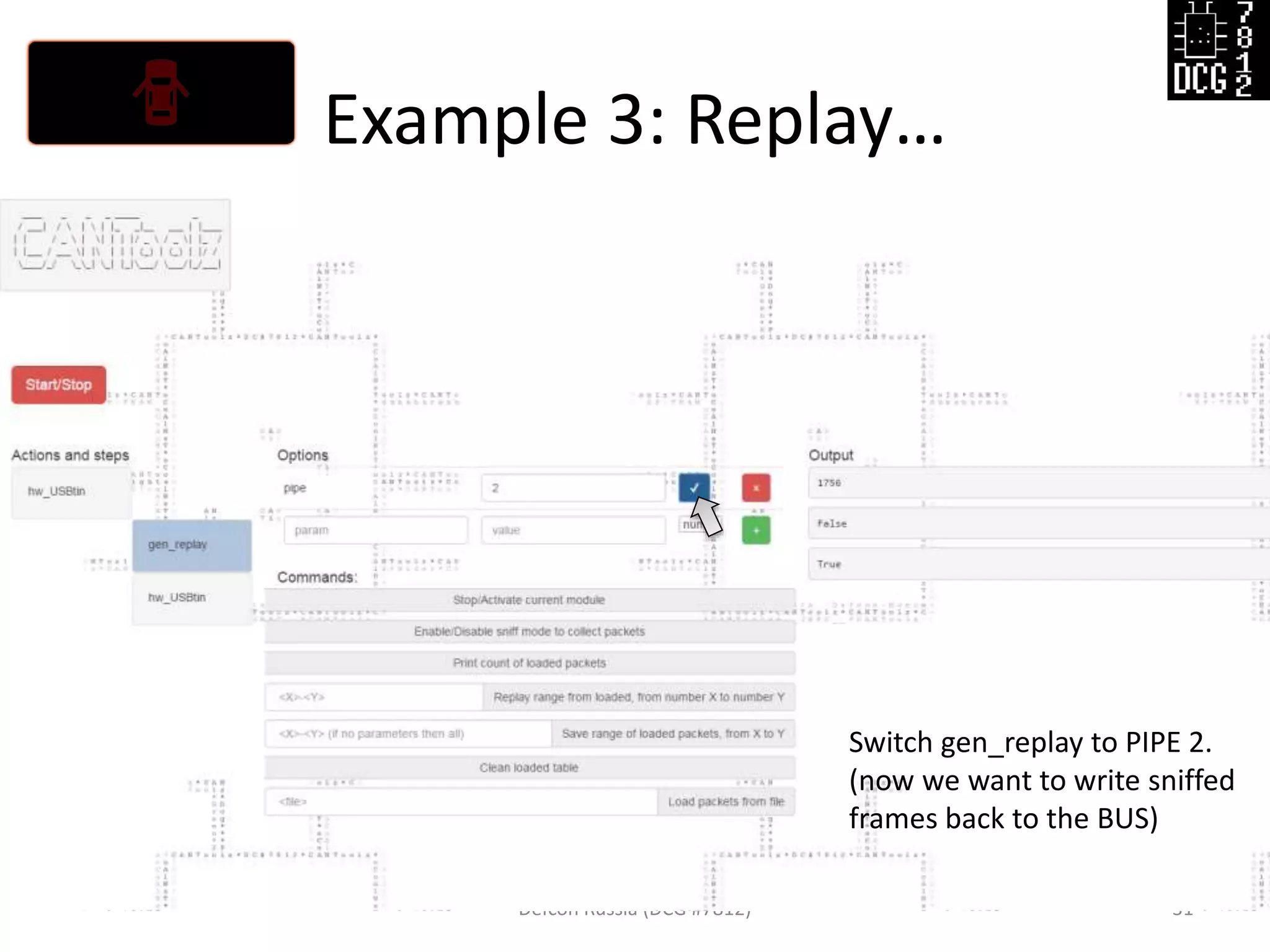
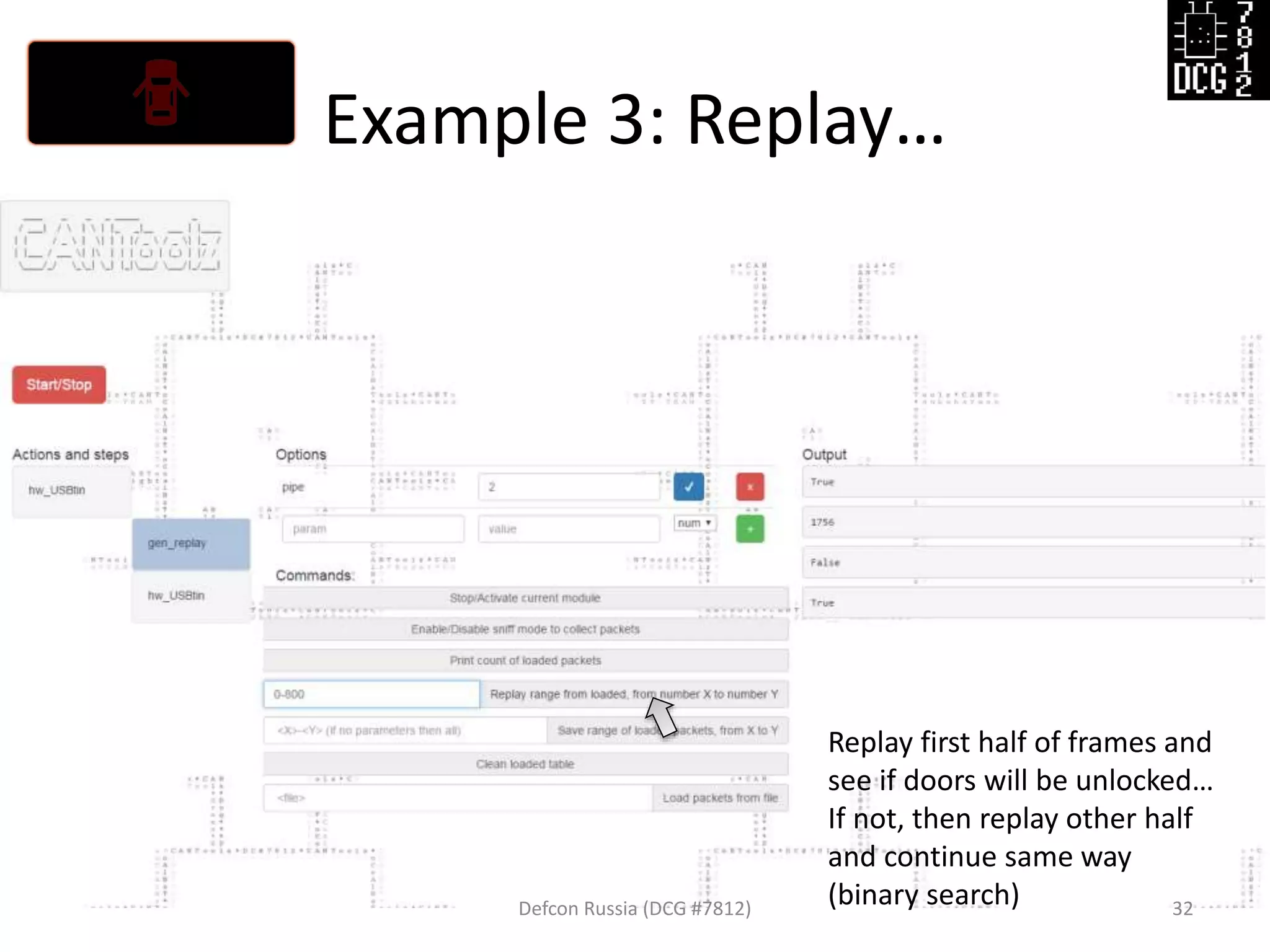
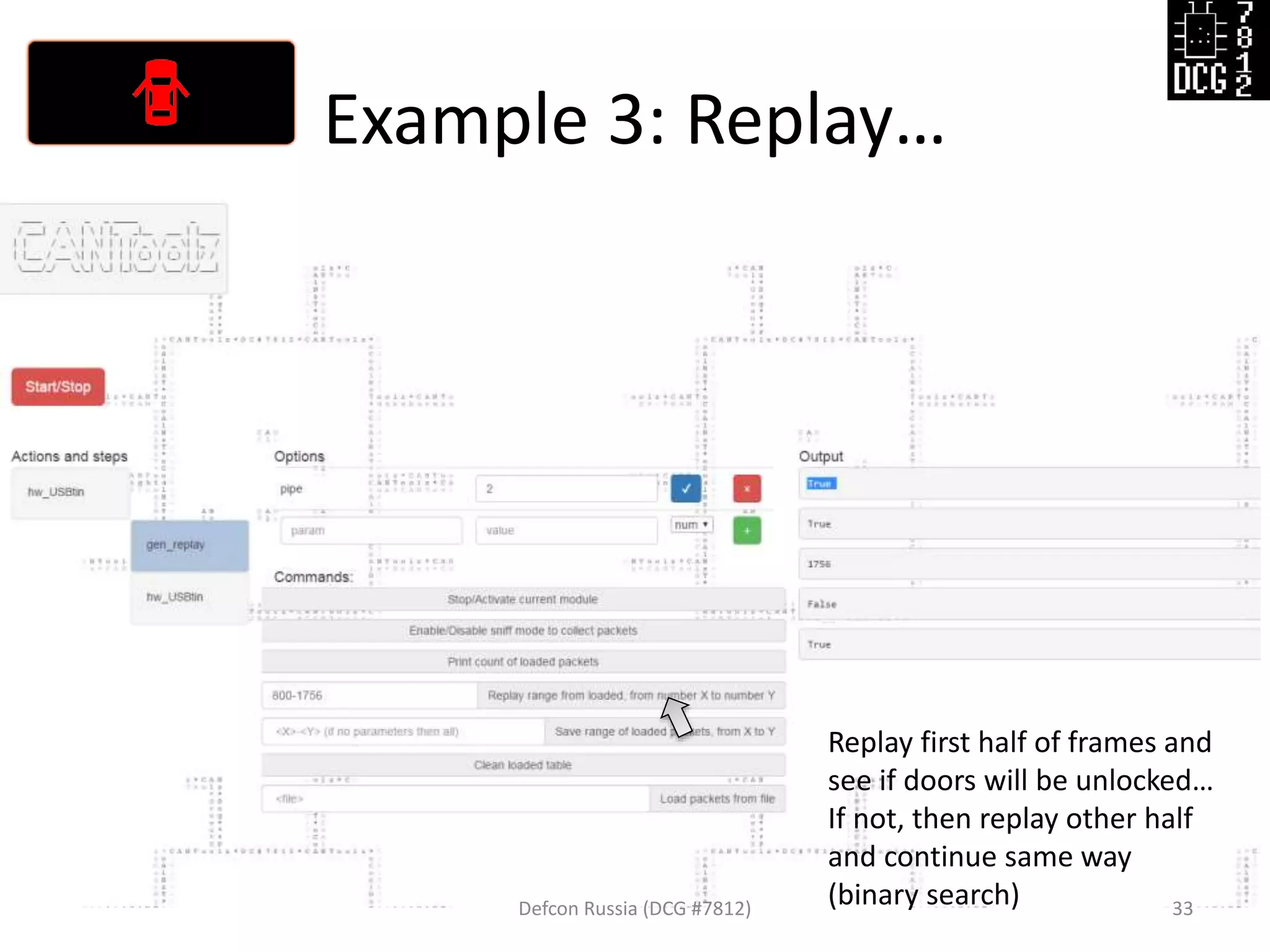
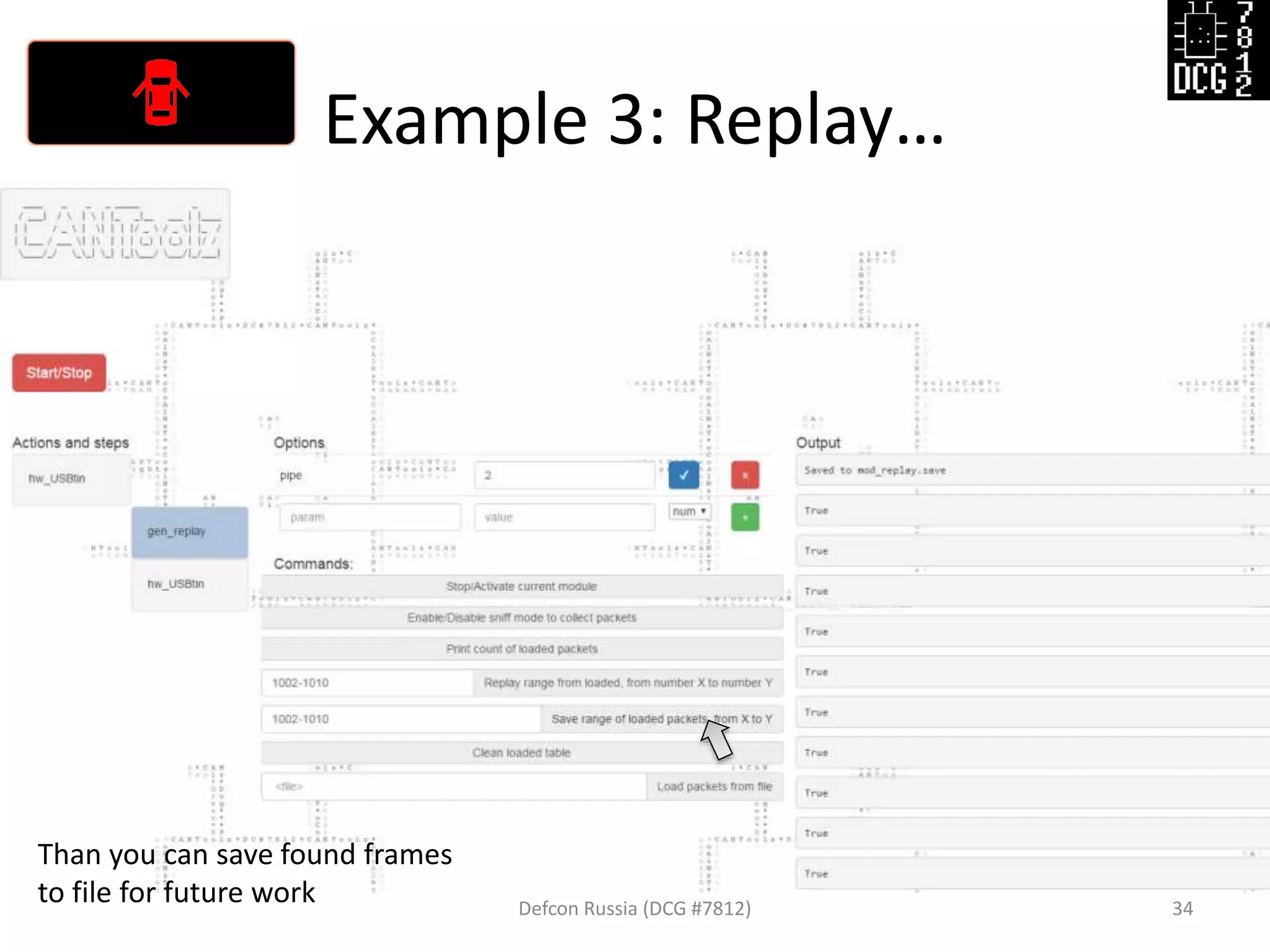
![Example 3: Replay…
Defcon Russia (DCG #7812) 27
load_modules = {
'hw_USBtin': {'port':'auto', 'debug':1, 'speed':500}, # IO hardware module
'gen_replay': {'debug': 1}, # Module for sniff and replay
'mod_stat': {} # Stats
}
# Now let's describe the logic of this test
actions = [
{'hw_USBtin': {'action': 'read','pipe': 1}}, # Read to PIPE 1
# We will sniff first from PIPE 1, then replay to PIPE 2
{'gen_replay': {'pipe': 1}},
{'hw_USBtin': {'action':'write','pipe': 2}} # Write generated packets (pings)
]](https://image.slidesharecdn.com/cantoolz-160323174947/75/Testing-CAN-network-with-help-of-CANToolz-27-2048.jpg)
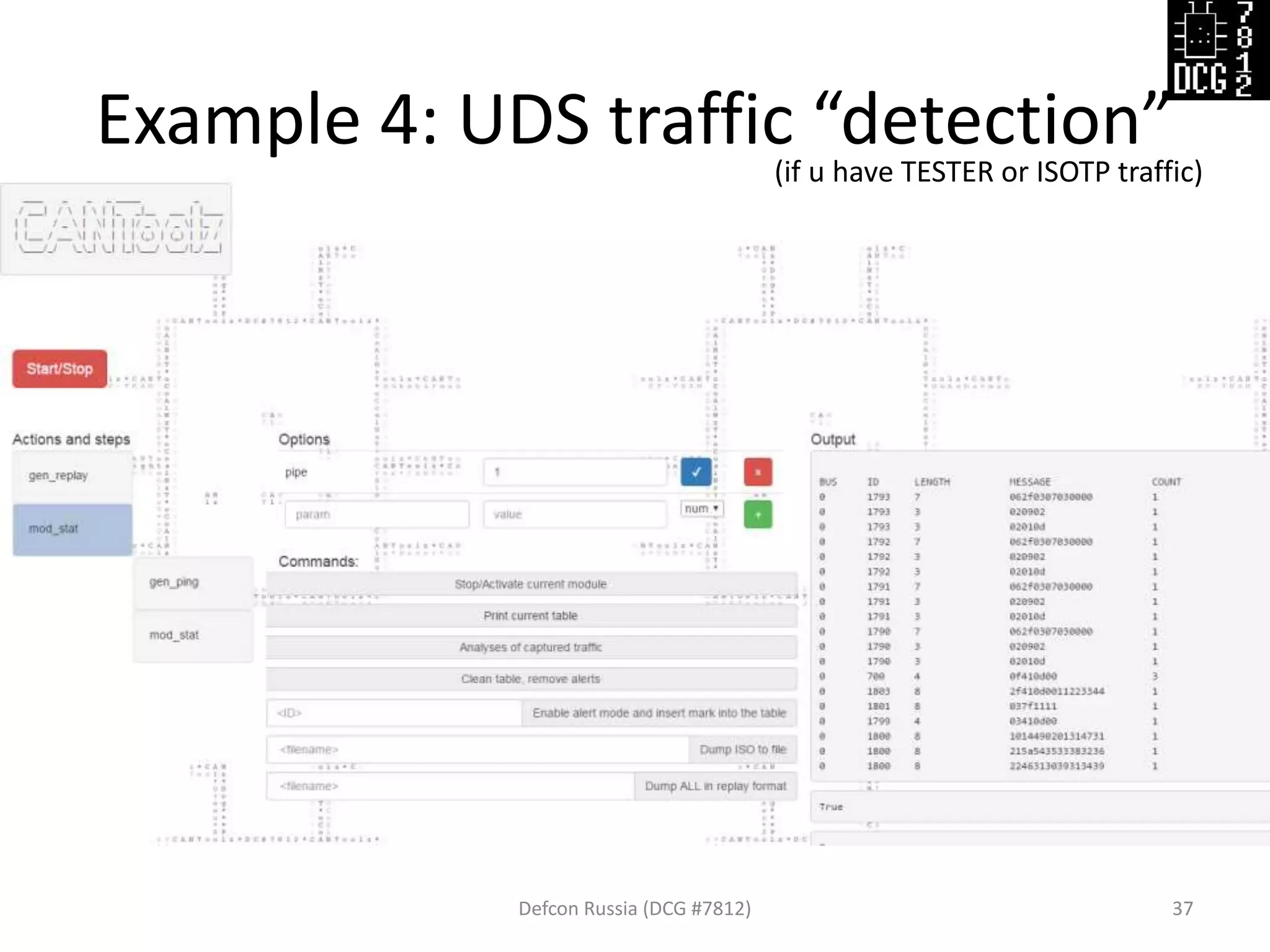
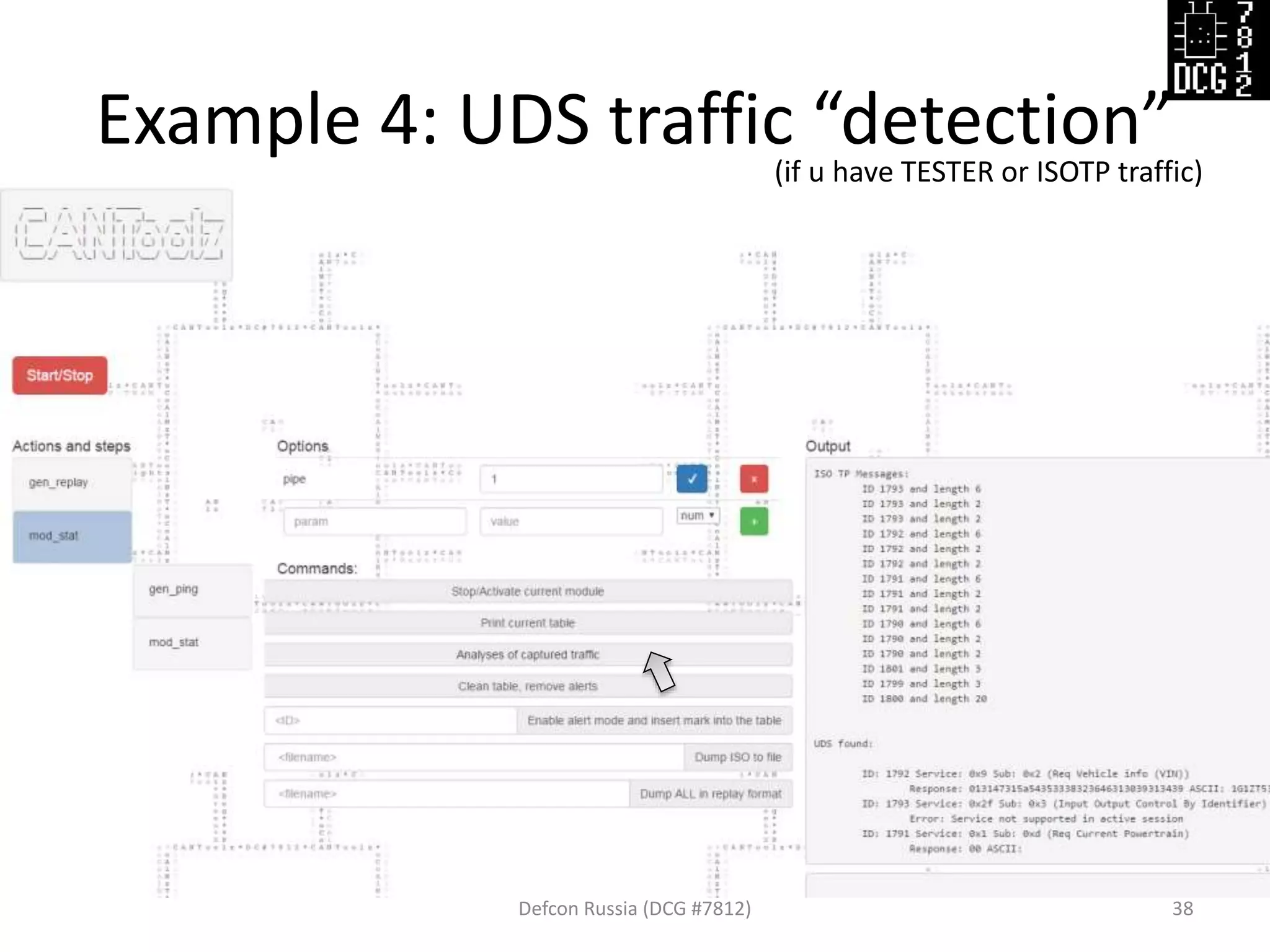
![Example 4.5: UDS “Scan/Ping”
Defcon Russia (DCG #7812) 39
{'gen_ping' : {
'pipe':2,
'range': [1790, 1794],
'services':[
{'service':0x01, 'sub':0x0d},
{'service':0x09, 'sub':0x02},
{'service':0x2F, 'sub':0x03,
'data':[7,3,0,0]}],
'mode':'UDS'}
Then listen “replay” with mod_stat and do anlysis of overall traffic](https://image.slidesharecdn.com/cantoolz-160323174947/75/Testing-CAN-network-with-help-of-CANToolz-39-2048.jpg)
![# Load modules
load_modules = {
'gen_fuzz': {},
'hw_USBtin' : {'port':'auto', 'debug':1, 'speed':500},
'mod_stat': {}
}
# Scenario
actions = [
# Fizz frames with ID: 222 and 555-999. Fuzz only first byte (index 0)
{'gen_fuzz' : {'index':[0],'id': [222,[555,999]], 'data': [0,0,0,0,0,0,0,0]
'delay': 0}},
# Write generated packets
{'hw_USBtin' : {'action':'write'}},
# Read response
{'hw_USBtin' : {'action':'read', 'pipe': 2}},
{'mod_stat': {'pipe': 2}}
]
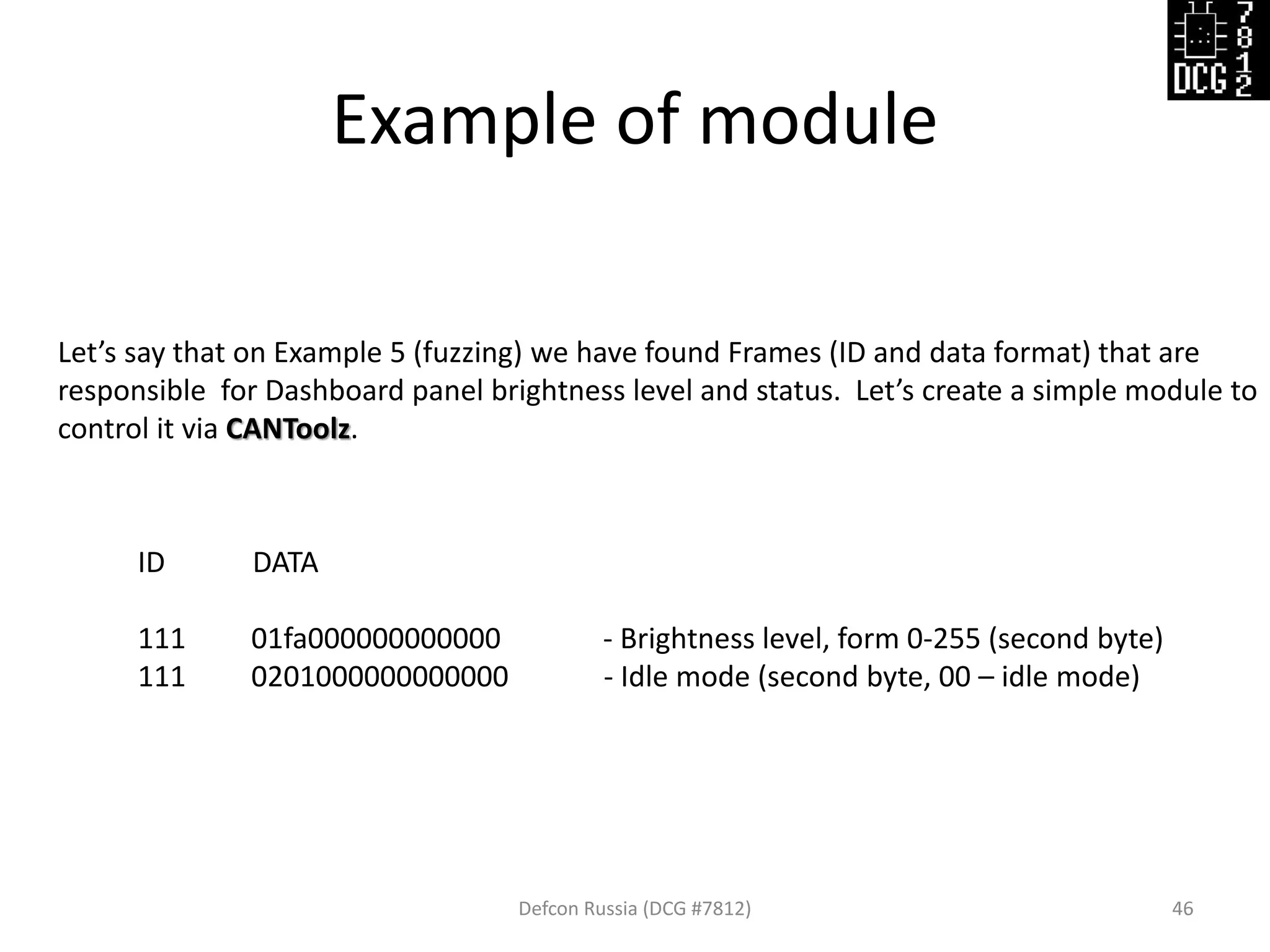
Example 5: Fuzzer (discovery, UDS, etc)
Defcon Russia (DCG #7812) 40
Run fuzzer and see results:
• Brightness level of something
have been changed something
• Blinking of something
• Got new ID in response](https://image.slidesharecdn.com/cantoolz-160323174947/75/Testing-CAN-network-with-help-of-CANToolz-40-2048.jpg)

![Init parameters and commands
Defcon Russia (DCG #7812) 43
def do_init(self, params):
if 'save_to' in params:
…
self._cmdList['p'] = ["Print count of loaded packets", 0, "", self.cnt_print]
self._cmdList['r'] = ["Replay range from loaded, from number X to number Y",
1, " <X>-<Y> ", self.replay_mode]
This method will be called when module loaded into the project
list of commands that can be triggered any time
Number of parameters of command
Command’s parameters format (just help)
Actual method that will be called by triggering the command](https://image.slidesharecdn.com/cantoolz-160323174947/75/Testing-CAN-network-with-help-of-CANToolz-43-2048.jpg)

![# handle message in the pipe
def do_effect(self, can_msg, args):
if can_msg.CANData:
if 'black_list' in args and can_msg.CANFrame.frame_id in args.get('black_list', []):
can_msg.CANData = False
return can_msg
Main action (CAN frame handling)
Defcon Russia (DCG #7812) 45
Main method
Message OUT
Arguments for current step
Flag, if message contains CAN frame
CAN Frame
Message IN](https://image.slidesharecdn.com/cantoolz-160323174947/75/Testing-CAN-network-with-help-of-CANToolz-45-2048.jpg)
![Example of module(code)
Defcon Russia (DCG #7812) 47
from libs.module import *
from libs.can import *
import copy
class mod_panel_control(CANModule):
name = "Panel control module"
help = """
This module change dahsboard panel things.
Init parameters: None
Module parameters:
'pipe' - integer, 1 or 2 - from which pipe to print, default 1
"""
def do_init(self, params):
self._active = True
self._cmdList['1'] = ["Idle mode on", 0, "", self.turn_off]
self._cmdList['0'] = ["Idle mode off", 0, "", self.turn_on]
self._cmdList['b'] = ["Change brightness level (0 - 255)", 1, "<level>",
self.change_level]
self._frame = None](https://image.slidesharecdn.com/cantoolz-160323174947/75/Testing-CAN-network-with-help-of-CANToolz-47-2048.jpg)
![Example of module(code)
Defcon Russia (DCG #7812) 48
# Effect (could be fuzz operation, sniff, filter or whatever)
def do_effect(self, can_msg, args):
if self._frame:
can_msg.CANFrame = copy.deepcopy(self._frame)
can_msg.CANData = True
self._frame = None
return can_msg
def turn_off(self):
self._frame = CANMessage(111,8,[2,0,0,0,0,0,0,0], False, CANMessage.DataFrame)
def turn_on(self):
self._frame = CANMessage(111,8,[2,1,0,0,0,0,0,0], False, CANMessage.DataFrame)
def change_level(self, level):
b_level = int(level)
if 0 < b_level < 256:
self._frame = CANMessage(111,8,[1,b_level,0,0,0,0,0,0], False,
CANMessage.DataFrame)](https://image.slidesharecdn.com/cantoolz-160323174947/75/Testing-CAN-network-with-help-of-CANToolz-48-2048.jpg)
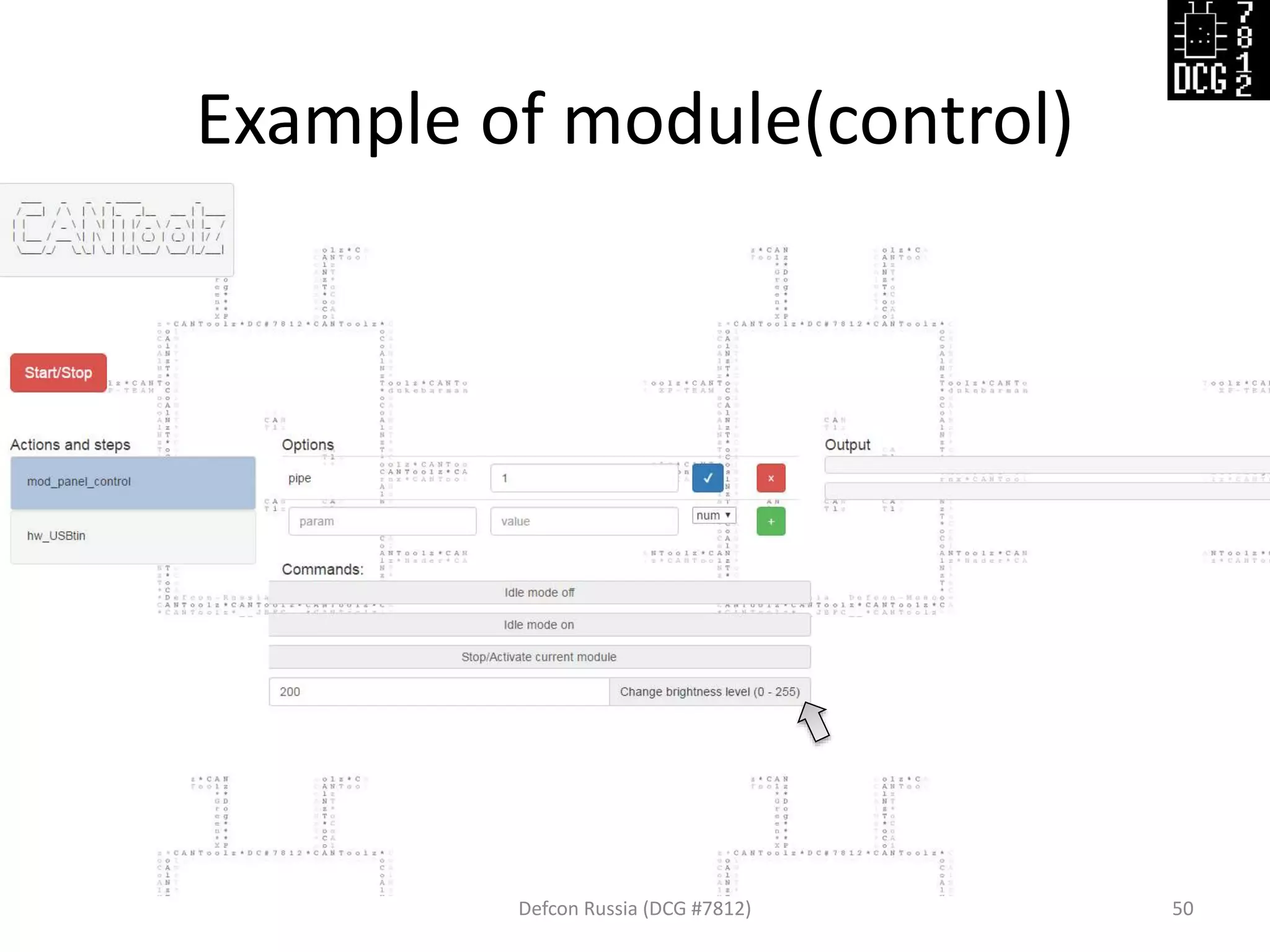
![Example of module(cfg)
Defcon Russia (DCG #7812) 49
# Load modules
load_modules = {
'mod_panel_control': {},
'hw_USBtin' : {'port':'auto', 'debug':1, 'speed':500},
}
# Scenario
actions = [
# Fizz frames with ID: 222 and 555-999. Fuzz only first byte (index 0)
{'mod_panel_control' : {}},
# Write generated packets
{'hw_USBtin' : {'action':'write'}}
]](https://image.slidesharecdn.com/cantoolz-160323174947/75/Testing-CAN-network-with-help-of-CANToolz-49-2048.jpg)