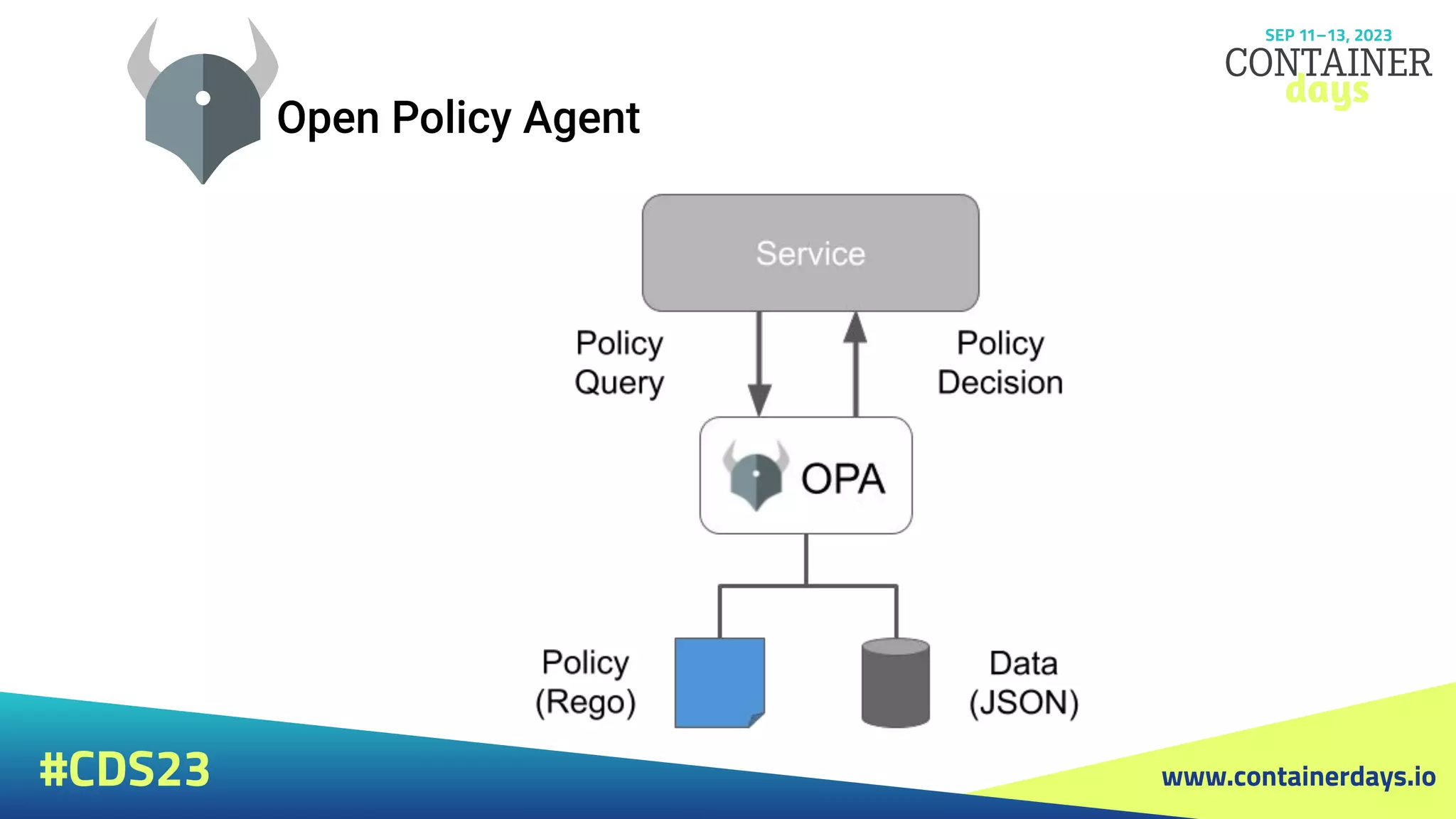
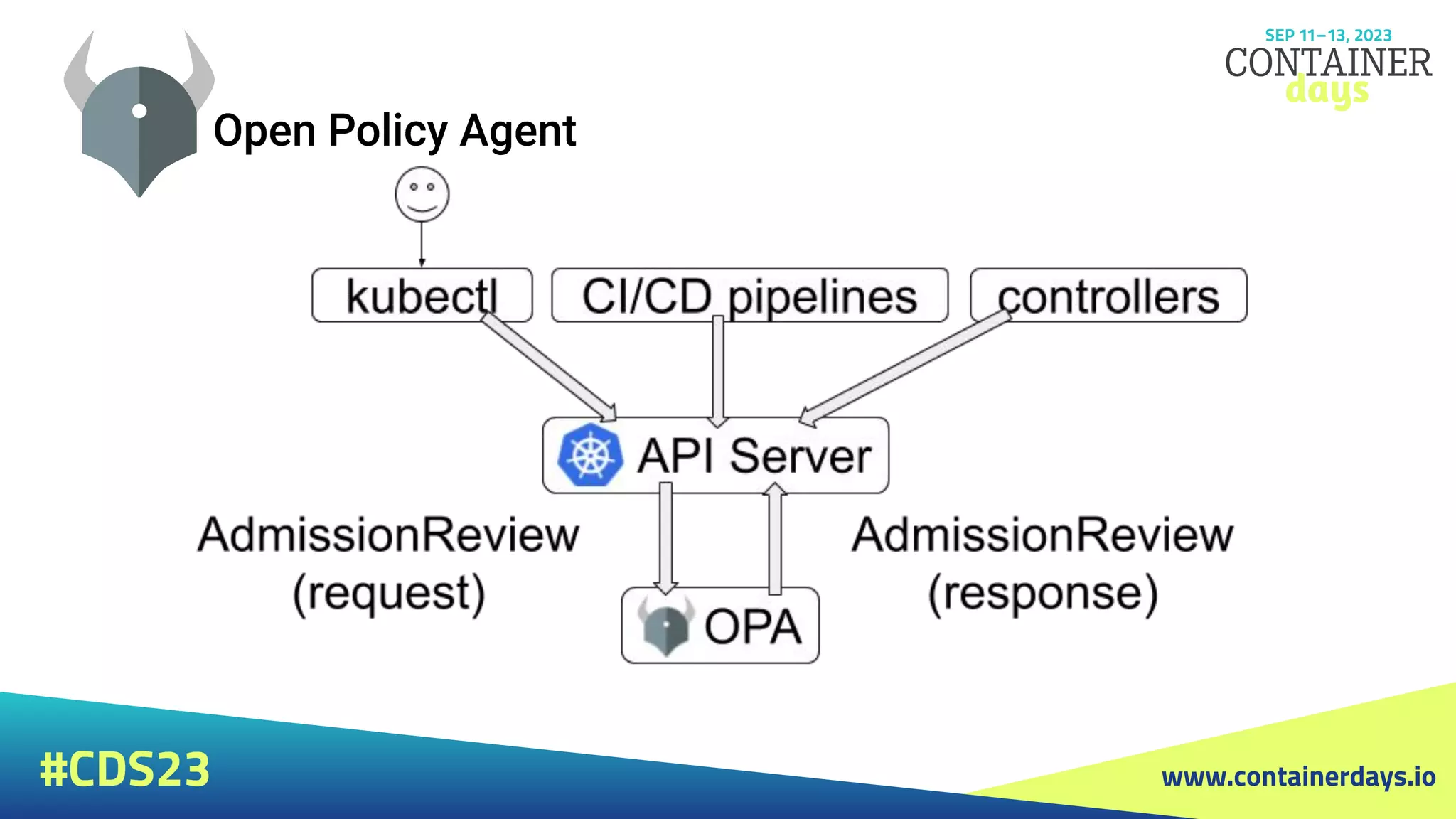
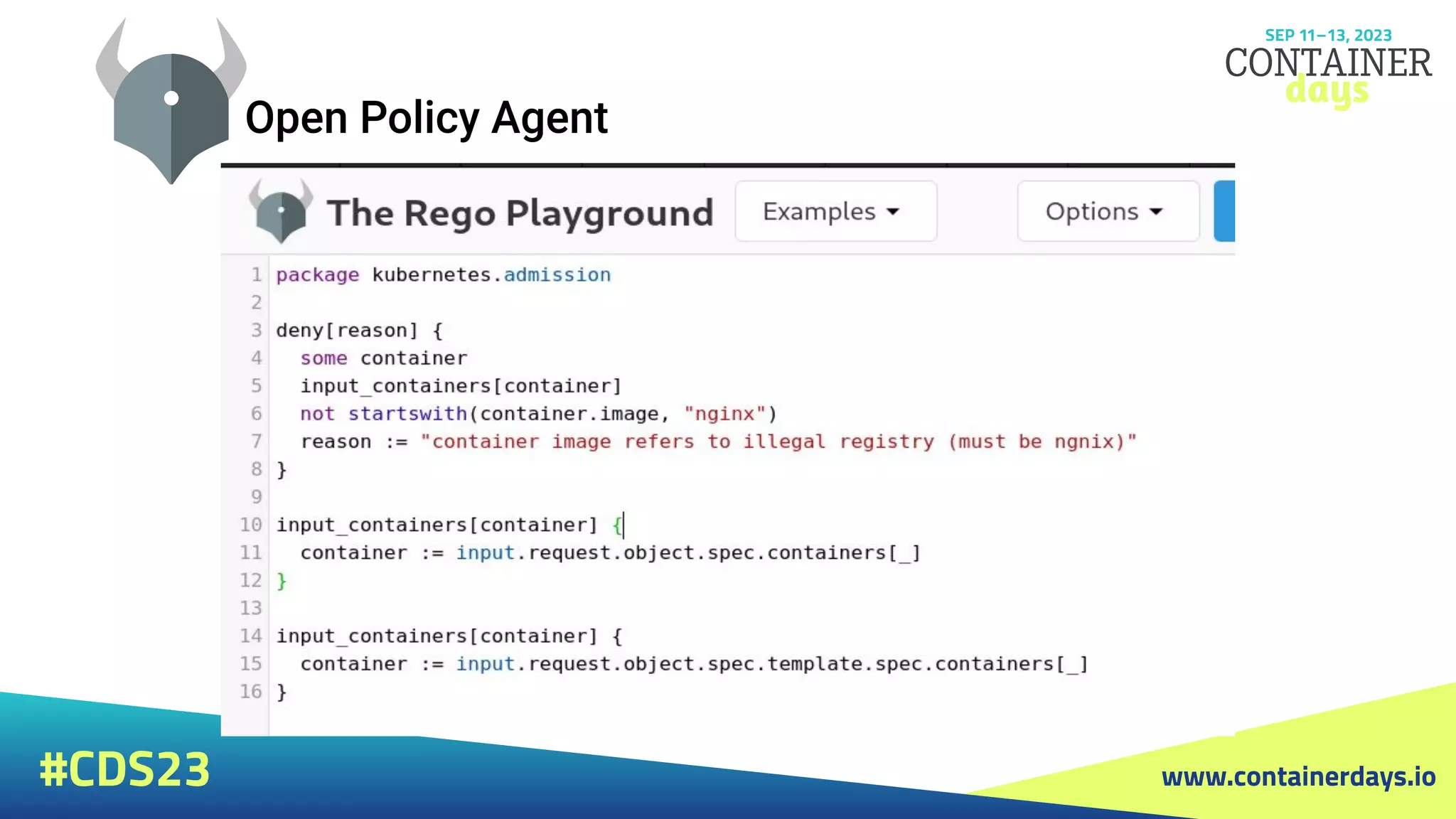
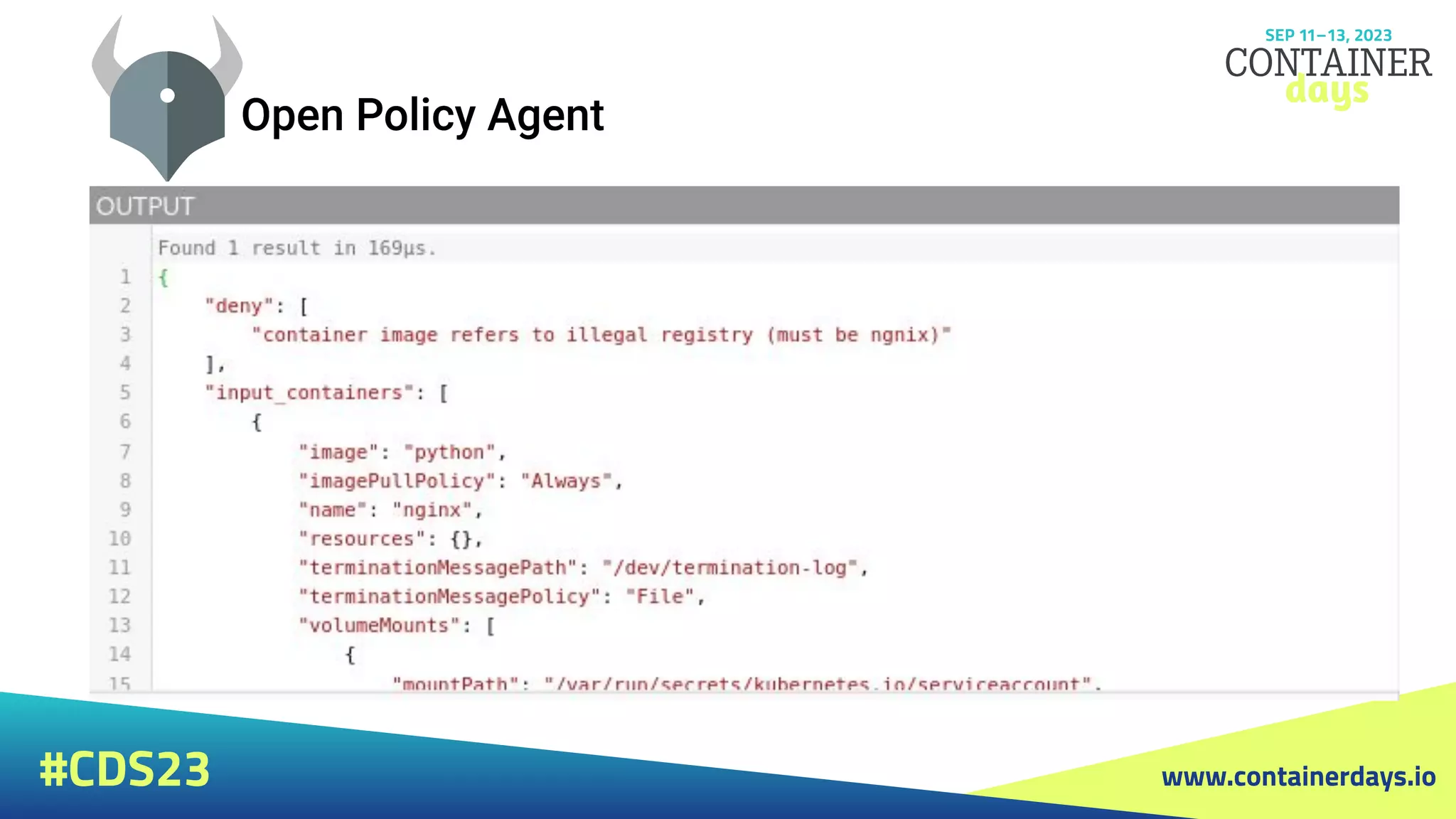
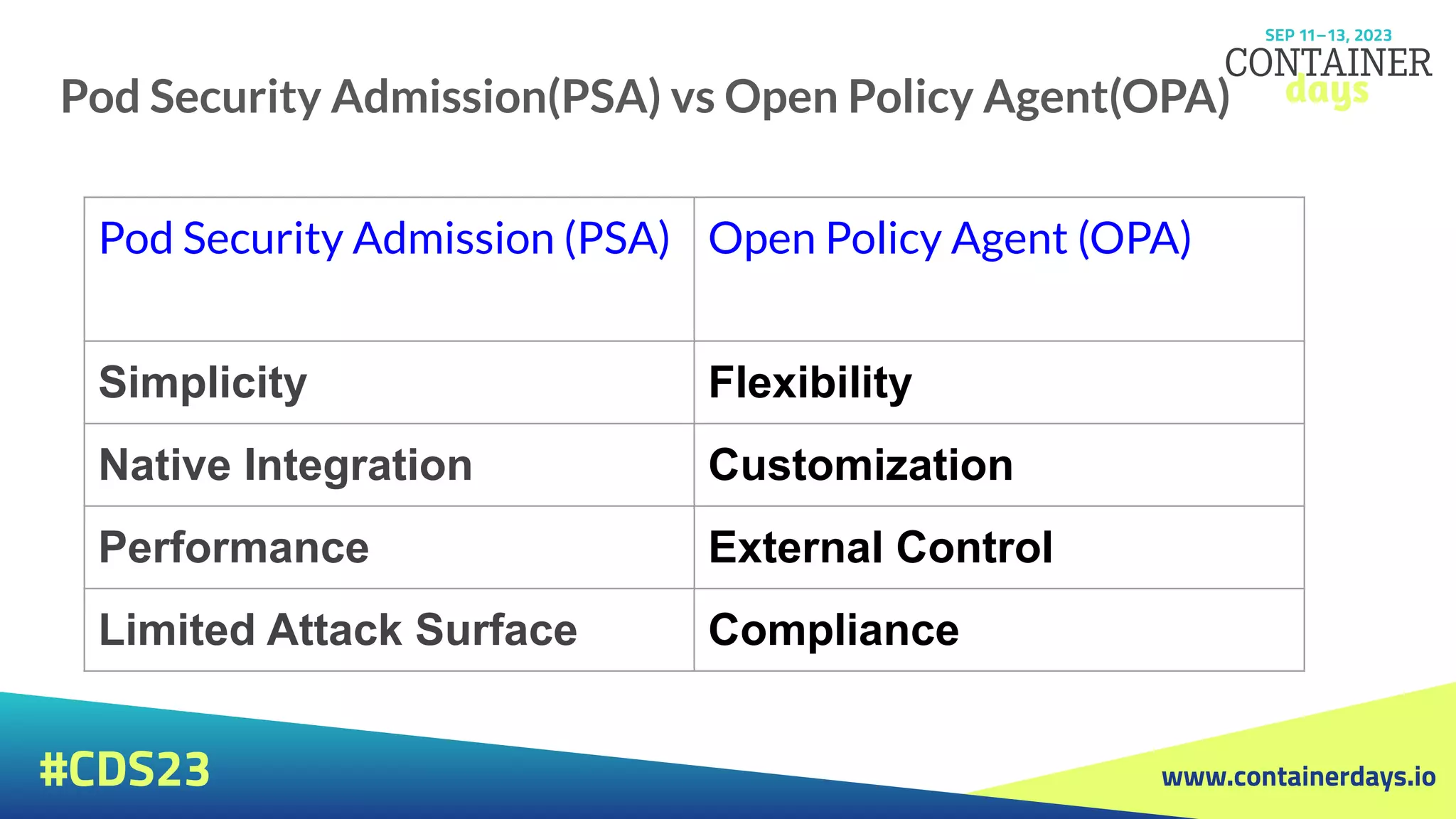
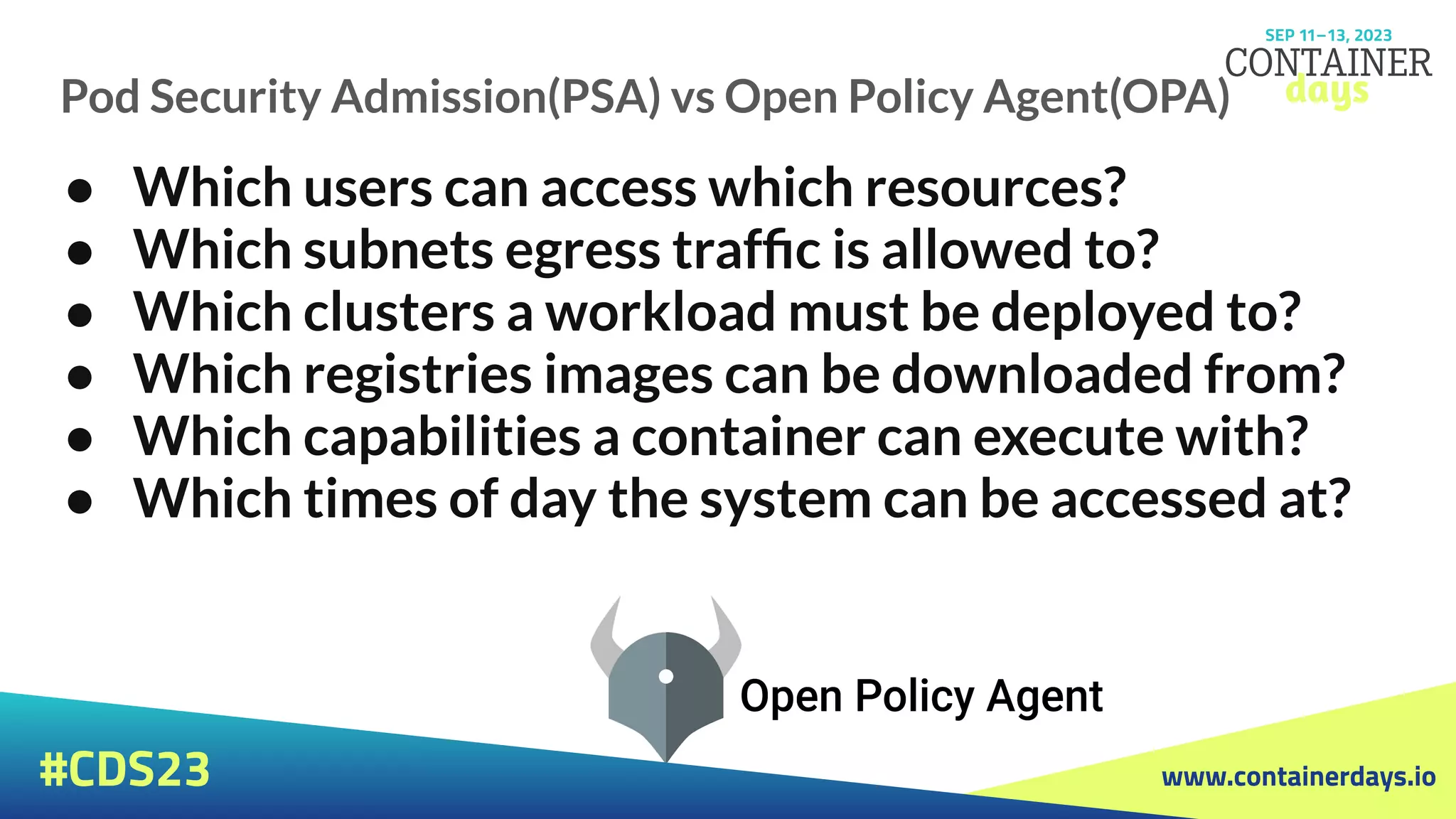
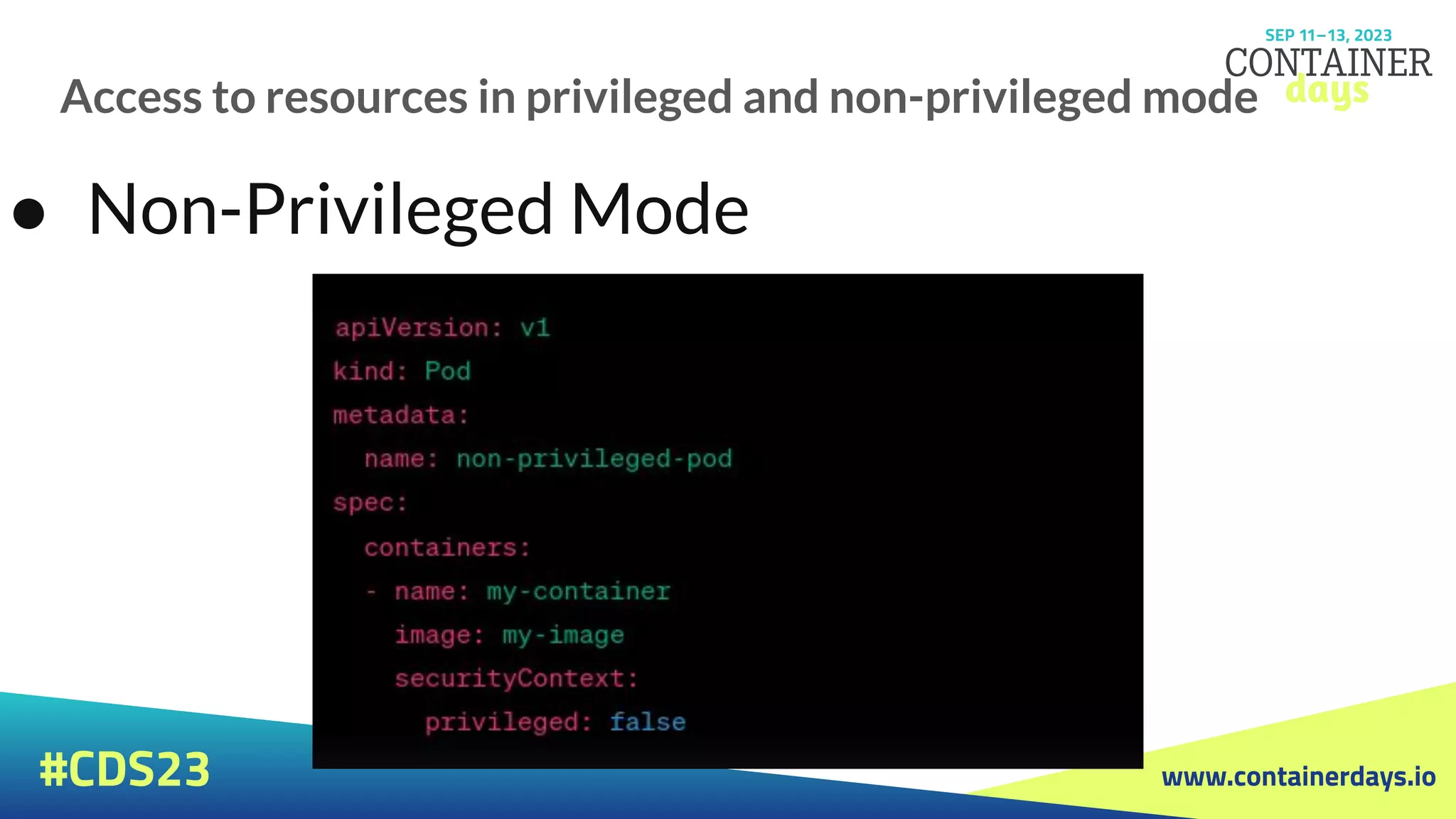
The document discusses evolving security strategies for Kubernetes (k8s) environments, including cluster hardening, pod security admission (PSA), and the integration of Open Policy Agent (OPA) for policy management. It highlights the importance of role-based access control (RBAC), resource quotas, and pod security contexts in enhancing security posture. Additionally, it contrasts PSA's simplicity with OPA's flexibility and customization options for governance in cloud-native applications.






![www.containerdays.io
#CDS23
Security Context
apiVersion: v1
kind: Pod
metadata:
name: scd-3
spec:
containers:
- name: scd-3
image: nginx
securityContext:
capabilities:
add: ["NET_ADMIN","SYS_TIME"]](https://image.slidesharecdn.com/evolutionofsecuritystrategiesink8senvironments-230913110220-0a55196f/75/Evolution-of-security-strategies-in-K8s-environments-pdf-10-2048.jpg)


![www.containerdays.io
#CDS23
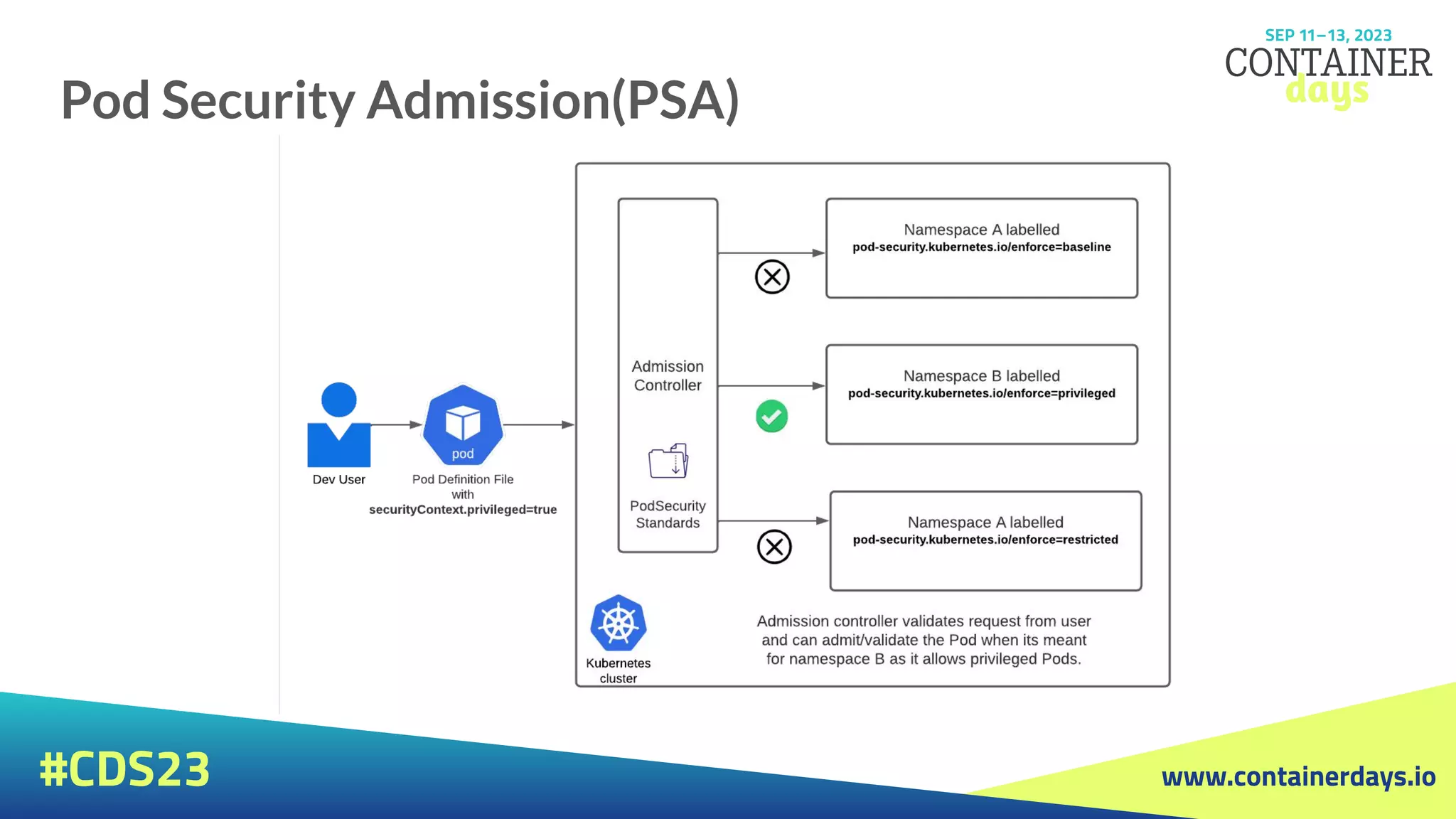
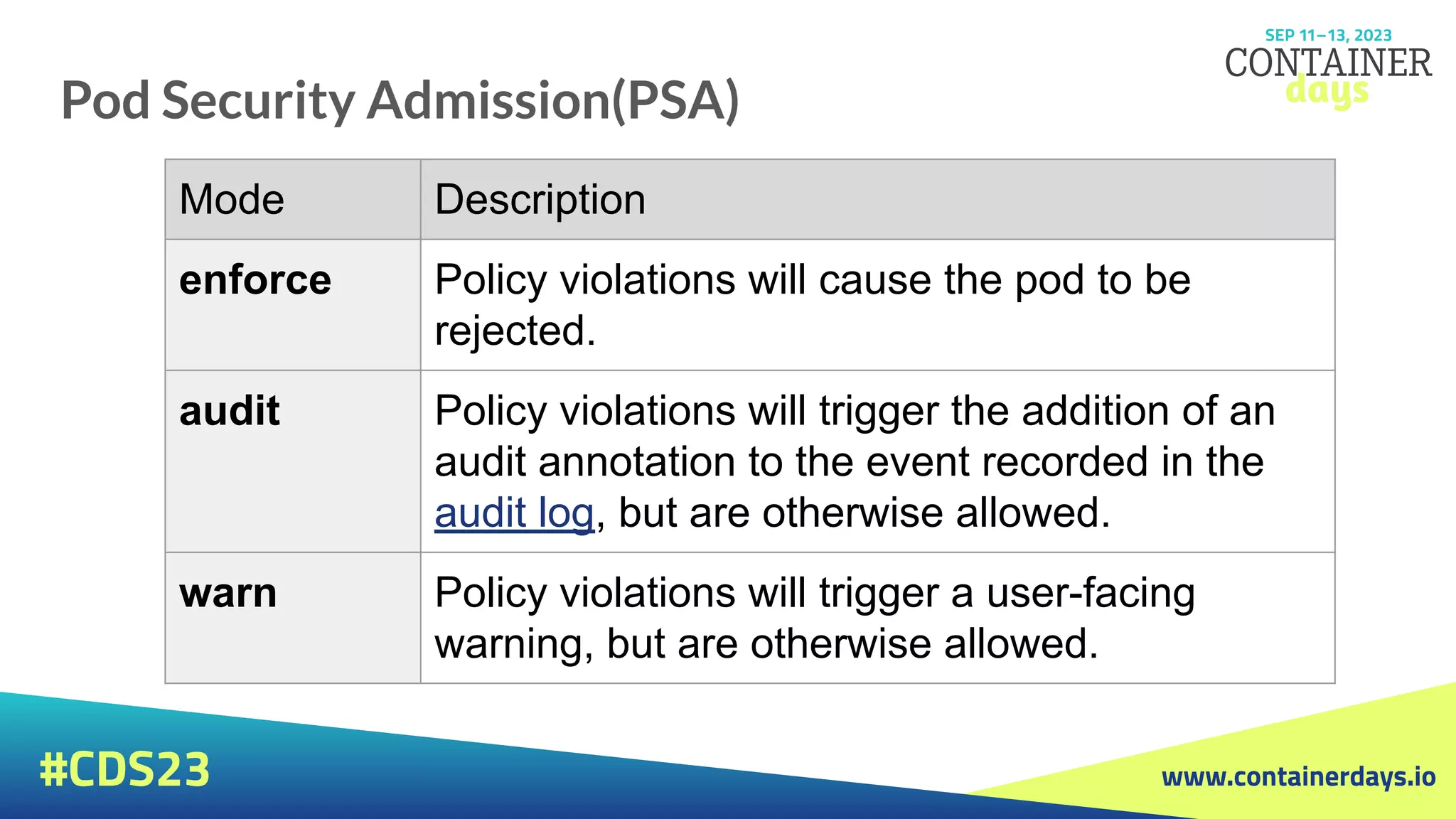
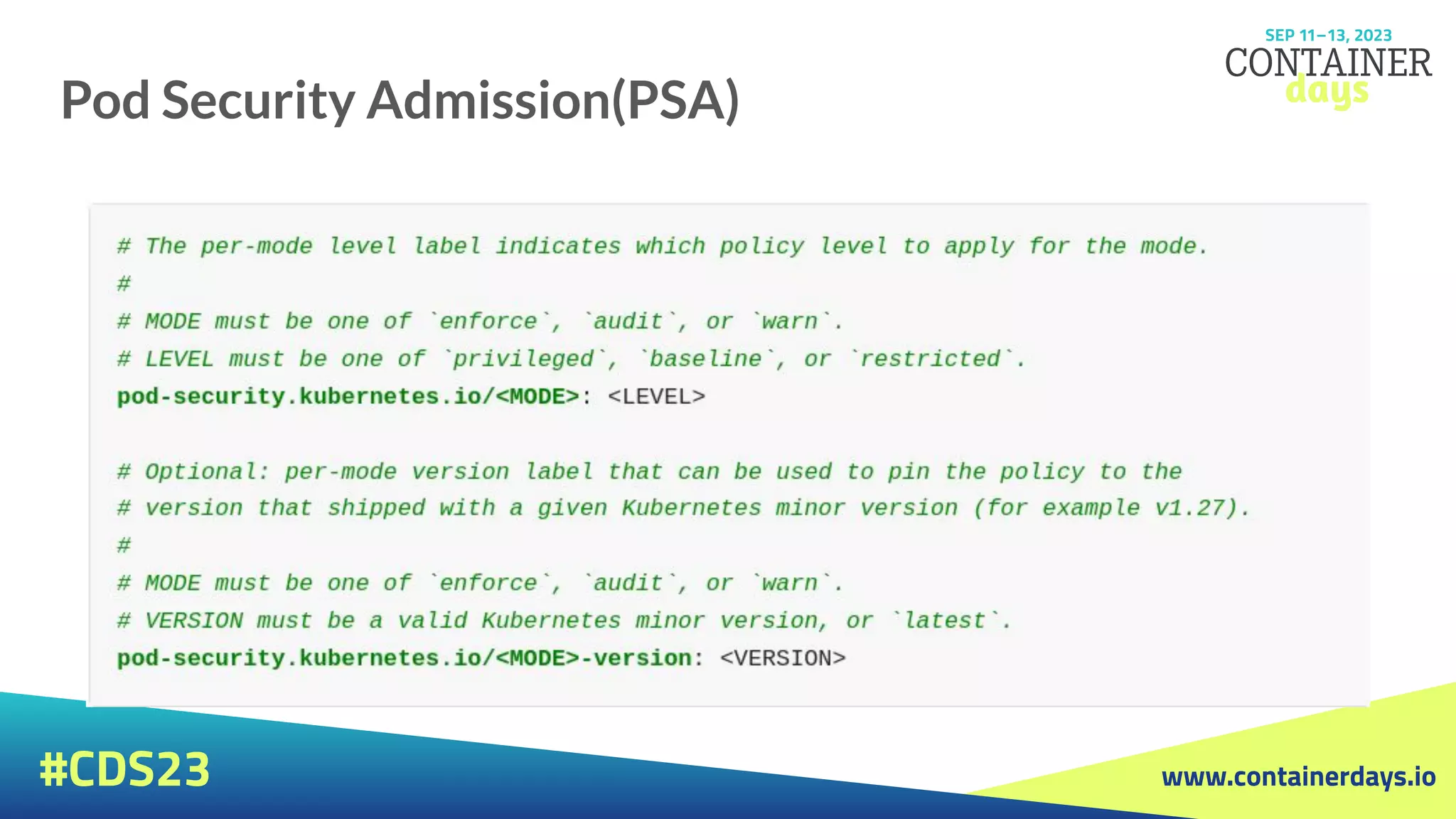
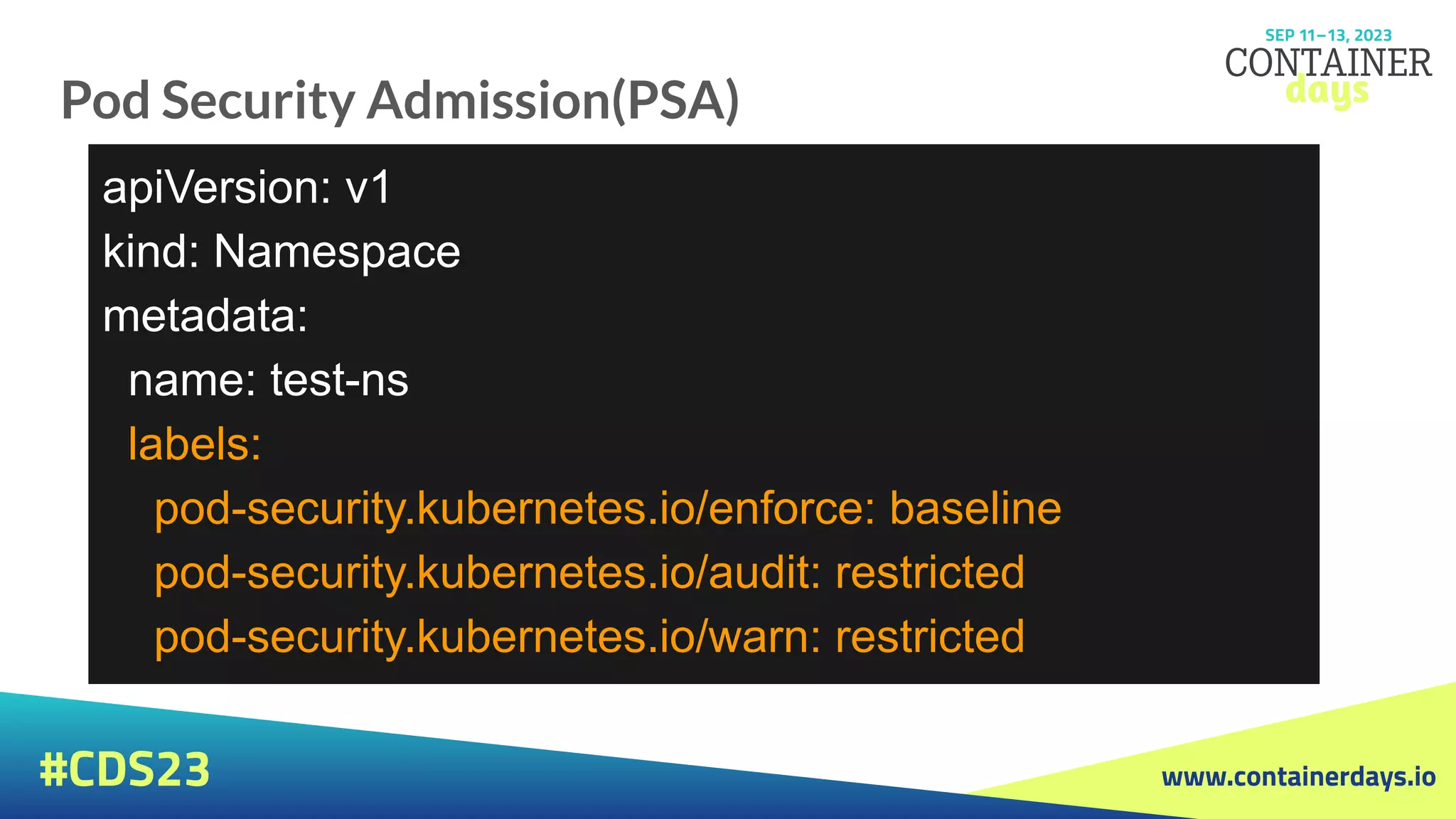
Pod Security Admission(PSA)
● Pod Security admission places requirements on a Pod's
Security Context and other related fields according to the
three levels defined by the Pod Security Standards:
privileged, baseline, and restricted.
● spec.containers[*].ports
● spec.volumes[*].hostPath
● spec.securityContext
● spec.containers[*].securityContext](https://image.slidesharecdn.com/evolutionofsecuritystrategiesink8senvironments-230913110220-0a55196f/75/Evolution-of-security-strategies-in-K8s-environments-pdf-15-2048.jpg)




![www.containerdays.io
#CDS23
Pod Security Admission(PSA)
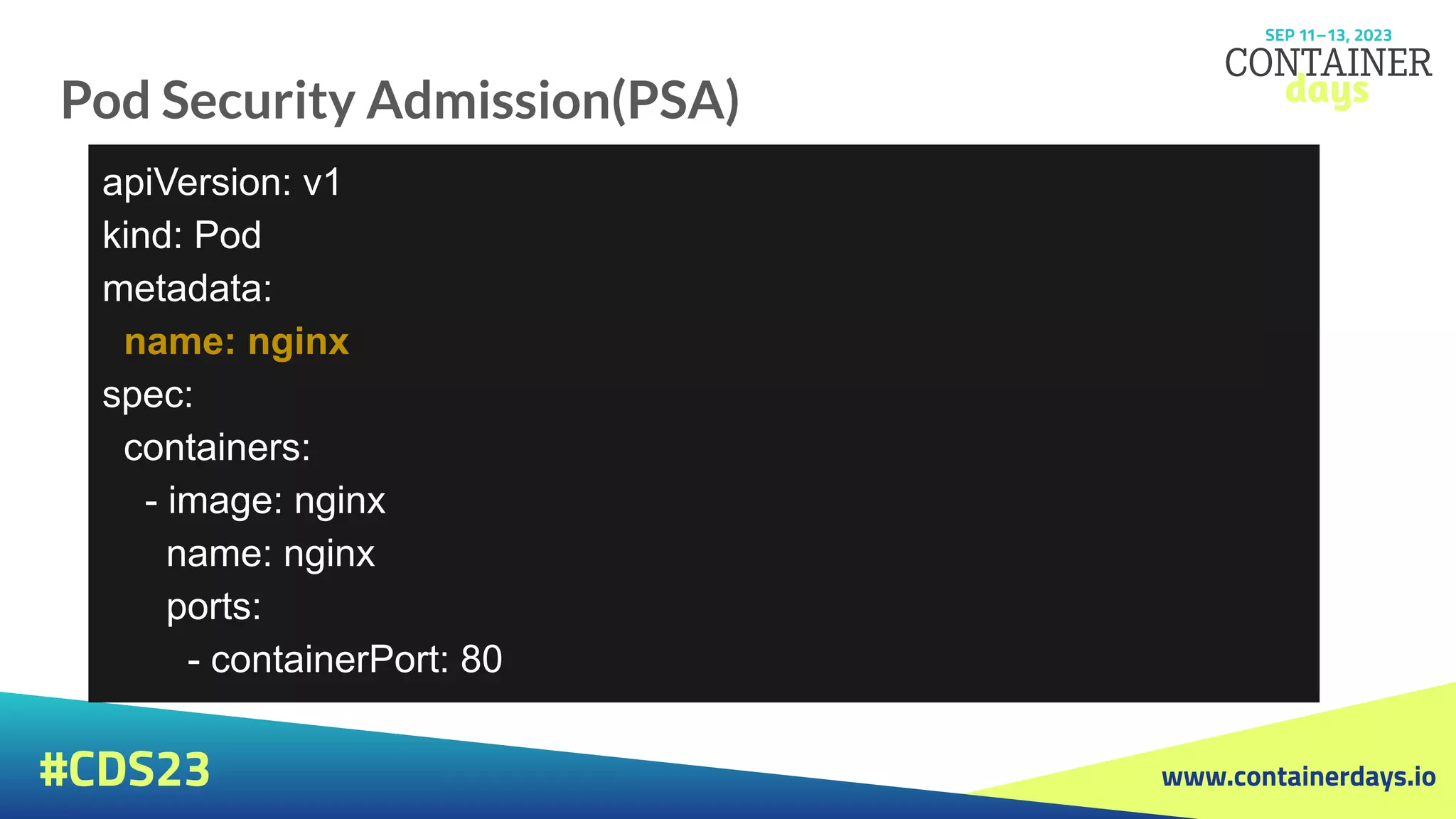
$ kubectl apply -f pod.yaml
Warning: would violate "latest" version of "restricted" PodSecurity profile:
allowPrivilegeEscalation != false (container "nginx" must set
securityContext.allowPrivilegeEscalation=false), unrestricted capabilities (container
"nginx" must set securityContext.capabilities.drop=["ALL"]), runAsNonRoot != true
(pod or container "nginx" must set securityContext.runAsNonRoot=true),
seccompProfile (pod or container "nginx" must set
securityContext.seccompProfile.type to "RuntimeDefault" or "Localhost")
pod/nginx created
$ kubectl get pods
NAME READY STATUS RESTARTS AGE
nginx 1/1 Running 0 6s](https://image.slidesharecdn.com/evolutionofsecuritystrategiesink8senvironments-230913110220-0a55196f/75/Evolution-of-security-strategies-in-K8s-environments-pdf-24-2048.jpg)
![www.containerdays.io
#CDS23
Pod Security Admission(PSA)
{"kind":"Event","apiVersion":"audit.k8s.io/v1","level":"Metadata","auditID":"808ca159-914c-43fa-
b4c8-dee5cb2fc440","stage":"ResponseComplete","requestURI":"/api/v1/namespaces/default/p
ods?fieldManager=kubectl-create","verb":"create","user":{"username":"kubernetes-admin","grou
ps":["system:masters","system:authenticated"]},"sourceIPs":["172.18.0.1"],"userAgent":"kubectl/
v1.22.0 (darwin/amd64)
kubernetes/c2b5237","objectRef":{"resource":"pods","namespace":"default","name":"nginx","api
Version":"v1"},"responseStatus":{"metadata":{},"code":201},"requestReceivedTimestamp":"2023
-08-21T03:30:26.605589Z","stageTimestamp":"2023-08-21T03:30:26.627123Z","annotations":{"
authorization.k8s.io/decision":"allow","authorization.k8s.io/reason":"","pod-security.kubernetes
.io/audit":"allowPrivilegeEscalation != false (container "nginx" must set
securityContext.allowPrivilegeEscalation=false), unrestricted capabilities (container "nginx"
must set securityContext.capabilities.drop=["ALL"]), runAsNonRoot != true (pod or container
"nginx" must set securityContext.runAsNonRoot=true), seccompProfile (pod or container
"nginx" must set securityContext.seccompProfile.type to "RuntimeDefault" or
"Localhost")"}}](https://image.slidesharecdn.com/evolutionofsecuritystrategiesink8senvironments-230913110220-0a55196f/75/Evolution-of-security-strategies-in-K8s-environments-pdf-25-2048.jpg)
![www.containerdays.io
#CDS23
Pod Security Admission(PSA)
apiVersion: apiserver.config.k8s.io/v1
kind: AdmissionConfiguration
plugins:
- name: PodSecurity
configuration:
apiVersion: pod-security.admission.config.k8s.io/v1alpha1
kind: PodSecurityConfiguration
defaults:
enforce: "baseline"
enforce-version: "latest"
audit: "restricted"
audit-version: "latest"
warn: "restricted"
warn-version: "latest"
exemptions:
usernames: []
runtimeClassNames: []
namespaces: [kube-system]](https://image.slidesharecdn.com/evolutionofsecuritystrategiesink8senvironments-230913110220-0a55196f/75/Evolution-of-security-strategies-in-K8s-environments-pdf-26-2048.jpg)